shiro
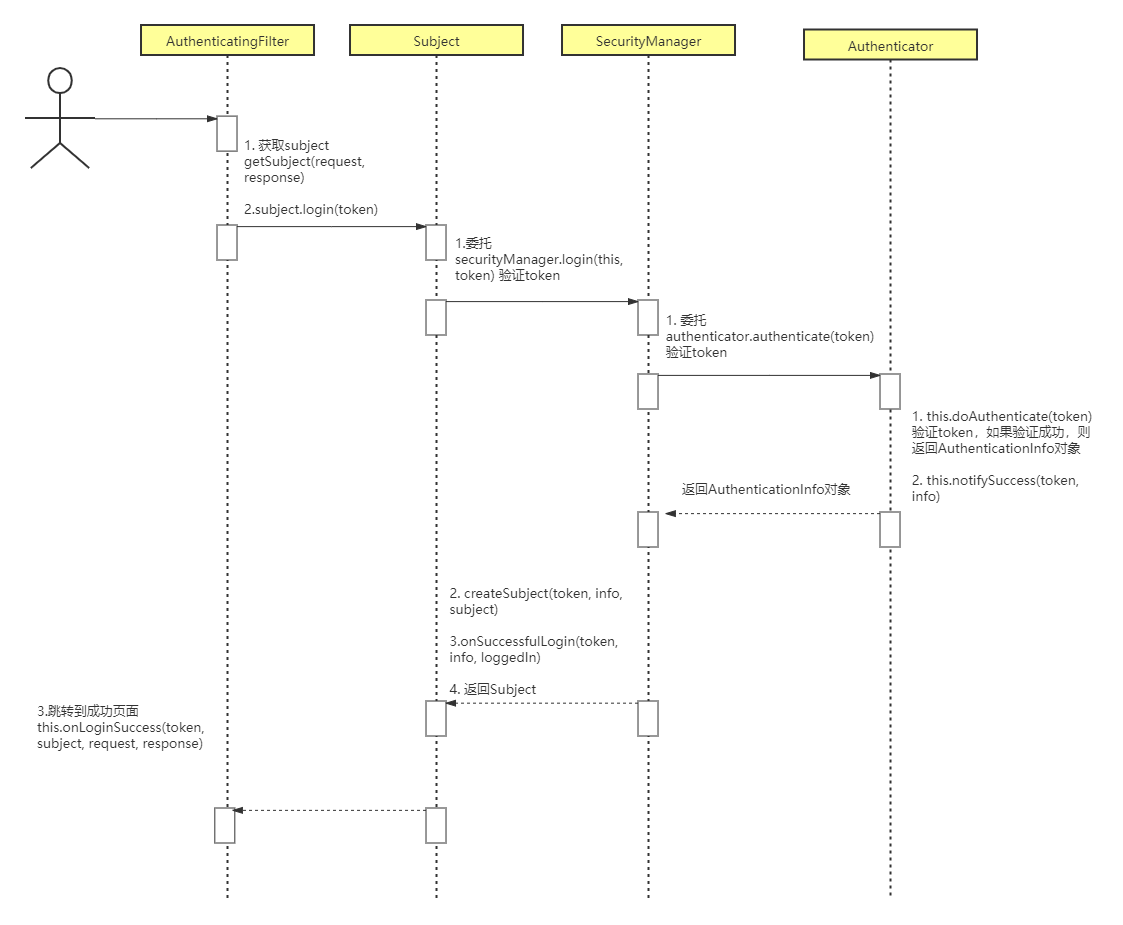
shiro处理的两个过程,一个是登录,这个过程完成后产生一个用户jwt,一个是访问接口时,通过jwt来完成验证的过程
登录逻辑:
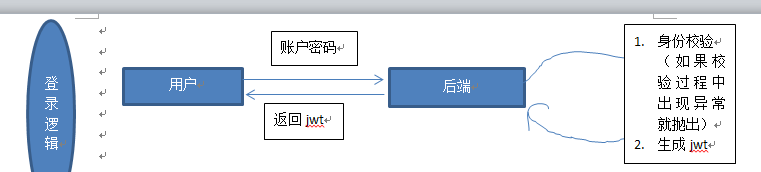
访问接口逻辑:

认证(authentication):
根据认证方式识别用户身份(jwt)
授权(authorization):
判断用户是否有访问权限(shiro)
jwt:JSON Web Token,由请求头、请求体和签名3部分组成,它主要用来认证。
shiro:是一个轻量级的安全框架,可以使用注解快速的实现权限管理。他主要用来授权。
具体实现:
ShiroConfig:
配置ShiroConfig,我们主要做了几件事情:
- 引入RedisSessionDAO和RedisCacheManager,为了解决shiro的权限数据和会话信息能保存到redis中,实现会话共享。
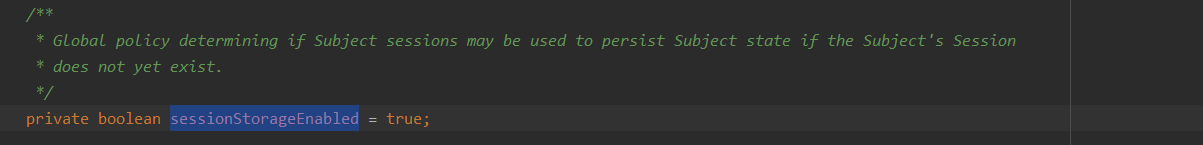
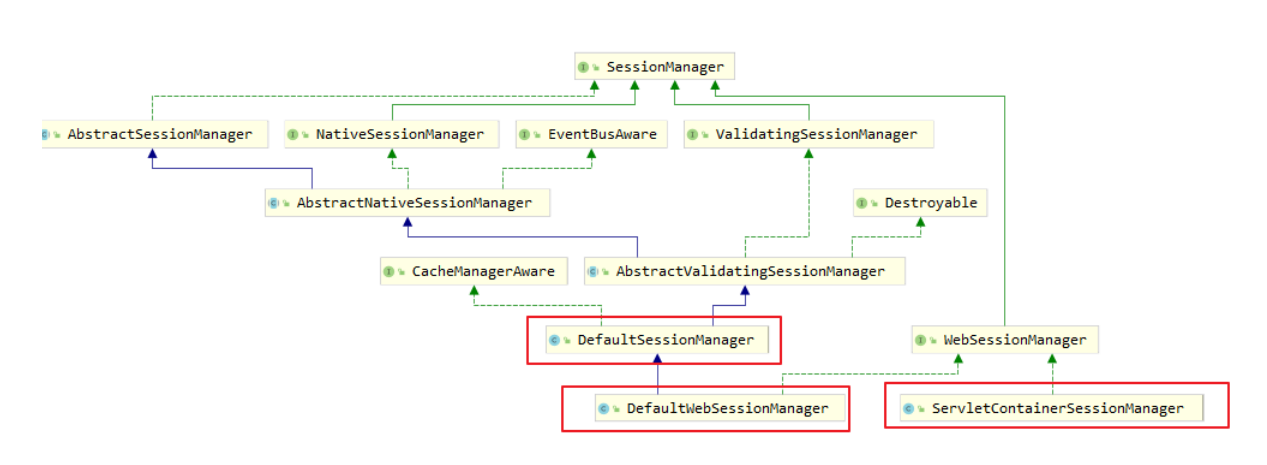
- 重写了SessionManager和DefaultWebSecurityManager,同时在DefaultWebSecurityManager中为了关闭shiro自带的session方式,我们需要设置为false,这样用户就不再能通过session方式登录shiro。后面将采用jwt凭证登录。
- 在ShiroFilterChainDefinition中,我们不再通过编码形式拦截Controller访问路径,而是所有的路由都需要经过JwtFilter这个过滤器,然后判断请求头中是否含有jwt的信息,有就登录,没有就跳过。跳过之后,有Controller中的shiro注解进行再次拦截,比如@RequiresAuthentication,这样控制权限访问。
/*** shiro启用注解拦截控制器*/
@Configuration
public class ShiroConfig {@AutowiredJwtFilter jwtFilter;@Beanpublic SessionManager sessionManager(RedisSessionDAO redisSessionDAO) {DefaultWebSessionManager sessionManager = new DefaultWebSessionManager();sessionManager.setSessionDAO(redisSessionDAO);return sessionManager;}@Beanpublic DefaultWebSecurityManager securityManager(AccountRealm accountRealm,SessionManager sessionManager,RedisCacheManager redisCacheManager) {DefaultWebSecurityManager securityManager = new DefaultWebSecurityManager(accountRealm);securityManager.setSessionManager(sessionManager);securityManager.setCacheManager(redisCacheManager);/** 关闭shiro自带的session,详情见文档*/DefaultSubjectDAO subjectDAO = new DefaultSubjectDAO();DefaultSessionStorageEvaluator defaultSessionStorageEvaluator = new DefaultSessionStorageEvaluator();defaultSessionStorageEvaluator.setSessionStorageEnabled(false);subjectDAO.setSessionStorageEvaluator(defaultSessionStorageEvaluator);securityManager.setSubjectDAO(subjectDAO);return securityManager;}@Beanpublic ShiroFilterChainDefinition shiroFilterChainDefinition() {DefaultShiroFilterChainDefinition chainDefinition = new DefaultShiroFilterChainDefinition();Map<String, String> filterMap = new LinkedHashMap<>();filterMap.put("/**", "jwt"); // 主要通过注解方式校验权限chainDefinition.addPathDefinitions(filterMap);return chainDefinition;}@Bean("shiroFilterFactoryBean")public ShiroFilterFactoryBean shiroFilterFactoryBean(SecurityManager securityManager,ShiroFilterChainDefinition shiroFilterChainDefinition) {ShiroFilterFactoryBean shiroFilter = new ShiroFilterFactoryBean();shiroFilter.setSecurityManager(securityManager);Map<String, Filter> filters = new HashMap<>();filters.put("jwt", jwtFilter);shiroFilter.setFilters(filters);Map<String, String> filterMap = shiroFilterChainDefinition.getFilterChainMap();shiroFilter.setFilterChainDefinitionMap(filterMap);return shiroFilter;}// 开启注解代理(默认好像已经开启,可以不要)@Beanpublic AuthorizationAttributeSourceAdvisor authorizationAttributeSourceAdvisor(SecurityManager securityManager){AuthorizationAttributeSourceAdvisor authorizationAttributeSourceAdvisor = new AuthorizationAttributeSourceAdvisor();authorizationAttributeSourceAdvisor.setSecurityManager(securityManager);return authorizationAttributeSourceAdvisor;}@Beanpublic static DefaultAdvisorAutoProxyCreator getDefaultAdvisorAutoProxyCreator() {DefaultAdvisorAutoProxyCreator creator = new DefaultAdvisorAutoProxyCreator();return creator;}
}那么,接下来,我们来看ShiroConfig中出现的AccountRealm,还有JwtFilter。
Realm:
自定义Realm是实现权限的关键,Realm类需要继承Shiro框架的AuthorizingRealm抽象类,重写以下两个方法
-
supports:为了让realm支持jwt的凭证校验
-
doGetAuthorizationInfo:通过从Token中取出的用户名,获取用户所具备的权限doGetAuthenticationInfo
-
doGetAuthenticationInfo:完成用户身份认证
@Component
public class AccountRealm extends AuthorizingRealm {@AutowiredUserService userService;@AutowiredJwtUtils jwtUtils;@Overridepublic boolean supports(AuthenticationToken token){return token instanceof JwtToken;}//获取权限@Overrideprotected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principalCollection) {return null;}//身份验证@Overrideprotected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException {JwtToken jwtToken = (JwtToken) token;String userId = jwtUtils.getClaimByToken((String) jwtToken.getPrincipal()).getSubject();User user = userService.getById(Long.valueOf(userId));if(user == null){throw new UnknownAccountException("账户不存在");}if(user.getStatus()==-1){throw new LockedAccountException("账户已被锁定");}AccountProfile profile = new AccountProfile();BeanUtil.copyProperties(user,profile);System.out.println("------------");return new SimpleAuthenticationInfo(profile,jwtToken.getCredentials(),getName());}
}JWTFilter:(过滤器)
除登录的请求之外,其他请求都会被拦截,走认证过程
需要实现的方法:
- createToken:实现登录,我们需要生成我们自定义支持的JwtToken
- onAccessDenied:拦截校验,当头部没有Authorization时候,我们直接通过,不需要自动登录;当带有的时候,首先我们校验jwt的有效性,没问题我们就直接执行executeLogin方法实现自动登录
- onLoginFailure:登录异常时候进入的方法,我们直接把异常信息封装然后抛出
- preHandle:拦截器的前置拦截,因为我们是前后端分析项目,项目中除了需要跨域全局配置之外,我们再拦截器中也需要提供跨域支持。这样,拦截器才不会在进入Controller之前就被限制了。
@Component
public class JwtFilter extends AuthenticatingFilter {@AutowiredJwtUtils jwtUtils;//登录时创建jwt@Overrideprotected AuthenticationToken createToken(ServletRequest servletRequest, ServletResponse servletResponse) throws Exception {HttpServletRequest request = (HttpServletRequest) servletRequest;String jwt = request.getHeader("Authorazation");if(StringUtils.isEmpty(jwt)){return null;}return new JwtToken(jwt);}//登录验证@Overrideprotected boolean onAccessDenied(ServletRequest servletRequest, ServletResponse servletResponse) throws Exception {HttpServletRequest request = (HttpServletRequest) servletRequest;String jwt = request.getHeader("Authorazation");if(StringUtils.isEmpty(jwt)){//return true;}else{//校验jwtClaims claim = jwtUtils.getClaimByToken(jwt);if(claim==null||jwtUtils.isTokenExpired(claim.getExpiration())){throw new ExpiredCredentialsException("token已失效,请重新登录");}//执行登录return executeLogin(servletRequest,servletResponse);}}//登录失败时执行@Overrideprotected boolean onLoginFailure(AuthenticationToken token, AuthenticationException e, ServletRequest request, ServletResponse response) {HttpServletResponse httpServletResponse = (HttpServletResponse) response;Throwable throwable = e.getCause() == null? e:e.getCause();Result result = Result.fail(throwable.getMessage());String json = JSONUtil.toJsonStr(result);try {httpServletResponse.getWriter().print(json);} catch (IOException ioException) {}return false;}//处理跨域@Overrideprotected boolean preHandle(ServletRequest request, ServletResponse response) throws Exception {HttpServletRequest httpServletRequest = WebUtils.toHttp(request);HttpServletResponse httpServletResponse = WebUtils.toHttp(response);httpServletResponse.setHeader("Access-control-Allow-Origin", httpServletRequest.getHeader("Origin"));httpServletResponse.setHeader("Access-Control-Allow-Methods", "GET,POST,OPTIONS,PUT,DELETE");httpServletResponse.setHeader("Access-Control-Allow-Headers", httpServletRequest.getHeader("Access-Control-Request-Headers"));// 跨域时会首先发送一个OPTIONS请求,这里我们给OPTIONS请求直接返回正常状态if (httpServletRequest.getMethod().equals(RequestMethod.OPTIONS.name())) {httpServletResponse.setStatus(org.springframework.http.HttpStatus.OK.value());return false;}return super.preHandle(request, response);}
}其实主要就是doGetAuthenticationInfo登录认证这个方法,可以看到我们通过jwt获取到用户信息,判断用户的状态,最后异常就抛出对应的异常信息,否者封装成SimpleAuthenticationInfo返回给shiro。 接下来我们逐步分析里面出现的新类(JwtToken和JwtFilter):
JwtToken:
shiro默认supports的是UsernamePasswordToken,而我们现在采用了jwt的方式,所以这里我们自定义一个JwtToken,来完成shiro的supports方法。
public class JwtToken implements AuthenticationToken {private String token;public JwtToken(String token) {this.token = token;}@Overridepublic Object getPrincipal() {return token;}@Overridepublic Object getCredentials() {return token;}
}JwtUtils:
JwtUtils是个生成和校验jwt的工具类,其中有些jwt相关的密钥信息是从项目配置文件中配置的:
/*** jwt工具类*/
@Slf4j
@Data
@Component
@ConfigurationProperties(prefix = "markerhub.jwt")
public class JwtUtils {private String secret;private long expire;private String header;/*** 生成jwt token*/public String generateToken(long userId) {Date nowDate = new Date();//过期时间Date expireDate = new Date(nowDate.getTime() + expire * 1000);return Jwts.builder().setHeaderParam("typ", "JWT").setSubject(userId+"").setIssuedAt(nowDate).setExpiration(expireDate).signWith(SignatureAlgorithm.HS512, secret).compact();}/*通过Token认证用户*/public Claims getClaimByToken(String token) {try {return Jwts.parser().setSigningKey(secret).parseClaimsJws(token).getBody();}catch (Exception e){log.debug("validate is token error ", e);return null;}}/*** token是否过期* @return true:过期*/public boolean isTokenExpired(Date expiration) {return expiration.before(new Date());}
}