文章目录
- 一、崩溃信息描述
- 二、手机命令行操作
- 三、电脑命令行操作
- 四、Tombstone 内容
Tombstone 报错信息日志文件被保存在了 /data/tombstones/ 目录下 , 先 ROOT 再说 , 没有 ROOT 权限无法访问该目录中的信息 ;
使用 Pixel 2 手机进行调试 , 其它 ROOT 后的手机也可以使用 ;
ROOT 前先 解锁 Bootloader , 参考博客 【Android】Pixel 2 解锁 Bootloader
ROOT 操作 , 参考博客 【Android】Pixel 2 Android 9 系统 ROOT 操作 ( TWRP 下载 | Magisk Manager 下载 | 线刷包下载 | 线刷 9.0 系统 | ROOT 操作 )
一、崩溃信息描述
2020-11-12 09:21:47.476 11561-11575/com.tombstone.demo A/libc: Fatal signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0xc in tid 11575 (Binder:11561_3), pid 11561 (process)
2020-11-12 09:21:47.539 11606-11606/? A/DEBUG: *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: Build fingerprint: 'google/walleye/walleye:9/PQ3A.190801.002/5670241:user/release-keys'
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: Revision: 'MP1'
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: ABI: 'arm64'
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: pid: 11561, tid: 11575, name: Binder:11561_3 >>> com.tombstone.demo:process <<<
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0xc
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: Cause: null pointer dereference
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: Abort message: 'art_method.cc:611] Check failed: existing_entry_point != nullptr void android.accessibilityservice.AccessibilityService.<init>()@0x7e70e6f588'
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: x0 0000000000000000 x1 0000000000000000 x2 0000007e86085ca1 x3 0000000000000000
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: x4 0000000000000000 x5 0000007e7dc69b6f x6 000000000000000a x7 000000000000000a
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: x8 7af92b4d5bbf85bd x9 7af92b4d5bbf85bd x10 0000000000000000 x11 0000007f068804a8
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: x12 20646c6568207c20 x13 3d7365786574756d x14 00000000ffffffff x15 0000007f0687fc18
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: x16 0000007e8612bef0 x17 0000007f097679b0 x18 0000007f0687f69a x19 0000007f06880480
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: x20 0000000000000000 x21 0000007e86051f10 x22 0000000000000000 x23 0000007e70e6f588
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: x24 0000000000000001 x25 0000000000000000 x26 0000000000000000 x27 0000007e863434a0
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: x28 0000000000000001 x29 0000007f068802c0
2020-11-12 09:21:47.540 11606-11606/? A/DEBUG: sp 0000007f068802b0 lr 0000007e85f9162c pc 0000007e85f91630
2020-11-12 09:21:47.566 11606-11606/? A/DEBUG: backtrace:
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #00 pc 00000000004a5630 /system/lib64/libart.so (art::CurrentMethodVisitor::VisitFrame()+24)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #01 pc 0000000000484608 /system/lib64/libart.so (_ZN3art12StackVisitor9WalkStackILNS0_16CountTransitionsE0EEEvb+1656)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #02 pc 0000000000495d9c /system/lib64/libart.so (art::Thread::DumpStack(std::__1::basic_ostream<char, std::__1::char_traits<char>>&, bool, BacktraceMap*, bool) const+316)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #03 pc 00000000004afd5c /system/lib64/libart.so (art::DumpCheckpoint::Run(art::Thread*)+844)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #04 pc 00000000004a8a9c /system/lib64/libart.so (art::ThreadList::RunCheckpoint(art::Closure*, art::Closure*)+476)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #05 pc 00000000004a7cd4 /system/lib64/libart.so (art::ThreadList::Dump(std::__1::basic_ostream<char, std::__1::char_traits<char>>&, bool)+500)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #06 pc 000000000046a9d0 /system/lib64/libart.so (art::Runtime::Abort(char const*)+392)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #07 pc 0000000000008d2c /system/lib64/libbase.so (android::base::LogMessage::~LogMessage()+724)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #08 pc 00000000000d07f0 /system/lib64/libart.so (art::ArtMethod::GetOatQuickMethodHeader(unsigned long)+608)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #09 pc 00000000001a0d0c /system/lib64/libart.so (art::FaultManager::IsInGeneratedCode(siginfo*, void*, bool)+908)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #10 pc 00000000001a0654 /system/lib64/libart.so (art::FaultManager::HandleFault(int, siginfo*, void*)+92)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #11 pc 0000000000002b80 /system/bin/app_process64 (art::SignalChain::Handler(int, siginfo*, void*)+568)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #12 pc 000000000000088c [vdso:0000007f0bc35000]
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #13 pc 0000000000553bcc /system/lib64/libart.so (ExecuteMterpImpl+33356)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #14 pc 0000000000390f46 /system/framework/boot-framework.vdex (android.app.ContextImpl.sendBroadcast+94)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #15 pc 0000000000255e68 /system/lib64/libart.so (_ZN3art11interpreterL7ExecuteEPNS_6ThreadERKNS_20CodeItemDataAccessorERNS_11ShadowFrameENS_6JValueEb.llvm.2088410233+496)
2020-11-12 09:21:47.567 11606-11606/? A/DEBUG: #16 pc 000000000025b9e8 /system/lib64/libart.so (art::interpreter::ArtInterpreterToInterpreterBridge(art::Thread*, art::CodeItemDataAccessor const&, art::ShadowFrame*, art::JValue*)+216)
2020-11-12 09:21:47.781 941-941/? E//system/bin/tombstoned: Tombstone written to: /data/tombstones/tombstone_00
在上述崩溃信息的最后给出了提示 “Tombstone written to: /data/tombstones/tombstone_00” , 崩溃日志信息被保存到了 /data/tombstones/tombstone_00 文件中 ;
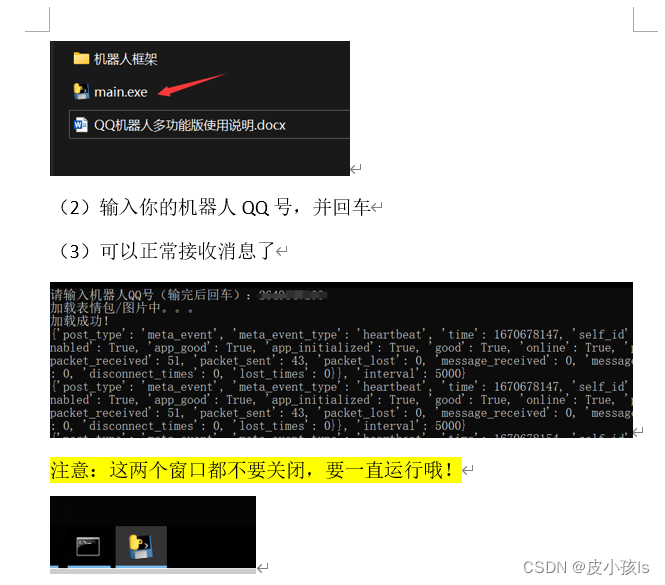
二、手机命令行操作
进入手机的命令行 ;
adb shell
获取 root 权限 ;
su
进入 /data/tombstones/ 目录 ;
cd /data/tombstones/
查看该目录下的崩溃日志文件 ;
ls
下面的截图中可以看到 , 上述崩溃日志 tombstone_00 ;

首先将该日志文件拷贝到 /sdcard/ 目录 ;
cp /data/tombstones/tombstone_00 /sdcard/tombstone_00

手机命令行操作完毕 , 执行两次 exit , 第一次退出 root 模式 , 第二次退出手机命令行 ;
exit
exit
三、电脑命令行操作
之前在手机命令行中 , 我们将 /data/tombstones/tombstone_00 的崩溃日志文件拷贝到了 sd 卡中 , /sdcard/tombstone_00 ;
adb pull 命令无法从 /data/ 目录中直接拉取文件 , 拷贝到 sd 卡中 , 就可以从 sd 卡拉取该文件 ;
将 /sdcard/tombstone_00 崩溃日志文件拉取到本地 ;
adb pull /sdcard/tombstone_00 .
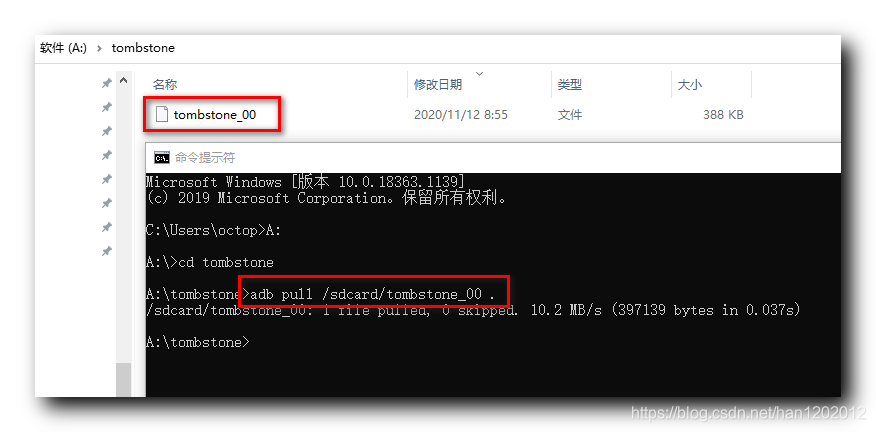
这样就获取到了 tombstone_00 文件 ;
四、Tombstone 内容
打开后查看其中的大致内容 :
*** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
Build fingerprint: 'google/walleye/walleye:9/PQ3A.190801.002/5670241:user/release-keys'
Revision: 'MP1'
ABI: 'arm64'
pid: 11561, tid: 11575, name: Binder:11561_3 >>> com.tombstone.demo:process <<<
signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0xc
Cause: null pointer dereference
Abort message: 'art_method.cc:611] Check failed: existing_entry_point != nullptr void android.accessibilityservice.AccessibilityService.<init>()@0x7e70e6f588'x0 0000000000000000 x1 0000000000000000 x2 0000007e86085ca1 x3 0000000000000000x4 0000000000000000 x5 0000007e7dc69b6f x6 000000000000000a x7 000000000000000ax8 7af92b4d5bbf85bd x9 7af92b4d5bbf85bd x10 0000000000000000 x11 0000007f068804a8x12 20646c6568207c20 x13 3d7365786574756d x14 00000000ffffffff x15 0000007f0687fc18x16 0000007e8612bef0 x17 0000007f097679b0 x18 0000007f0687f69a x19 0000007f06880480x20 0000000000000000 x21 0000007e86051f10 x22 0000000000000000 x23 0000007e70e6f588x24 0000000000000001 x25 0000000000000000 x26 0000000000000000 x27 0000007e863434a0x28 0000000000000001 x29 0000007f068802c0sp 0000007f068802b0 lr 0000007e85f9162c pc 0000007e85f91630backtrace:#00 pc 00000000004a5630 /system/lib64/libart.so (art::CurrentMethodVisitor::VisitFrame()+24)#01 pc 0000000000484608 /system/lib64/libart.so (_ZN3art12StackVisitor9WalkStackILNS0_16CountTransitionsE0EEEvb+1656)#02 pc 0000000000495d9c /system/lib64/libart.so (art::Thread::DumpStack(std::__1::basic_ostream<char, std::__1::char_traits<char>>&, bool, BacktraceMap*, bool) const+316)#03 pc 00000000004afd5c /system/lib64/libart.so (art::DumpCheckpoint::Run(art::Thread*)+844)#04 pc 00000000004a8a9c /system/lib64/libart.so (art::ThreadList::RunCheckpoint(art::Closure*, art::Closure*)+476)#05 pc 00000000004a7cd4 /system/lib64/libart.so (art::ThreadList::Dump(std::__1::basic_ostream<char, std::__1::char_traits<char>>&, bool)+500)#06 pc 000000000046a9d0 /system/lib64/libart.so (art::Runtime::Abort(char const*)+392)#07 pc 0000000000008d2c /system/lib64/libbase.so (android::base::LogMessage::~LogMessage()+724)#08 pc 00000000000d07f0 /system/lib64/libart.so (art::ArtMethod::GetOatQuickMethodHeader(unsigned long)+608)#09 pc 00000000001a0d0c /system/lib64/libart.so (art::FaultManager::IsInGeneratedCode(siginfo*, void*, bool)+908)#10 pc 00000000001a0654 /system/lib64/libart.so (art::FaultManager::HandleFault(int, siginfo*, void*)+92)#11 pc 0000000000002b80 /system/bin/app_process64 (art::SignalChain::Handler(int, siginfo*, void*)+568)#12 pc 000000000000088c [vdso:0000007f0bc35000]#13 pc 0000000000553bcc /system/lib64/libart.so (ExecuteMterpImpl+33356)#14 pc 0000000000390f46 /system/framework/boot-framework.vdex (android.app.ContextImpl.sendBroadcast+94)#15 pc 0000000000255e68 /system/lib64/libart.so (_ZN3art11interpreterL7ExecuteEPNS_6ThreadERKNS_20CodeItemDataAccessorERNS_11ShadowFrameENS_6JValueEb.llvm.2088410233+496)#16 pc 000000000025b9e8 /system/lib64/libart.so (art::interpreter::ArtInterpreterToInterpreterBridge(art::Thread*, art::CodeItemDataAccessor const&, art::ShadowFrame*, art::JValue*)+216)stack:0000007f06880230 0000007e86343400 [anon:libc_malloc]0000007f06880238 000000000000000b0000007f06880240 0000000000002d370000007f06880248 0000007e86059197 /system/lib64/libart.so0000007f06880250 0000007f06880580 [anon:thread signal stack]0000007f06880258 7af92b4d5bbf85bd0000007f06880260 00000000000000010000007f06880268 0000007e70e6f588 <anonymous:0000007e70d74000>0000007f06880270 00000000000000010000007f06880278 0000007e70e6f588 <anonymous:0000007e70d74000>0000007f06880280 00000000000000000000007f06880288 0000007e86051f10 /system/lib64/libart.so (art_quick_instrumentation_exit)0000007f06880290 00000000000000000000007f06880298 0000007f06880480 [anon:thread signal stack]0000007f068802a0 0000007f068802c0 [anon:thread signal stack]0000007f068802a8 0000007e85f9162c /system/lib64/libart.so (_ZN3art20CurrentMethodVisitor10VisitFrameEv+20)#00 0000007f068802b0 0000000000000000........ ........#01 0000007f068802d0 0000040000000000........ ........#02 0000007f06880480 0000007e86123170 /system/lib64/libart.so........ ........#03 0000007f06880540 615b202020202020........ ........#04 0000007f068806f0 0000007f068809e8 [anon:thread signal stack]........ ........#05 0000007f06880940 0000007f068809c0 [anon:thread signal stack]........ ........#06 0000007f06880a80 0000000b86057ea1........ ........#07 0000007f06880b00 0000007f06880b70 [anon:thread signal stack]........ ........#08 0000007f06880b80 0000000000000000........ ........#09 0000007f06880c00 0000007e70e6c9b0 <anonymous:0000007e70d74000>........ ........#10 0000007f06880c90 0000000000000002........ ........#11 0000007f06880d10 0000007f06880da0 [anon:thread signal stack]........ ........#12 0000007f06880da0 000000000000000b........ ........#13 0000007e70e6c9b0 0000007e70e6f588 <anonymous:0000007e70d74000>........ ........#14 0000007e70e6ca00 0000007e86343400 [anon:libc_malloc]........ ........#15 0000007e70e6ca00 0000007e86343400 [anon:libc_malloc]........ ........#16 0000007e70e6cac0 00000000000000080000007e70e6cac8 0000007e6e9e5268 /data/app/com.tombstone.demo-h00jR9L0Nz3hIKifxKrl5Q==/lib/arm64/liboboe.so (Java_com_tombstone_demo_OboePlayer_play+388)0000007e70e6cad0 00000000000000000000007e70e6cad8 00000000000000000000007e70e6cae0 00000000000000000000007e70e6cae8 00000000000000000000007e70e6caf0 00000000000000000000007e70e6caf8 00000000000000000000007e70e6cb00 00000000000000000000007e70e6cb08 00000000000000000000007e70e6cb10 00000000000000000000007e70e6cb18 00000000000000000000007e70e6cb20 00000000000000000000007e70e6cb28 00000000000000000000007e70e6cb30 00000000000000000000007e70e6cb38 0000000000000000memory near x2 (/system/lib64/libart.so):0000007e86085c80 6f6e207361772064 6863617474612074 d was not attach0000007e86085c90 7572206f74206465 0a2921656d69746e ed to runtime!).0000007e86085ca0 656e72656b202000 726f624100203a6c . kernel: .Abor0000007e86085cb0 72687420676e6974 7544000a3a646165 ting thread:..Du0000007e86085cc0 6c6120676e69706d 646165726874206c mping all thread0000007e86085cd0 756f687469772073 706f727070612074 s without approp0000007e86085ce0 6f6c206574616972 646c656820736b63 riate locks held0000007e86085cf0 616572687420003a 6c207473696c2064 :. thread list l0000007e86085d00 74756d20006b636f 636f6c20726f7461 ock. mutator loc0000007e86085d10 6874206c6c41006b 000a3a7364616572 k.All threads:..0000007e86085d20 20676e69646e6550 6f69747065637865 Pending exceptio0000007e86085d30 424147495300206e 5542474953005452 n .SIGABRT.SIGBU0000007e86085d40 4550464749530053 004c4c4947495300 S.SIGFPE.SIGILL.0000007e86085d50 0045504950474953 0056474553474953 SIGPIPE.SIGSEGV.0000007e86085d60 4c464b5453474953 4152544749530054 SIGSTKFLT.SIGTRA0000007e86085d70 4c4c49003f3f0050 0043504f4c4c495f P.??.ILL_ILLOPC.memory near x5 ([anon:libc_malloc]):0000007e7dc69b48 636f6c2074726f62 6174756d2220226b bort lock" "muta0000007e7dc69b58 6b636f6c20726f74 6465726168732822 tor lock"(shared0000007e7dc69b68 000a29646c656820 0000000000000000 held)..........0000007e7dc69b78 0000000000000000 c110000040e00000 ...........@....0000007e7dc69b88 0000000000000000 00000000c1600000 ..........`.....0000007e7dc69b98 00000000c1600000 00000000bf8d6000 ..`......`......0000007e7dc69ba8 3f654000c0000000 40000000c0000000 .....@e?.......@0000007e7dc69bb8 0000000000000000 4160000000000000 ..............`A0000007e7dc69bc8 4160000000000000 3f8d600000000000 ......`A.....`.?0000007e7dc69bd8 400000003f654000 4000000040000000 .@e?...@...@...@0000007e7dc69be8 0000000000000000 0000000041600000 ..........`A....0000007e7dc69bf8 0000000041600000 000000003f8d6000 ..`A.....`.?....0000007e7dc69c08 bf65400040000000 c000000040000000 ...@.@e....@....0000007e7dc69c18 0000000000000000 c160000000000000 ..............`.0000007e7dc69c28 c160000000000000 bf8d600000000000 ......`......`..0000007e7dc69c38 c0000000bf654000 c0000000c0000000 .@e.............
分析上述 Stack , 基本可以根据如下日志 , 将错误定位到 NDK 方法 Java_com_tombstone_demo_OboePlayer_play 中 ;
#16 0000007e70e6cac0 00000000000000080000007e70e6cac8 0000007e6e9e5268 /data/app/com.tombstone.demo-h00jR9L0Nz3hIKifxKrl5Q==/lib/arm64/liboboe.so (Java_com_tombstone_demo_OboePlayer_play+388)




![OpenHarmony啃论文俱乐部—盘点开源鸿蒙引用的三方开源软件[1]](https://img-blog.csdnimg.cn/img_convert/9f5bf9c110d2ecfc54abf0b39fe6e243.png)