目录
需要做的事情
一、安装与配置文档
1、node.js安装与配置
2、VSCode安装
3、在VSCode中运行
二、JS常用算法
1、md5 线性散列算法
2、DES/AES对称加密算法
3、RSA 非对称加密算法
4、base64 伪加密算法
三、js逆向案例
1、有道笔记翻译(MD5)
进行js代码调试的流程
2、微信公众平台登录(MD5)
3、模拟凡客登录(MD5)
4、房天下( RSA)
5、模拟闪职登陆-RSA加密
需要做的事情
- 找到加密的字段
- 借助加密字段找到客户端(浏览器端)进行加密的代码(js调试,找到加密的位置)
- 运行加密代码(找到加密代码之后,要通过python执行js代码)
- 最后把加密之后的密码和其他参数一起提交到服务器(通过python代码实现)
一、安装与配置文档
1、node.js安装与配置
win10安装nodejs及配置cnpm详细教程_秋枫萧竹的博客-CSDN博客_nodejs配置cnpm一、安装环境二、开始安装三、验证安装四、修改全局模块下载路径(可选)五、更换npm源为淘宝镜像六、全局安装基于淘宝源的cnpm总结https://blog.csdn.net/qq_44697728/article/details/114276438?spm=1001.2101.3001.6650.6&utm_medium=distribute.pc_relevant.none-task-blog-2~default~BlogCommendFromBaidu~default-6.pc_relevant_default&depth_1-utm_source=distribute.pc_relevant.none-task-blog-
2、VSCode安装
VsCode下载与安装![]() https://www.cnblogs.com/csji/p/13558221.html
https://www.cnblogs.com/csji/p/13558221.html
3、在VSCode中运行
注意:
vscode不会自动默认保存(执行)修改之后的代码
如果需要自动保存->settings->把off改成onFocusChange
注如何无法运行js程序,安装code Runner插件即可
安装一个模块:
pip install PyExecJs -i https://pypi.douban.com/simple
另外:
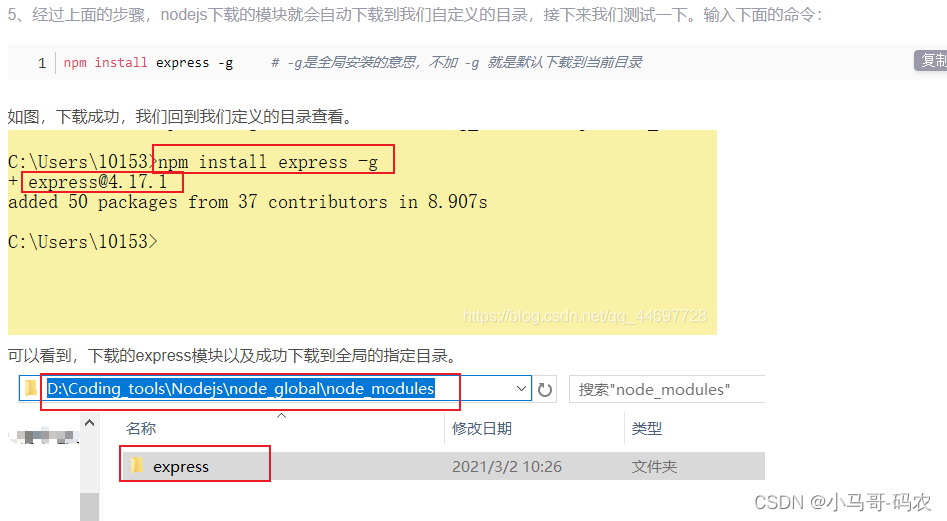
在运行npm install express -g 这一步的时候,一定要用管理员运行cmd才能安装成功。
这里还要注意一个地方,我碰到的情况是,在安装完node.js等一系列软件之后,execjs执行js报错 TypeError: 'console' 未定义,需要重新启动一下pycharm.
二、JS常用算法
1、md5 线性散列算法
为了提高密码的安全性,一般会在密码后面追加一个盐(如:时间戳)。
MD5是一种被广泛使用的线性散列算法,可以产出一个128位(16字节)的散列值(hash value),用于确保信息传输完整的一致性。且MD5加密之后产生的是一个固定长度(32位或16位)数据
https://cdn.bootcdn.net/ajax/libs/blueimp-md5/1.0.1/js/md5.js
2、DES/AES对称加密算法
1、DES对称加密,是一种比较传统的加密方式,其加密运算、解密运算使用的是同样的密钥,信息的发送者和信息的接收者在进行信息的传输与处理时,必须共同持有该密钥(称为对称密码),是一种对称加密算法
2、AES和DES的区别加密后密文长度不同:
DES加密后密文长度是8的整数倍,AES加密后密文的长度是16的整数倍
3、安全度不同
一般情况下DES足够安全,如果要求高可以使用AES,DES和AES切换只需要修改CryptoJS.DES =>CryptoJS.AES
3、RSA 非对称加密算法
RSA加密算法是一种非对称加密算法。在公开密钥加密和电子商业中RSA被广泛使用。
非对称加密需要2个密钥
- 公开密钥(publickey:公钥)
- 私有密钥(privatekey:私钥)
- 公钥和私钥是一对
base64加密算法
base64是一种用64个字符来表示任意二进制数据的方法。
base64使用 A--Z a--z 0--9 + / 这64个字符实现对数据的加密
4、base64 伪加密算法
三、js逆向案例
1、有道笔记翻译(MD5)
有道笔记翻译-MD5加密 · 语雀1、发送两次请求 第一次: i: 翻译 from: A...
总结:
1、通过加密码字段salt、sign额lts
2、通过加密字段定位到相关js代码 调试代码
3、通过python执行js代码(使用python执行之前,需要确保js代码是正确的)
4、携带参数发送请求
进行js代码调试的流程
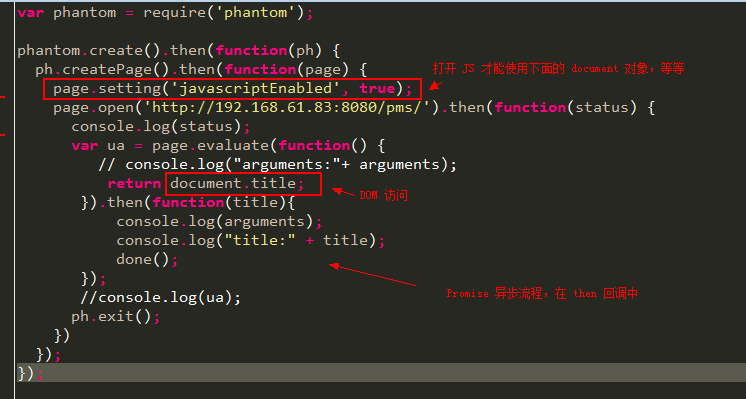
调试工具:灰色箭头是执行当前的下一条语句 蓝色三角形是跳到下一个断点处1、确定加密字段2、利用某个加密字段搜索:开发工具右上角有三个点-》选择search-》搜索点击搜索结果里面-》点击左下角的花括号进行格式化处理在当前文件里面用鼠标进行聚焦-》再次搜索加密字段找到可疑的加密字段打上断点进行调试借助花括号下面的下划线找到函数开始和结束的位置
2、微信公众平台登录(MD5)
通过查看请求调用栈,找到加密代码
- 抓包 确定加密字段
- 定位到加密的大致位置
- 打断点分析 确定加密的具体位置
- 拷贝js加密部分的代码 进行调试(vscode中进行的)
- 调试到js代码没有问题使用python执行js代码生成加密字段
- python代码
import requests
import execjs
from fake_useragent import UserAgent
def get_js(file_name,fun_name,fun_args = None):with open(file_name,'r',encoding='utf-8') as file:js_code = file.read()csj = execjs.compile(js_code)return csj.call(fun_name,fun_args)if __name__ == '__main__':username = '82232778@qq.com'password = 'aimama412304'data_dict = {}pwd = get_js('wechat.js','md5',password)data_dict['username'] = usernamedata_dict['pwd'] = pwddata_dict['imgcode'] = ''data_dict['f'] = 'json'data_dict['userlang'] = 'zh_CN'data_dict['redirect_url'] = ''data_dict['token'] = ''data_dict['lang'] = 'zh_CN'data_dict['ajax'] = 1header = {'cookie':'pgv_pvid=1606564294054066; RK=zOsAcrfhEZ; ptcz=4e31d0f9f461559f799a55923c2b76a83682e517c6552accf56b80830b89bea9; tvfe_boss_uuid=ed5f7109bdc6d8a5; ua_id=HK1ZbbA8NMNWqflhAAAAAMF02MKxhr1S7oOE1LMNtl8=; wxuin=65975220034367; mm_lang=zh_CN; logTrackKey=5cf4b4dc3ac54f0a83b521b0ab609c2b; o_cookie=824104778; _clck=3508202292|1|f6a|0; ts_uid=5328249324; _hjSessionUser_2765497=eyJpZCI6IjU1ZjgwMzIzLWE1YjQtNTM2ZS1iNDY1LWEyZTBiZTJmMWVjOSIsImNyZWF0ZWQiOjE2NjgwNDk3MTA2NDEsImV4aXN0aW5nIjpmYWxzZX0=; _ga=GA1.2.2108284859.1668049711; pac_uid=1_824104778; iip=0; _hp2_id.1405110977=%7B%22userId%22%3A%227829766777300571%22%2C%22pageviewId%22%3A%221289756376712607%22%2C%22sessionId%22%3A%22395270926496724%22%2C%22identity%22%3Anull%2C%22trackerVersion%22%3A%224.0%22%7D; xid=dacc3c34f2ed5e218861b31766e20b5c; cert=UHdf106vaBuswqlrmUZp9zHUuvEkc93n; uuid=517ae204db37da5cfd4232e25c93dcf7','Referer': 'https://mp.weixin.qq.com/','User-Agent': UserAgent().random}url = 'https://mp.weixin.qq.com/cgi-bin/bizlogin?action=startlogin'result = requests.post(url, data=data_dict, headers=header)print(result.json())- js代码
function l(e, t) {var n = (65535 & e) + (65535 & t);return (e >> 16) + (t >> 16) + (n >> 16) << 16 | 65535 & n
}
function a(e, t, n, o, r, i) {return l((t = l(l(t, e), l(o, i))) << r | t >>> 32 - r, n)
}
function p(e, t, n, o, r, i, s) {return a(t & n | ~t & o, e, t, r, i, s)
}
function f(e, t, n, o, r, i, s) {return a(t & o | n & ~o, e, t, r, i, s)
}
function m(e, t, n, o, r, i, s) {return a(t ^ n ^ o, e, t, r, i, s)
}
function g(e, t, n, o, r, i, s) {return a(n ^ (t | ~o), e, t, r, i, s)
}
function s(e, t) {e[t >> 5] |= 128 << t % 32,e[14 + (t + 64 >>> 9 << 4)] = t;for (var n, o, r, d, i = 1732584193, s = -271733879, a = -1732584194, c = 271733878, u = 0; u < e.length; u += 16)i = p(n = i, o = s, r = a, d = c, e[u], 7, -680876936),c = p(c, i, s, a, e[u + 1], 12, -389564586),a = p(a, c, i, s, e[u + 2], 17, 606105819),s = p(s, a, c, i, e[u + 3], 22, -1044525330),i = p(i, s, a, c, e[u + 4], 7, -176418897),c = p(c, i, s, a, e[u + 5], 12, 1200080426),a = p(a, c, i, s, e[u + 6], 17, -1473231341),s = p(s, a, c, i, e[u + 7], 22, -45705983),i = p(i, s, a, c, e[u + 8], 7, 1770035416),c = p(c, i, s, a, e[u + 9], 12, -1958414417),a = p(a, c, i, s, e[u + 10], 17, -42063),s = p(s, a, c, i, e[u + 11], 22, -1990404162),i = p(i, s, a, c, e[u + 12], 7, 1804603682),c = p(c, i, s, a, e[u + 13], 12, -40341101),a = p(a, c, i, s, e[u + 14], 17, -1502002290),i = f(i, s = p(s, a, c, i, e[u + 15], 22, 1236535329), a, c, e[u + 1], 5, -165796510),c = f(c, i, s, a, e[u + 6], 9, -1069501632),a = f(a, c, i, s, e[u + 11], 14, 643717713),s = f(s, a, c, i, e[u], 20, -373897302),i = f(i, s, a, c, e[u + 5], 5, -701558691),c = f(c, i, s, a, e[u + 10], 9, 38016083),a = f(a, c, i, s, e[u + 15], 14, -660478335),s = f(s, a, c, i, e[u + 4], 20, -405537848),i = f(i, s, a, c, e[u + 9], 5, 568446438),c = f(c, i, s, a, e[u + 14], 9, -1019803690),a = f(a, c, i, s, e[u + 3], 14, -187363961),s = f(s, a, c, i, e[u + 8], 20, 1163531501),i = f(i, s, a, c, e[u + 13], 5, -1444681467),c = f(c, i, s, a, e[u + 2], 9, -51403784),a = f(a, c, i, s, e[u + 7], 14, 1735328473),i = m(i, s = f(s, a, c, i, e[u + 12], 20, -1926607734), a, c, e[u + 5], 4, -378558),c = m(c, i, s, a, e[u + 8], 11, -2022574463),a = m(a, c, i, s, e[u + 11], 16, 1839030562),s = m(s, a, c, i, e[u + 14], 23, -35309556),i = m(i, s, a, c, e[u + 1], 4, -1530992060),c = m(c, i, s, a, e[u + 4], 11, 1272893353),a = m(a, c, i, s, e[u + 7], 16, -155497632),s = m(s, a, c, i, e[u + 10], 23, -1094730640),i = m(i, s, a, c, e[u + 13], 4, 681279174),c = m(c, i, s, a, e[u], 11, -358537222),a = m(a, c, i, s, e[u + 3], 16, -722521979),s = m(s, a, c, i, e[u + 6], 23, 76029189),i = m(i, s, a, c, e[u + 9], 4, -640364487),c = m(c, i, s, a, e[u + 12], 11, -421815835),a = m(a, c, i, s, e[u + 15], 16, 530742520),i = g(i, s = m(s, a, c, i, e[u + 2], 23, -995338651), a, c, e[u], 6, -198630844),c = g(c, i, s, a, e[u + 7], 10, 1126891415),a = g(a, c, i, s, e[u + 14], 15, -1416354905),s = g(s, a, c, i, e[u + 5], 21, -57434055),i = g(i, s, a, c, e[u + 12], 6, 1700485571),c = g(c, i, s, a, e[u + 3], 10, -1894986606),a = g(a, c, i, s, e[u + 10], 15, -1051523),s = g(s, a, c, i, e[u + 1], 21, -2054922799),i = g(i, s, a, c, e[u + 8], 6, 1873313359),c = g(c, i, s, a, e[u + 15], 10, -30611744),a = g(a, c, i, s, e[u + 6], 15, -1560198380),s = g(s, a, c, i, e[u + 13], 21, 1309151649),i = g(i, s, a, c, e[u + 4], 6, -145523070),c = g(c, i, s, a, e[u + 11], 10, -1120210379),a = g(a, c, i, s, e[u + 2], 15, 718787259),s = g(s, a, c, i, e[u + 9], 21, -343485551),i = l(i, n),s = l(s, o),a = l(a, r),c = l(c, d);return [i, s, a, c]
}
function c(e) {for (var t = "", n = 0; n < 32 * e.length; n += 8)t += String.fromCharCode(e[n >> 5] >>> n % 32 & 255);return t
}
function u(e) {var t, n = [];for (n[(e.length >> 2) - 1] = void 0,t = 0; t < n.length; t += 1)n[t] = 0;for (t = 0; t < 8 * e.length; t += 8)n[t >> 5] |= (255 & e.charCodeAt(t / 8)) << t % 32;return n
}
function o(e) {for (var t, n = "0123456789abcdef", o = "", r = 0; r < e.length; r += 1)t = e.charCodeAt(r),o += n.charAt(t >>> 4 & 15) + n.charAt(15 & t);return o
}
function d(e) {return unescape(encodeURIComponent(e))
}
function r(e) {return c(s(u(e = d(e)), 8 * e.length))
}
function i(e, t) {var n, e = d(e), t = d(t), o = u(e), r = [], i = [];for (r[15] = i[15] = void 0,16 < o.length && (o = s(o, 8 * e.length)),n = 0; n < 16; n += 1)r[n] = 909522486 ^ o[n],i[n] = 1549556828 ^ o[n];return e = s(r.concat(u(t)), 512 + 8 * t.length),c(s(i.concat(e), 640))
}// e 为原始密码
function md5(e,t,n) {return t ? n ? i(t, e) : o(i(t, e)) : n ? r(e) : o(r(e))
}3、模拟凡客登录(MD5)
- python代码
import requests
import execjs
from fake_useragent import UserAgent
url = 'https://i.fkw.com/ajax/login_h.jsp?dogSrc=3'
headers = {'User-Agent':UserAgent().random,'Cookie':'_faiHeDistictId=18443f9af272e3c2; _cliid=AqLXwGi1sFotrNYL; loginComeForm=fkjz; first_ta=3; _ta=3; _tp=-; _newUnion=0; _kw=0; _vid_url=https%3A%2F%2Fi.fkw.com%2F%3F_ta%3D3; _s_pro=i.fkw.com%2F; _c_pro=i.fkw.com%2F; reg_sid=0; wxRegBiz=none; _FSESSIONID=; loginSign=','Referer':'https://i.fkw.com/?_ta=3'
}
def get_js(file_name,fun_name,fun_args):# 1、读取js文件with open(file_name, 'r', encoding='utf-8') as file_obj:js_code = file_obj.read()# 2、编译js文件cjs = execjs.compile(js_code)# 3、 执行js代码return cjs.call(fun_name, fun_args)password = '123456'
data = {"cacct": "18735109041","pwd": get_js('./fanke.js','md5',password),"autoLogin": "false","staffLogin": "false","bizType": 5,"dogId": 0,"fromsite":"false","cmd": "loginCorpNews","vc_type": 2,"checkSign": "AgpMTDZKZzhjNHZCCg8xODMuMTI4LjIyMi4xNjAQARoGMTY1MTM3","fallbacked":"false",
}
response = requests.post(url,headers=headers,data=data)
print(response.json())
- js代码
function o(u, z) {var w = (u & 65535) + (z & 65535), v = (u >> 16) + (z >> 16) + (w >> 16);return (v << 16) | (w & 65535)
}
function s(u, v) {return (u << v) | (u >>> (32 - v))
}
function c(A, w, v, u, z, y) {return o(s(o(o(w, A), o(u, y)), z), v)
}
function b(w, v, B, A, u, z, y) {return c((v & B) | ((~v) & A), w, v, u, z, y)
}
function i(w, v, B, A, u, z, y) {return c((v & A) | (B & (~A)), w, v, u, z, y)
}
function n(w, v, B, A, u, z, y) {return c(v ^ B ^ A, w, v, u, z, y)
}
function a(w, v, B, A, u, z, y) {return c(B ^ (v | (~A)), w, v, u, z, y)
}
function d(F, A) {F[A >> 5] |= 128 << ((A) % 32);F[(((A + 64) >>> 9) << 4) + 14] = A;var w, z, y, v, u, E = 1732584193, D = -271733879, C = -1732584194, B = 271733878;for (w = 0; w < F.length; w += 16) {z = E;y = D;v = C;u = B;E = b(E, D, C, B, F[w], 7, -680876936);B = b(B, E, D, C, F[w + 1], 12, -389564586);C = b(C, B, E, D, F[w + 2], 17, 606105819);D = b(D, C, B, E, F[w + 3], 22, -1044525330);E = b(E, D, C, B, F[w + 4], 7, -176418897);B = b(B, E, D, C, F[w + 5], 12, 1200080426);C = b(C, B, E, D, F[w + 6], 17, -1473231341);D = b(D, C, B, E, F[w + 7], 22, -45705983);E = b(E, D, C, B, F[w + 8], 7, 1770035416);B = b(B, E, D, C, F[w + 9], 12, -1958414417);C = b(C, B, E, D, F[w + 10], 17, -42063);D = b(D, C, B, E, F[w + 11], 22, -1990404162);E = b(E, D, C, B, F[w + 12], 7, 1804603682);B = b(B, E, D, C, F[w + 13], 12, -40341101);C = b(C, B, E, D, F[w + 14], 17, -1502002290);D = b(D, C, B, E, F[w + 15], 22, 1236535329);E = i(E, D, C, B, F[w + 1], 5, -165796510);B = i(B, E, D, C, F[w + 6], 9, -1069501632);C = i(C, B, E, D, F[w + 11], 14, 643717713);D = i(D, C, B, E, F[w], 20, -373897302);E = i(E, D, C, B, F[w + 5], 5, -701558691);B = i(B, E, D, C, F[w + 10], 9, 38016083);C = i(C, B, E, D, F[w + 15], 14, -660478335);D = i(D, C, B, E, F[w + 4], 20, -405537848);E = i(E, D, C, B, F[w + 9], 5, 568446438);B = i(B, E, D, C, F[w + 14], 9, -1019803690);C = i(C, B, E, D, F[w + 3], 14, -187363961);D = i(D, C, B, E, F[w + 8], 20, 1163531501);E = i(E, D, C, B, F[w + 13], 5, -1444681467);B = i(B, E, D, C, F[w + 2], 9, -51403784);C = i(C, B, E, D, F[w + 7], 14, 1735328473);D = i(D, C, B, E, F[w + 12], 20, -1926607734);E = n(E, D, C, B, F[w + 5], 4, -378558);B = n(B, E, D, C, F[w + 8], 11, -2022574463);C = n(C, B, E, D, F[w + 11], 16, 1839030562);D = n(D, C, B, E, F[w + 14], 23, -35309556);E = n(E, D, C, B, F[w + 1], 4, -1530992060);B = n(B, E, D, C, F[w + 4], 11, 1272893353);C = n(C, B, E, D, F[w + 7], 16, -155497632);D = n(D, C, B, E, F[w + 10], 23, -1094730640);E = n(E, D, C, B, F[w + 13], 4, 681279174);B = n(B, E, D, C, F[w], 11, -358537222);C = n(C, B, E, D, F[w + 3], 16, -722521979);D = n(D, C, B, E, F[w + 6], 23, 76029189);E = n(E, D, C, B, F[w + 9], 4, -640364487);B = n(B, E, D, C, F[w + 12], 11, -421815835);C = n(C, B, E, D, F[w + 15], 16, 530742520);D = n(D, C, B, E, F[w + 2], 23, -995338651);E = a(E, D, C, B, F[w], 6, -198630844);B = a(B, E, D, C, F[w + 7], 10, 1126891415);C = a(C, B, E, D, F[w + 14], 15, -1416354905);D = a(D, C, B, E, F[w + 5], 21, -57434055);E = a(E, D, C, B, F[w + 12], 6, 1700485571);B = a(B, E, D, C, F[w + 3], 10, -1894986606);C = a(C, B, E, D, F[w + 10], 15, -1051523);D = a(D, C, B, E, F[w + 1], 21, -2054922799);E = a(E, D, C, B, F[w + 8], 6, 1873313359);B = a(B, E, D, C, F[w + 15], 10, -30611744);C = a(C, B, E, D, F[w + 6], 15, -1560198380);D = a(D, C, B, E, F[w + 13], 21, 1309151649);E = a(E, D, C, B, F[w + 4], 6, -145523070);B = a(B, E, D, C, F[w + 11], 10, -1120210379);C = a(C, B, E, D, F[w + 2], 15, 718787259);D = a(D, C, B, E, F[w + 9], 21, -343485551);E = o(E, z);D = o(D, y);C = o(C, v);B = o(B, u)}return [E, D, C, B]
}
function p(v) {var w, u = "";for (w = 0; w < v.length * 32; w += 8) {u += String.fromCharCode((v[w >> 5] >>> (w % 32)) & 255)}return u
}
function j(v) {var w, u = [];u[(v.length >> 2) - 1] = undefined;for (w = 0; w < u.length; w += 1) {u[w] = 0}for (w = 0; w < v.length * 8; w += 8) {u[w >> 5] |= (v.charCodeAt(w / 8) & 255) << (w % 32)}return u
}
function k(u) {return p(d(j(u), u.length * 8))
}
function f(w, z) {var v, y = j(w), u = [], x = [], A;u[15] = x[15] = undefined;if (y.length > 16) {y = d(y, w.length * 8)}for (v = 0; v < 16; v += 1) {u[v] = y[v] ^ 909522486;x[v] = y[v] ^ 1549556828}A = d(u.concat(j(z)), 512 + z.length * 8);return p(d(x.concat(A), 512 + 128))
}
function t(w) {var z = "0123456789abcdef", v = "", u, y;for (y = 0; y < w.length; y += 1) {u = w.charCodeAt(y);v += z.charAt((u >>> 4) & 15) + z.charAt(u & 15)}return v
}
function m(u) {return unescape(encodeURIComponent(u))
}
function q(u) {return k(m(u))
}
function l(u) {return t(q(u))
}
function h(u, v) {return f(m(u), m(v))
}
function r(u, v) {return t(h(u, v))
}function md5(v, w, u) {if (!w) {if (!u) {return l(v)} else {return q(v)}}if (!u) {return r(w, v)} else {return h(w, v)}
}4、房天下( RSA)
在js中看到encrypt格外注意
- 抓包 确定了加密字段 pwd
- 找到加密的大致位置
- 打上断点 确定加密的具体 找到需要出阿迪的参数 开始在vscode中调试
- 通过python执行js代码
- python代码
import requests
import execjs
from fake_useragent import UserAgent
url = 'https://passport.fang.com/login.api'
# 获取加密后的密码
def get_pwd(file_name,fun_name,fun_args):with open(file_name,'r',encoding='utf-8') as file:js_code = file.read()js = execjs.compile(js_code)return js.call(fun_name,fun_args)
data = {"uid":"18735109041","pwd": get_pwd('./fang.js','encryptedString','412304'),"Service": "soufun-passport-web","AutoLogin": 1
}
headers = {'User-Agent':UserAgent().random,'Referer':'https://passport.fang.com/'
}
response = requests.post(url,headers=headers,data=data)
print(response.json())- js代码
function setMaxDigits(n) {maxDigits = n;ZERO_ARRAY = new Array(maxDigits);for (var t = 0; t < ZERO_ARRAY.length; t++)ZERO_ARRAY[t] = 0;bigZero = new BigInt;bigOne = new BigInt;bigOne.digits[0] = 1
}
function BigInt(n) {this.digits = typeof n == "boolean" && n == !0 ? null : ZERO_ARRAY.slice(0);this.isNeg = !1
}
function biFromDecimal(n) {for (var u = n.charAt(0) == "-", t = u ? 1 : 0, i, f, r; t < n.length && n.charAt(t) == "0"; )++t;if (t == n.length)i = new BigInt;else {for (f = n.length - t,r = f % dpl10,r == 0 && (r = dpl10),i = biFromNumber(Number(n.substr(t, r))),t += r; t < n.length; )i = biAdd(biMultiply(i, lr10), biFromNumber(Number(n.substr(t, dpl10)))),t += dpl10;i.isNeg = u}return i
}
function biCopy(n) {var t = new BigInt(!0);return t.digits = n.digits.slice(0),t.isNeg = n.isNeg,t
}
function biFromNumber(n) {var t = new BigInt, i;for (t.isNeg = n < 0,n = Math.abs(n),i = 0; n > 0; )t.digits[i++] = n & maxDigitVal,n = Math.floor(n / biRadix);return t
}
function reverseStr(n) {for (var i = "", t = n.length - 1; t > -1; --t)i += n.charAt(t);return i
}
function biToString(n, t) {var r = new BigInt, i, u;for (r.digits[0] = t,i = biDivideModulo(n, r),u = hexatrigesimalToChar[i[1].digits[0]]; biCompare(i[0], bigZero) == 1; )i = biDivideModulo(i[0], r),digit = i[1].digits[0],u += hexatrigesimalToChar[i[1].digits[0]];return (n.isNeg ? "-" : "") + reverseStr(u)
}
function biToDecimal(n) {var i = new BigInt, t, r;for (i.digits[0] = 10,t = biDivideModulo(n, i),r = String(t[1].digits[0]); biCompare(t[0], bigZero) == 1; )t = biDivideModulo(t[0], i),r += String(t[1].digits[0]);return (n.isNeg ? "-" : "") + reverseStr(r)
}
function digitToHex(n) {var t = "";for (i = 0; i < 4; ++i)t += hexToChar[n & 15],n >>>= 4;return reverseStr(t)
}
function biToHex(n) {for (var i = "", r = biHighIndex(n), t = biHighIndex(n); t > -1; --t)i += digitToHex(n.digits[t]);return i
}
function charToHex(n) {var t = 48, u = t + 9, i = 97, f = i + 25, r = 65;return n >= t && n <= u ? n - t : n >= r && n <= 90 ? 10 + n - r : n >= i && n <= f ? 10 + n - i : 0
}
function hexToDigit(n) {for (var t = 0, r = Math.min(n.length, 4), i = 0; i < r; ++i)t <<= 4,t |= charToHex(n.charCodeAt(i));return t
}
function biFromHex(n) {for (var i = new BigInt, u = n.length, t = u, r = 0; t > 0; t -= 4,++r)i.digits[r] = hexToDigit(n.substr(Math.max(t - 4, 0), Math.min(t, 4)));return i
}
function biFromString(n, t) {var f = n.charAt(0) == "-", e = f ? 1 : 0, i = new BigInt, r = new BigInt, u;for (r.digits[0] = 1,u = n.length - 1; u >= e; u--) {var o = n.charCodeAt(u), s = charToHex(o), h = biMultiplyDigit(r, s);i = biAdd(i, h);r = biMultiplyDigit(r, t)}return i.isNeg = f,i
}
function biDump(n) {return (n.isNeg ? "-" : "") + n.digits.join(" ")
}
function biAdd(n, t) {var r, u, f, i;if (n.isNeg != t.isNeg)t.isNeg = !t.isNeg,r = biSubtract(n, t),t.isNeg = !t.isNeg;else {for (r = new BigInt,u = 0,i = 0; i < n.digits.length; ++i)f = n.digits[i] + t.digits[i] + u,r.digits[i] = f % biRadix,u = Number(f >= biRadix);r.isNeg = n.isNeg}return r
}
function biSubtract(n, t) {var r, f, u, i;if (n.isNeg != t.isNeg)t.isNeg = !t.isNeg,r = biAdd(n, t),t.isNeg = !t.isNeg;else {for (r = new BigInt,u = 0,i = 0; i < n.digits.length; ++i)f = n.digits[i] - t.digits[i] + u,r.digits[i] = f % biRadix,r.digits[i] < 0 && (r.digits[i] += biRadix),u = 0 - Number(f < 0);if (u == -1) {for (u = 0,i = 0; i < n.digits.length; ++i)f = 0 - r.digits[i] + u,r.digits[i] = f % biRadix,r.digits[i] < 0 && (r.digits[i] += biRadix),u = 0 - Number(f < 0);r.isNeg = !n.isNeg} elser.isNeg = n.isNeg}return r
}
function biHighIndex(n) {for (var t = n.digits.length - 1; t > 0 && n.digits[t] == 0; )--t;return t
}
function biNumBits(n) {for (var i = biHighIndex(n), r = n.digits[i], u = (i + 1) * bitsPerDigit, t = u; t > u - bitsPerDigit; --t) {if ((r & 32768) != 0)break;r <<= 1}return t
}
function biMultiply(n, t) {for (var i = new BigInt, u, o = biHighIndex(n), s = biHighIndex(t), e, f, r = 0; r <= s; ++r) {for (u = 0,f = r,j = 0; j <= o; ++j,++f)e = i.digits[f] + n.digits[j] * t.digits[r] + u,i.digits[f] = e & maxDigitVal,u = e >>> biRadixBits;i.digits[r + o + 1] = u}return i.isNeg = n.isNeg != t.isNeg,i
}
function biMultiplyDigit(n, t) {var u, r, f, i;for (result = new BigInt,u = biHighIndex(n),r = 0,i = 0; i <= u; ++i)f = result.digits[i] + n.digits[i] * t + r,result.digits[i] = f & maxDigitVal,r = f >>> biRadixBits;return result.digits[1 + u] = r,result
}
function arrayCopy(n, t, i, r, u) {for (var o = Math.min(t + u, n.length), f = t, e = r; f < o; ++f,++e)i[e] = n[f]
}
function biShiftLeft(n, t) {var e = Math.floor(t / bitsPerDigit), i = new BigInt, u, o, r, f;for (arrayCopy(n.digits, 0, i.digits, e, i.digits.length - e),u = t % bitsPerDigit,o = bitsPerDigit - u,r = i.digits.length - 1,f = r - 1; r > 0; --r,--f)i.digits[r] = i.digits[r] << u & maxDigitVal | (i.digits[f] & highBitMasks[u]) >>> o;return i.digits[0] = i.digits[r] << u & maxDigitVal,i.isNeg = n.isNeg,i
}
function biShiftRight(n, t) {var e = Math.floor(t / bitsPerDigit), i = new BigInt, u, o, r, f;for (arrayCopy(n.digits, e, i.digits, 0, n.digits.length - e),u = t % bitsPerDigit,o = bitsPerDigit - u,r = 0,f = r + 1; r < i.digits.length - 1; ++r,++f)i.digits[r] = i.digits[r] >>> u | (i.digits[f] & lowBitMasks[u]) << o;return i.digits[i.digits.length - 1] >>>= u,i.isNeg = n.isNeg,i
}
function biMultiplyByRadixPower(n, t) {var i = new BigInt;return arrayCopy(n.digits, 0, i.digits, t, i.digits.length - t),i
}
function biDivideByRadixPower(n, t) {var i = new BigInt;return arrayCopy(n.digits, t, i.digits, 0, i.digits.length - t),i
}
function biModuloByRadixPower(n, t) {var i = new BigInt;return arrayCopy(n.digits, 0, i.digits, 0, t),i
}
function biCompare(n, t) {if (n.isNeg != t.isNeg)return 1 - 2 * Number(n.isNeg);for (var i = n.digits.length - 1; i >= 0; --i)if (n.digits[i] != t.digits[i])return n.isNeg ? 1 - 2 * Number(n.digits[i] > t.digits[i]) : 1 - 2 * Number(n.digits[i] < t.digits[i]);return 0
}
function biDivideModulo(n, t) {var a = biNumBits(n), s = biNumBits(t), v = t.isNeg, r, i, u, e, h, o, f, y, p;if (a < s)return n.isNeg ? (r = biCopy(bigOne),r.isNeg = !t.isNeg,n.isNeg = !1,t.isNeg = !1,i = biSubtract(t, n),n.isNeg = !0,t.isNeg = v) : (r = new BigInt,i = biCopy(n)),[r, i];for (r = new BigInt,i = n,u = Math.ceil(s / bitsPerDigit) - 1,e = 0; t.digits[u] < biHalfRadix; )t = biShiftLeft(t, 1),++e,++s,u = Math.ceil(s / bitsPerDigit) - 1;for (i = biShiftLeft(i, e),a += e,h = Math.ceil(a / bitsPerDigit) - 1,o = biMultiplyByRadixPower(t, h - u); biCompare(i, o) != -1; )++r.digits[h - u],i = biSubtract(i, o);for (f = h; f > u; --f) {var c = f >= i.digits.length ? 0 : i.digits[f], w = f - 1 >= i.digits.length ? 0 : i.digits[f - 1], b = f - 2 >= i.digits.length ? 0 : i.digits[f - 2], l = u >= t.digits.length ? 0 : t.digits[u], k = u - 1 >= t.digits.length ? 0 : t.digits[u - 1];for (r.digits[f - u - 1] = c == l ? maxDigitVal : Math.floor((c * biRadix + w) / l),y = r.digits[f - u - 1] * (l * biRadix + k),p = c * biRadixSquared + (w * biRadix + b); y > p; )--r.digits[f - u - 1],y = r.digits[f - u - 1] * (l * biRadix | k),p = c * biRadix * biRadix + (w * biRadix + b);o = biMultiplyByRadixPower(t, f - u - 1);i = biSubtract(i, biMultiplyDigit(o, r.digits[f - u - 1]));i.isNeg && (i = biAdd(i, o),--r.digits[f - u - 1])}return i = biShiftRight(i, e),r.isNeg = n.isNeg != v,n.isNeg && (r = v ? biAdd(r, bigOne) : biSubtract(r, bigOne),t = biShiftRight(t, e),i = biSubtract(t, i)),i.digits[0] == 0 && biHighIndex(i) == 0 && (i.isNeg = !1),[r, i]
}
function biDivide(n, t) {return biDivideModulo(n, t)[0]
}
function biModulo(n, t) {return biDivideModulo(n, t)[1]
}
function biMultiplyMod(n, t, i) {return biModulo(biMultiply(n, t), i)
}
function biPow(n, t) {for (var r = bigOne, i = n; ; ) {if ((t & 1) != 0 && (r = biMultiply(r, i)),t >>= 1,t == 0)break;i = biMultiply(i, i)}return r
}
function biPowMod(n, t, i) {for (var f = bigOne, u = n, r = t; ; ) {if ((r.digits[0] & 1) != 0 && (f = biMultiplyMod(f, u, i)),r = biShiftRight(r, 1),r.digits[0] == 0 && biHighIndex(r) == 0)break;u = biMultiplyMod(u, u, i)}return f
}
function BarrettMu(n) {this.modulus = biCopy(n);this.k = biHighIndex(this.modulus) + 1;var t = new BigInt;t.digits[2 * this.k] = 1;this.mu = biDivide(t, this.modulus);this.bkplus1 = new BigInt;this.bkplus1.digits[this.k + 1] = 1;this.modulo = BarrettMu_modulo;this.multiplyMod = BarrettMu_multiplyMod;this.powMod = BarrettMu_powMod
}
function BarrettMu_modulo(n) {var r = biDivideByRadixPower(n, this.k - 1), u = biMultiply(r, this.mu), f = biDivideByRadixPower(u, this.k + 1), e = biModuloByRadixPower(n, this.k + 1), o = biMultiply(f, this.modulus), s = biModuloByRadixPower(o, this.k + 1), t = biSubtract(e, s), i;for (t.isNeg && (t = biAdd(t, this.bkplus1)),i = biCompare(t, this.modulus) >= 0; i; )t = biSubtract(t, this.modulus),i = biCompare(t, this.modulus) >= 0;return t
}
function BarrettMu_multiplyMod(n, t) {var i = biMultiply(n, t);return this.modulo(i)
}
function BarrettMu_powMod(n, t) {var u = new BigInt, r, i;for (u.digits[0] = 1,r = n,i = t; ; ) {if ((i.digits[0] & 1) != 0 && (u = this.multiplyMod(u, r)),i = biShiftRight(i, 1),i.digits[0] == 0 && biHighIndex(i) == 0)break;r = this.multiplyMod(r, r)}return u
}
function RSAKeyPair(n, t, i) {this.e = biFromHex(n);this.d = biFromHex(t);this.m = biFromHex(i);this.digitSize = 2 * biHighIndex(this.m) + 2;this.chunkSize = this.digitSize - 11;this.radix = 16;this.barrett = new BarrettMu(this.m)
}
function twoDigit(n) {return (n < 10 ? "0" : "") + String(n)
}
function encryptedString(t) {var n = new RSAKeyPair("010001", "", "978C0A92D2173439707498F0944AA476B1B62595877DD6FA87F6E2AC6DCB3D0BF0B82857439C99B5091192BC134889DFF60C562EC54EFBA4FF2F9D55ADBCCEA4A2FBA80CB398ED501280A007C83AF30C3D1A142D6133C63012B90AB26AC60C898FB66EDC3192C3EC4FF66925A64003B72496099F4F09A9FB72A2CF9E4D770C41");var e, o, s, h, c, i, f, u, v, l, y;if (n.chunkSize > n.digitSize - 11)return "Error";for (var a = [], p = t.length, r = 0; r < p; )a[r] = t.charCodeAt(r),r++;for (e = a.length,o = "",r = 0; r < e; r += n.chunkSize) {for (c = new BigInt,s = 0,f = r + n.chunkSize > e ? e % n.chunkSize : n.chunkSize,u = [],i = 0; i < f; i++)u[i] = a[r + f - 1 - i];for (u[f] = 0,v = Math.max(8, n.digitSize - 3 - f),i = 0; i < v; i++)u[f + 1 + i] = Math.floor(Math.random() * 254) + 1;for (u[n.digitSize - 2] = 2,u[n.digitSize - 1] = 0,h = 0; h < n.digitSize; ++s)c.digits[s] = u[h++],c.digits[s] += u[h++] << 8;l = n.barrett.powMod(c, n.e);y = n.radix == 16 ? biToHex(l) : biToString(l, n.radix);o += y + " "}return o.substring(0, o.length - 1)
}
function decryptedString(n, t) {for (var e = t.split(" "), i = "", r, u, o, f = 0; f < e.length; ++f)for (o = n.radix == 16 ? biFromHex(e[f]) : biFromString(e[f], n.radix),u = n.barrett.powMod(o, n.d),r = 0; r <= biHighIndex(u); ++r)i += String.fromCharCode(u.digits[r] & 255, u.digits[r] >> 8);return i.charCodeAt(i.length - 1) == 0 && (i = i.substring(0, i.length - 1)),i
}
var biRadixBase = 2, biRadixBits = 16, bitsPerDigit = biRadixBits, biRadix = 65536, biHalfRadix = biRadix >>> 1, biRadixSquared = biRadix * biRadix, maxDigitVal = biRadix - 1, maxInteger = 9999999999999998, maxDigits, ZERO_ARRAY, bigZero, bigOne, dpl10, lr10, hexatrigesimalToChar, hexToChar, highBitMasks, lowBitMasks;
setMaxDigits(20);
dpl10 = 15;
lr10 = biFromNumber(1e15);
hexatrigesimalToChar = ["0", "1", "2", "3", "4", "5", "6", "7", "8", "9", "a", "b", "c", "d", "e", "f", "g", "h", "i", "j", "k", "l", "m", "n", "o", "p", "q", "r", "s", "t", "u", "v", "w", "x", "y", "z"];
hexToChar = ["0", "1", "2", "3", "4", "5", "6", "7", "8", "9", "a", "b", "c", "d", "e", "f"];
highBitMasks = [0, 32768, 49152, 57344, 61440, 63488, 64512, 65024, 65280, 65408, 65472, 65504, 65520, 65528, 65532, 65534, 65535];
lowBitMasks = [0, 1, 3, 7, 15, 31, 63, 127, 255, 511, 1023, 2047, 4095, 8191, 16383, 32767, 65535];
setMaxDigits(129);
// key_to_encode 通过搜索获取
//console.log(encryptedString(key_to_encode,'412304'))
针对这个说明一下方法:
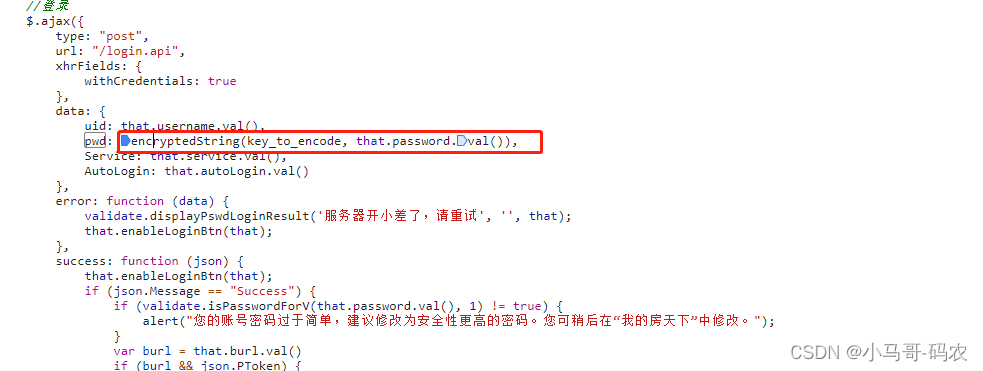
1、首先通过查看请求链接参数,可以看到pwd是经过加密的,那么在search里搜索pwd,定位到如下位置
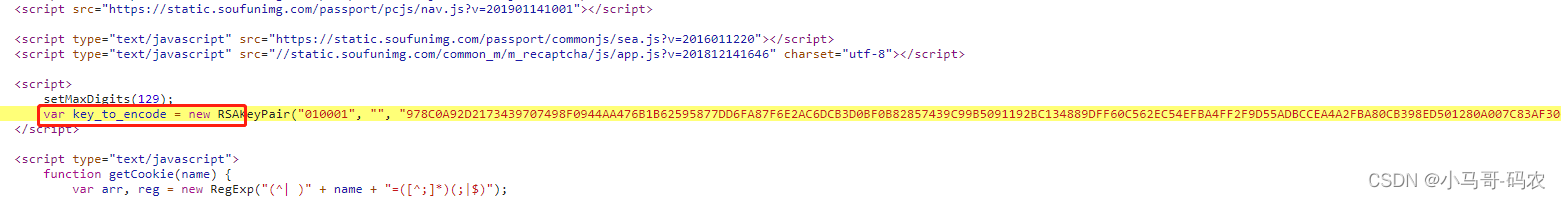
2、截下来我们打断点找到该方法 ,该方法中还有一个参数key_to_encode,同样的方法进行搜索

3、接下来,查找其余需要的代码。如果该js文件代码不多的话,可以全部进行复制。这样,js加密代码就完成了,剩下的就是通过python代码进行密码加密,然后发起登录请求操作
5、模拟闪职登陆-RSA加密
- 方法一、加密方式通过python重构
1、模拟登陆:
使用python重构了rsa加密方式,得到加密之后的密码
从网页源码中获取到了csrfmiddlewaretoken和pk
携带data发送post进行模拟登陆
2、遇到RSA加密的
如果加密代码不是很长,复制所有的
如果加密代码比较长,最好使用python重构一下加密过程(需要得到重构时所必须的一些参数)
重构的时候要特别注意:有没有对一些细节方面的小处理(如果有,还是要回归js代码的)
setPublicKey----->RSA
encrypt decrypt --->DES/AES
代码部分:
分析:首先需要的参数:
username:
password: KaYiT7HiFfadM2S7S31w3mgTHA/Z5idogLXrVi6hdROy6M837ilwXVaV+m4hbLE/SRXTiB+sjbbGP0VsNKK5TNdnuq3/ukRSbr5WtAMF8eoH2f/NhSa4OmZZR3BN+JcOSmdk8qLgsI9FaR8xCRu+P6hc+n/liAq+DfEfjgfI31I=
csrfmiddlewaretoken: HS5stw6ug7ZVnj5WP6eEoxG96NydfsYToEQ2eYPLlBc2uhbyLvKEhk6PKs3vr4Cd搜索password:
索索到
eval(function(p,a,c,k,e,d){e=function(c){return(c<a?'':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)d[e(c)]=k[c]||e(c);k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p}('4 2(){e 8=$("#1").d();e 3=6 0();e a=$("#9").d();3.b(a);e 7=3.3(8);$("#1").d(7);$("#5").c()}',62,15,'JSEncrypt|MemberPassword|doLogin|encrypt|function|login_button|new|pass_new|password_old|pk|public_key|setPublicKey|submit|val|var'.split('|'),0,{}))
}这种基本上就是经过加密的,
通过以下链接进行解密查看源代码:解密工具地址:http://www.ab173.com/enc/eval_package.php经过解密之后:
function doLogin() {var password_old = $("#MemberPassword").val(); # 输入密码var encrypt = new JSEncrypt(); # 加密类var public_key = $("#pk").val(); # 源码中可以获得pk(公钥)encrypt.setPublicKey(public_key); # 由setPublickKey函数基本可以确定是RSA加密var pass_new = encrypt.encrypt(password_old);# 进行加密$("#MemberPassword").val(pass_new);$("#login_button").submit()
}shanzhi_rsa.py这里因为是引入了外部加密文件,加密代码比较长,这里使用方法通过python重构加密过程
# 安装需要的包: pip install pycryptodome -i https://pypi.tuna.tsinghua.edu.cn/simplefrom Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_v1_5 as cry_pksc1_v1_5
import base64
# Pk公钥 password 密码
def encrypto(pk, password):"""使用公钥对密码进行加密处理:param pk: 公钥:param password: 明文密码:return: RAS加密之后的密码"""public_key = "-----BEGIN PUBLIC KEY-----\n{}\n-----END PUBLIC KEY-----".format(pk)# 导入公钥 返回一个RSA秘钥对象rsakey = RSA.importKey(public_key)# 对需要加密的内容进行PKCS#1 v1.5加密cipher = cry_pksc1_v1_5.new(rsakey)# 使用公钥加密密码 密码必须是二进制miwen_encode = cipher.encrypt(password.encode())# 再使用Base64对类似字节的对象进行编码cipher_text = base64.b64encode(miwen_encode).decode()return cipher_textshanzhi_login.pyimport requests
from shanzhi_rsa import encrypto
from lxml import etree
# lxml.etree._Element
from lxml.etree import _Elementurl = 'http://shanzhi.spbeen.com/login/'
header = {'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.82 Safari/537.36','Cookie': 'shanzhi_kmer=h9wm0ptr9kcuza527as3a43a6zuwzsid; csrftoken=yHdq0AaPEO1pyiC2zji4MmeyLRNcXVcZLNoHCT3izQ52lwvASvHv0jgsGG9kEXUN'
}
# 先从网页源码中得到csrfmiddlewaretoken和pk
reponse_obj = requests.get(url, headers=header)
tree = etree.HTML(reponse_obj.text)
csrfmiddlewaretoken = tree.xpath('//input[@name="csrfmiddlewaretoken"]/@value')[0]
pk = tree.xpath('//input[@id="pk"]/@value')[0]
old_password = 'logic_00'
password = encrypto(pk, old_password)
data_dict = {'username': 'logic_00','password': password,'csrfmiddlewaretoken': csrfmiddlewaretoken
}
res = requests.post(url, headers=header, data=data_dict)
print(res.text)- 方法二、使用js加密
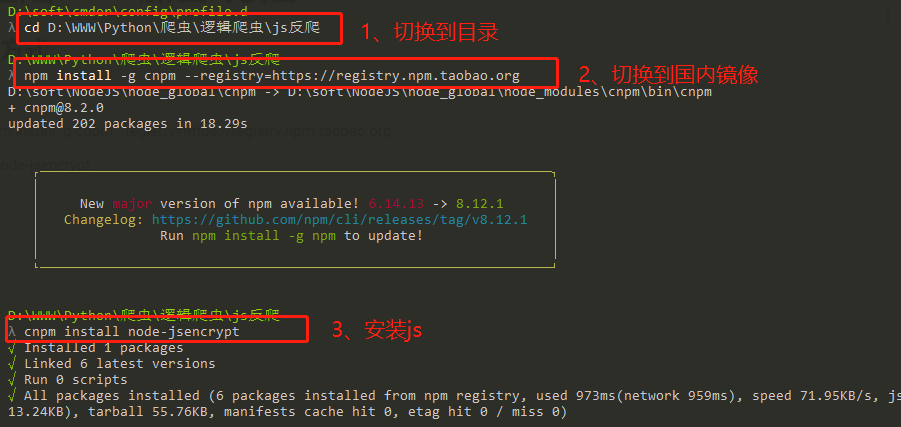
1、cd 进项目目录
2、做国内资源映射:
npm install -g cnpm --registry=https://registry.npm.taobao.org,最后安装:cnpm install node-jsencrypt
shanzhi.js:const JSEncrypt = require('node-jsencrypt')
// 登陆
function doLogin(pass_old,pk) {var encrypt = new JSEncrypt()var public_key = pkencrypt.setPublicKey(public_key)var pass_new = encrypt.encrypt(pass_old)return pass_new
}tools.pyimport execjs
def get_js(file_name,fun_name,*args):with open(file_name,'r',encoding='utf-8') as file_obj:js_code = file_obj.read()# 1、编译js文件cjs = execjs.compile(js_code)# 2、 执行js代码return cjs.call(fun_name,*args)shanzhi.pyimport requests
from lxml import etree
from tools import get_js# 目标url
url = 'http://shanzhi.spbeen.com/login/'
# 请求头
header = {'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.82 Safari/537.36','Cookie': 'shanzhi_kmer=h9wm0ptr9kcuza527as3a43a6zuwzsid; csrftoken=yHdq0AaPEO1pyiC2zji4MmeyLRNcXVcZLNoHCT3izQ52lwvASvHv0jgsGG9kEXUN'
}
# 先从网页源码中得到csrfmiddlewaretoken和pk
reponse_obj = requests.get(url, headers=header)
tree = etree.HTML(reponse_obj.text)
# 获取csrfmiddlewaretoken
csrfmiddlewaretoken = tree.xpath('//input[@name="csrfmiddlewaretoken"]/@value')[0]
# 获取pk
pk = tree.xpath('//input[@id="pk"]/@value')[0]
old_password = 'logic_00'
new_password = get_js('shanzhi.js','doLogin',old_password,pk)
data_dict = {'username': 'logic_00','password': new_password,'csrfmiddlewaretoken': csrfmiddlewaretoken
}
res = requests.post(url, headers=header, data=data_dict)
print(res.text)