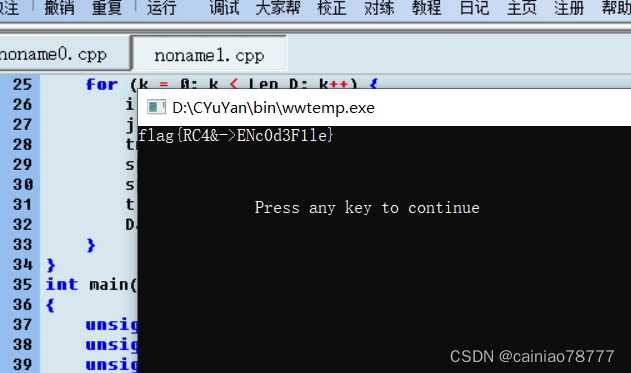
0x01. 进入环境,下载附件
题目给出的是一个无后缀文件,我们将其下载。先看看是否有套壳,发现没有套壳。那么接下来就老套路了
0x02. 问题分析
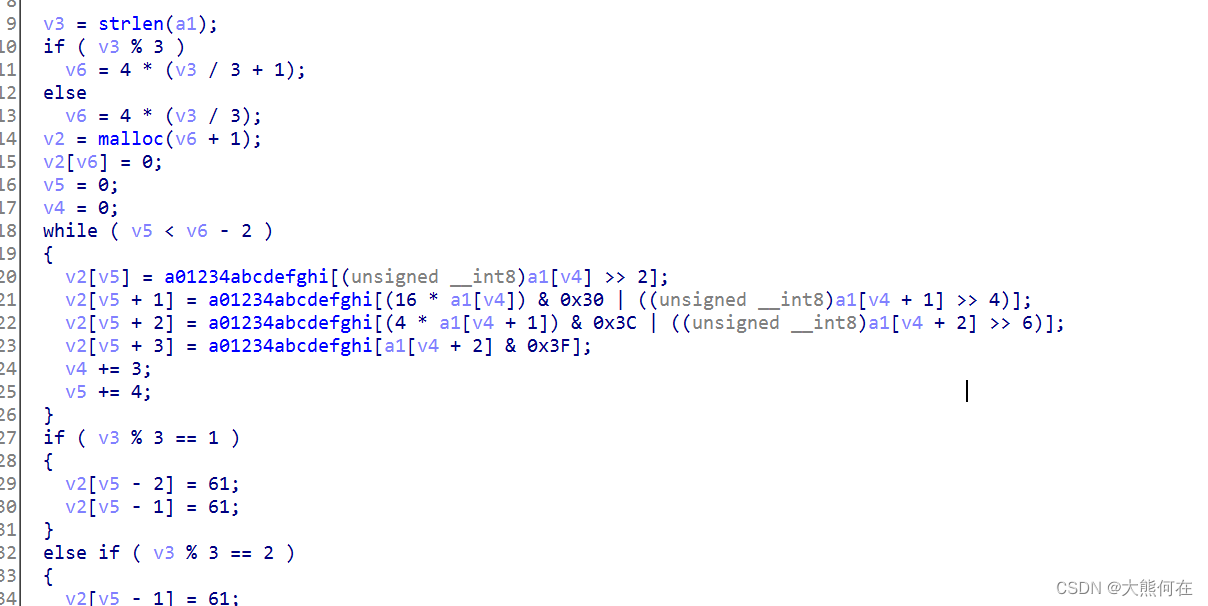
我们使用IDA Pro打开文件,找到main函数,反编译文件,得到代码如下:
__int64 __fastcall main(int a1, char **a2, char **a3)
{char *v3; // rbx__int64 v4; // rax__int64 v5; // rdx__int64 v6; // rax__int64 v7; // rdx__int64 v8; // rdx__int64 v9; // rdx__int64 i; // [rsp+10h] [rbp-60h]char v12; // [rsp+20h] [rbp-50h]char v13; // [rsp+4Fh] [rbp-21h]__int64 v14; // [rsp+50h] [rbp-20h]int v15; // [rsp+5Ch] [rbp-14h]if ( a1 != 2 ){v3 = *a2;v4 = std::operator<<<std::char_traits<char>>(&std::cout, "Usage: ", a3);v6 = std::operator<<<std::char_traits<char>>(v4, v3, v5);std::operator<<<std::char_traits<char>>(v6, " flag\n", v7);exit(0);}std::allocator<char>::allocator(&v13, a2, a3);std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(&v12, a2[1], &v13);std::allocator<char>::~allocator(&v13);v15 = 0;for ( i = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::begin(&v12); ; sub_400D7A(&i) ){v14 = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::end(&v12);if ( !(unsigned __int8)sub_400D3D(&i, &v14) )break;v9 = *(unsigned __int8 *)sub_400D9A((__int64)&i);if ( (_BYTE)v9 != off_6020A0[dword_6020C0[v15]] )sub_400B56((__int64)&i, (__int64)&v14, v9);++v15;}sub_400B73((__int64)&i, (__int64)&v14, v8);std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(&v12);return 0LL;
}
阅读完代码,这不就是c++代码么,最核心的内容则是for循环中的内容,我们可以看到,off_6020A0[dword_6020C0[v15]]才是比较爱逻辑中的核心。
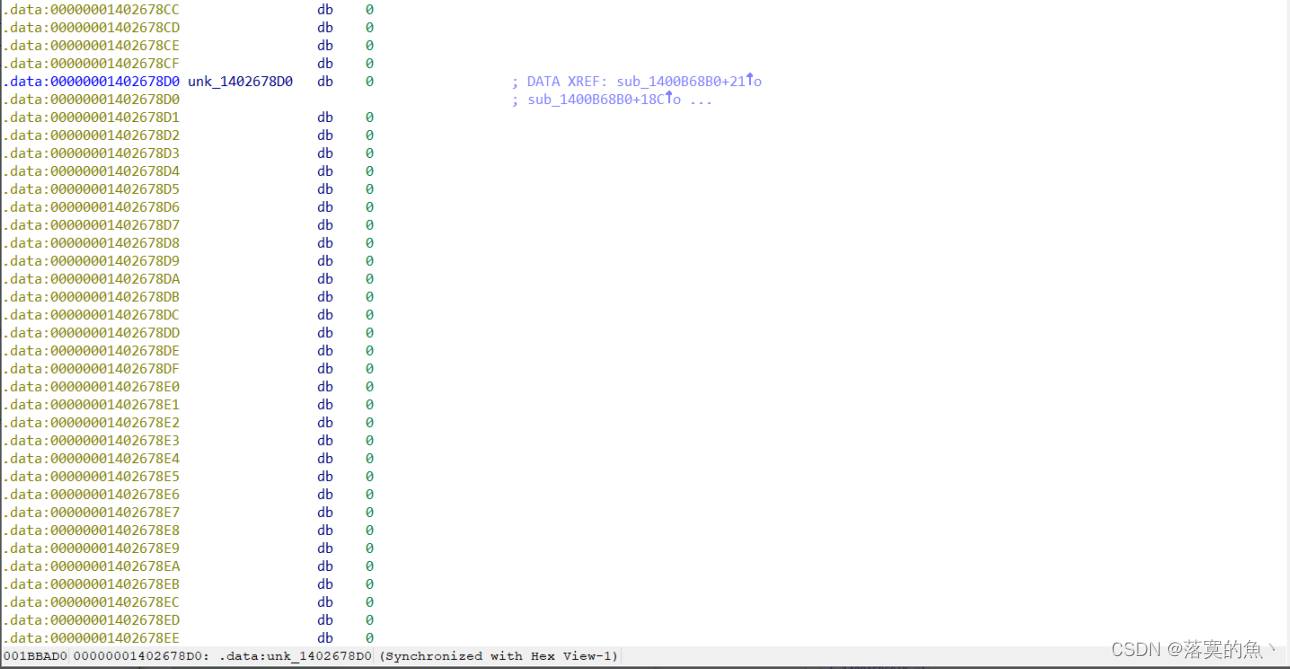
我们双击查看off_6020A0变量,发现是一串字符串,如图:

我们再双击查看dword_6020C0变量,一堆地址信息,使用hex视图去查看,如图:

ok,也就是每次使用上述地址去拿到off_6020A0字符里面的信息,开始编写脚本:
S = 'L3t_ME_T3ll_Y0u_S0m3th1ng_1mp0rtant_A_{FL4G}_W0nt_b3_3X4ctly_th4t_345y_t0_c4ptur3_H0wev3r_1T_w1ll_b3_C00l_1F_Y0u_g0t_1t'N = [0x24, 0x0, 0x5, 0x36, 0x65, 0x7, 0x27, 0x26, 0x2d, 0x1, 0x3, 0x0, 0x0d, 0x56, 0x1, 0x3, 0x65, 0x3, 0x2d, 0x16, 0x2,0x15, 0x3, 0x65, 0x0, 0x29, 0x44, 0x44, 0x1, 0x44, 0x2b]
flag = ''for i in N:flag += S[i]print(flag)
得到最终的结果:ALEXCTF{W3_L0v3_C_W1th_CL45535}