版权声明
email:1256153255@qq.com
website for get 瑞萨RH850F1x开发板和瑞萨E1仿真器
认真的朋友会发现,我的上一篇博文《基于IAR for RH850的瑞萨RH850 FCL库用法介绍》在最后留下了一个bug,就是当FCL执行ERASE或WRITE时,返回的状态myRequest.status_enu经常是0x00000005(R_FCL_ERR_PROTECTION),在上一篇博客最后给的解决办法是通过RFP进行Chip的ERASE,但是这种方式的ERASE之后,只能正常的执行一次FCL的WRITE,第二次时又会出现R_FCL_ERR_PROTECTION。
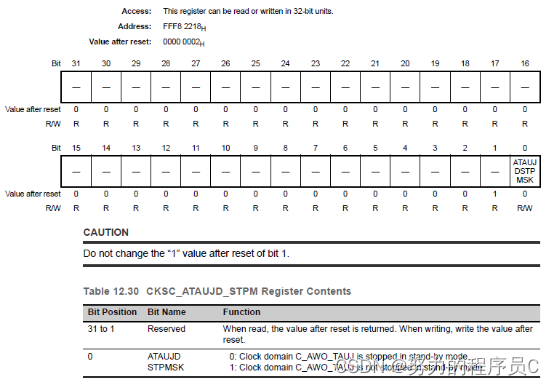
在FCL官方手册上分析出现R_FCL_ERR_PROTECTION的原因如下
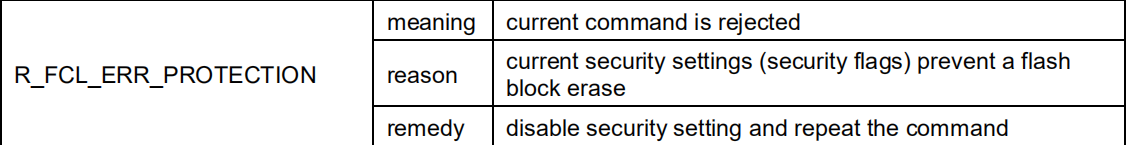
官方给的原因是:安全设置(安全Flag)被Enable了,导致Code Flash被 Protection了,解决办法就是Disable安全设置。
怎么Disable呢?继续查手册,找到这里
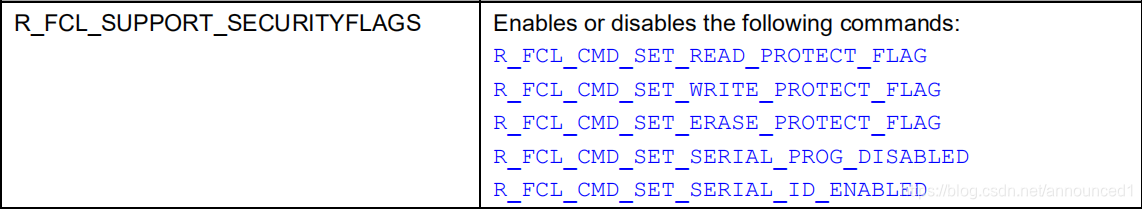
那就是说宏R_FCL_SUPPORT_SECURITYFLAGS是负责安全设置的Enable和Disable的,那好办呀,把代码中的R_FCL_SUPPORT_SECURITYFLAGS注释掉就完了。结果注释掉之后还是没完,依然R_FCL_ERR_PROTECTION。
那就试试其他区域呗,如下修改
/* erase block 2 and 3 */myRequest.command_enu = R_FCL_CMD_ERASE;myRequest.idx_u32 = 0x2; /* erased range = 0x4000 to 0x7fff */myRequest.cnt_u16 = 1;R_FCL_Execute (&myRequest);#if R_FCL_COMMAND_EXECUTION_MODE == R_FCL_HANDLER_CALL_USERwhile (R_FCL_BUSY == myRequest.status_enu){R_FCL_Handler ();}#endiftest_value = myRequest.status_enu;/* write 512 bytes to address 0x40000 (start of block 2) */REINITIALIZE_BUFFER;myRequest.command_enu = R_FCL_CMD_WRITE;myRequest.bufferAdd_u32 = (uint32_t)&writeBuffer_u08[0];myRequest.idx_u32 = 0x4000;myRequest.cnt_u16 = 1; /* written bytes = 256 * cnt_u16 */R_FCL_Execute (&myRequest);#if R_FCL_COMMAND_EXECUTION_MODE == R_FCL_HANDLER_CALL_USERwhile (R_FCL_BUSY == myRequest.status_enu){R_FCL_Handler ();}#endiftest_value = myRequest.idx_u32;
↓↓↓↓↓↓↓↓↓
/* erase block 2 and 3 */myRequest.command_enu = R_FCL_CMD_ERASE;myRequest.idx_u32 = 0x3; /* erased range = 0x4000 to 0x7fff */myRequest.cnt_u16 = 1;R_FCL_Execute (&myRequest);#if R_FCL_COMMAND_EXECUTION_MODE == R_FCL_HANDLER_CALL_USERwhile (R_FCL_BUSY == myRequest.status_enu){R_FCL_Handler ();}#endiftest_value = myRequest.status_enu;/* write 512 bytes to address 0x40000 (start of block 2) */REINITIALIZE_BUFFER;myRequest.command_enu = R_FCL_CMD_WRITE;myRequest.bufferAdd_u32 = (uint32_t)&writeBuffer_u08[0];myRequest.idx_u32 = 0x6000;myRequest.cnt_u16 = 1; /* written bytes = 256 * cnt_u16 */R_FCL_Execute (&myRequest);#if R_FCL_COMMAND_EXECUTION_MODE == R_FCL_HANDLER_CALL_USERwhile (R_FCL_BUSY == myRequest.status_enu){R_FCL_Handler ();}#endiftest_value = myRequest.idx_u32;
竟然可以了,再试试后边的其他block,也可以
那就是Block2不能这么玩儿了,为什么呢?是不是Block2放的还是Code,不能擦除呢?查map文件
11 638 bytes of readonly code memory50 bytes of readonly data memory41 116 bytes of readwrite data memory
Code量占用了11638Bytes,Block0和Block1共16KB,够用。
没辙了!!!
那就用RFP把整个1M的Code Flash读出来看看,结果发现问题所在了
S0110000437265617465642062792052465033
S31500000000E0022C2C000000000000000000000000B0
S315000000101F00E0027E2D000000000000000000002E
S31500000020EE0F4000C10E1F001F00E0027E2D0000F3
S31500000030EE0F4000C10E0F001F00E002662D00000B
。。。。。。。。
S31500002D7050000000000000008207610006E863EFD3
S31500002D8001000338013280FF0600A5FD7F00000028
S31500002D90850500008505000085050000E00748015F
S31500002DA041000000410000004100FFFFFFFFFFFF60
S31500002DB0FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF1D
S31500002DC0FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0D
S31500002DD0FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFD
从这段来看,code是放在Block0和Block1是没错。
但是,再往下
S31500003FD0FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEB
S31500003FE0FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFDB
S31500003FF0FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFCB
S31500004000000800000241000008000240000104040C
S31500004010000000002004000008020A080100080A47
S315000040200400820000000000008000000000060678
S31500004030000000220000000008000A08100400002A
。。。。。。。。
S31500005FD000000000000000000000000000000000BB
S31500005FE000000000000000000000000000000000AB
S31500005FF0000000000000000000000000000000009B
S31500006000000102030405060708090A0B0C0D0E0F12
S31500006010101112131415161718191A1B1C1D1E1F02
S31500006020202122232425262728292A2B2C2D2E2FF2
发现没有,Block2(0x0000 4000~0x0000 5FFF)不是ERASE状态,所以 不能 写 入。
而Block3开始(0x0000 6000)就是我们刚才写入的值。这下明白了吧,原来Block2不是ERASE状态。
但是这里还有两个疑问:
1、Block2里边这些数据是什么内容?
2、在FCL的COMMOND指令对Block2执行了R_FCL_CMD_ERASE,为什么不能正常ERASE?
这两个问题,还没找到原因,找到之后和大家共享出来,如有朋友知道,也请留言对我进行扫盲。