文章目录
- 一、DNS是什么
- 二、DNS的域名解析过程
- 三、搭建主辅DNS服务器
- 1.设置主DNS服务器
- 2.设置辅DNS服务器
- 四、访问控制,子域授权
- 五、使用bind搭建智能DNS
一、DNS是什么
DNS(Domain Name Service的缩写)的作用就是根据域名查出IP地址。IP地址是由32位二进制数字组成,人们很难记住这些IP,相反,大家愿意使用比较容易记忆的主机名字。而电脑在处理IP数据报文时,是使用IP地址的,因为它是固定长度。
DNS查询的类型对于客户端来说是递归查询,对于DNS服务器来说,绝大多数是迭代查询的。DNS名称解析中,从名称到IP的查询叫做正向解析,而从IP到名称的查询叫做反向解析。如果DNS服务器至少解析了一个或一个以上的域叫做DNS主服务器或者DNS辅助服务器,如果不负责任何解析叫做DNS缓存服务器。
现在互联网规模很大,DNS被设计成一个分布式的数据库系统,他分布的功能就是把一个大的数据库切割成很多小的数据库,来分别提供一部分数据的处理。全球一共分布了13台DNS根服务器,名字为A至M。
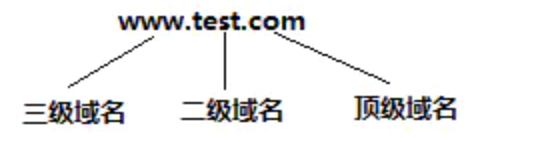
二、DNS的域名解析过程
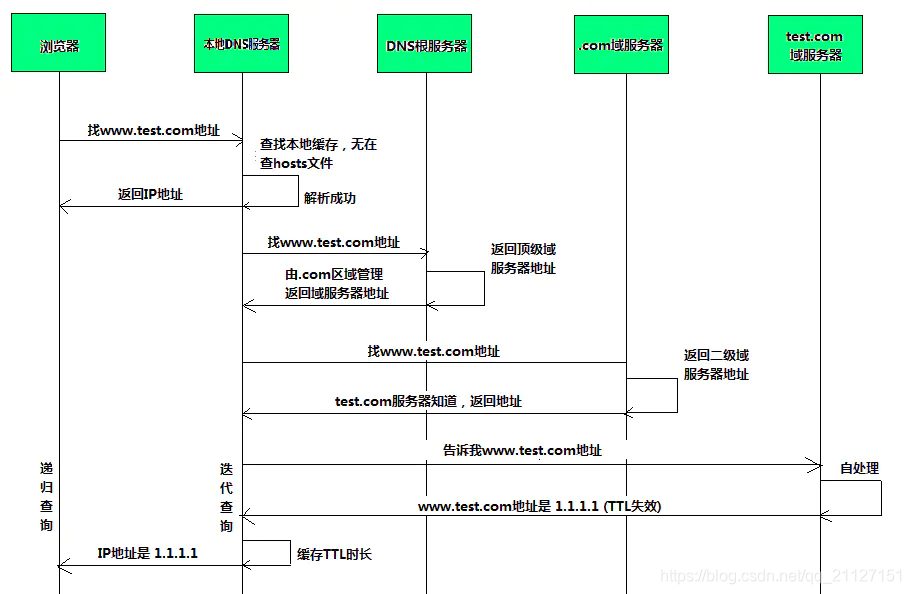
- 用户使用浏览器输入网址时域名解析过程:
- 客户访问时,先查自己的hosts文件,有则返回
- 客户hosts中没有就去查自己的缓存,有则返回
- 客户缓存没有就去找dns服务器
- dns服务器先找根服务器获得顶级域服务器地址
- dns服务器在找顶级域服务器去获得二级域服务器地址
- dns服务器从二级域服务器获得最终的IP地址
- 客户端从dns服务器中得到IP地址
DNS区域数据库文件
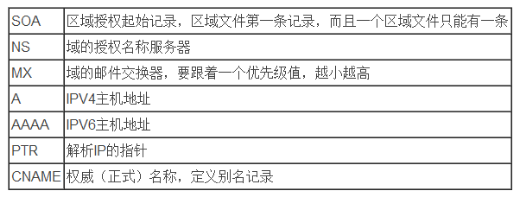
资源记录(Resource Record)的类型有以下几个:
*SOA:起始授权记录,只能有一个,必须放在第一条
- NS:域名服务记录,其中一个为主,可以有多个
- A:IPv4地址记录
- AAAA:IPv6地址记录
- CNAME:别名记录
- PTR:反向解析记录
- MX:邮件交换器
相关测试工具及命令
-
dig命令
用于测试DNS系统,其不会查询hosts文件,使用格式:
dig [-t RR_TYPE] name [@SERVER] [query options]
常用的查询选项包括:
+[no]trace:跟踪解析过程;
+[no]recurse:进行递归解析;
其常用用法包括:
反向解析测试:dig -x IP
测试区域传送:dig -t [axfr|ixfr] DOMAIN [@server] -
host命令
其用法类似于dig命令,使用格式为:
host [-t RR_TYPE] name SERVER_IP -
nslookup命令
nslookup命令有两种使用模式,一种是命令模式,另一个交互模式。
其命令模式的使用格式为:nslookup [-options] [name] [server]
而交互模式的使用格式为:
nslookup>
server IP:以指定的IP为DNS服务器进行查询;
set q=RR_TYPE:要查询的资源记录类型;
name:要查询的名称; -
rndc命令
rndc命令为named服务的控制命令,其常用的用法有以下:
rndc status:显示服务器状态
rndc reload:在不停止DNS服务器工作的情况下,重新加载配置文件和区域文件
rndc flush:清理DNS缓存 -
bind中的安全相关的配置
-
bind有四个内置的acl
none:没有一个主机;
any:任意主机;
local:本机;
localnet:本机所在的IP所属的网络; -
访问控制指令:
allow-query {}; 允许查询的主机;白名单;
allow-transfer {}; 允许向哪些主机做区域传送;默认为向所有主机;
allow-recursion {}; 允许哪些主机向当前DNS服务器发起递归查询请求;
allow-update {}; DDNS,允许动态更新区域数据库文件中内容;三、搭建主辅DNS服务器
环境说明
DNS主服务器:192.168.10.10
DNS辅服务器:192.168.10.11
DNS子域主服务器:192.168.10.12
1.设置主DNS服务器
安装软件
[root@localhost ~]# yum -y install bind #安装bind
[root@localhost ~]# yum -y install bind-utils #安装bind工具包
[root@localhost ~]# systemctl start named #启动服务
[root@localhost ~]# netstat -tunlp #查看状态
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 1323/named
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 891/sshd
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 1323/named
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 994/master
tcp6 0 0 ::1:53 :::* LISTEN 1323/named
tcp6 0 0 :::22 :::* LISTEN 891/sshd
tcp6 0 0 ::1:953 :::* LISTEN 1323/named
tcp6 0 0 ::1:25 :::* LISTEN 994/master
udp 0 0 127.0.0.1:53 0.0.0.0:* 1323/named
udp 0 0 127.0.0.1:323 0.0.0.0:* 639/chronyd
udp6 0 0 ::1:53 :::* 1323/named
udp6 0 0 ::1:323 :::* 639/chronyd
#其中53端口被监听,953端口被rndc监听
配置环境
[root@localhost ~]# vim /etc/resolv.conf #修改DNS配置文件
nameserver 192.168.10.10[root@localhost ~]# vim /etc/named.conf listen-on port 53 { 192.168.10.10; }; #修改监听通信地址IP
allow-query { any; }; #允许任何人连接,设置成any
dnssec-enable no;
dnssec-validation no;
#关闭dnssec,设置为no
配置解析一个正向区域
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "test.com" IN {type master; #定义主类型file "test.com.zone"; #这是相对路径,在/var/named下
};
建立区域数据文件
[root@localhost ~]# vim /var/named/test.com.zone
$TTL 3600
$ORIGIN test.com. #补一个后缀
@ IN SOA ns1.test.com. dnsadmin.test.com. (20180531011H10M3D1D )IN NS ns1 #前面有补后缀可以简写,否则写全称最后要有点号IN MX 10 mx1IN MX 20 mx2
ns1 IN A 192.168.10.10
MX1 IN A 192.168.10.21
MX2 IN A 192.168.10.22
www IN A 192.168.10.10
web IN CNAME www
bbs IN A 192.168.10.23
bbs IN A 192.168.10.24
修改权限,检测语法
[root@localhost ~]# chgrp named /var/named/test.com.zone
[root@localhost ~]# chmod o= /var/named/test.com.zone
#修改新键的区域数据文件权限
[root@localhost named]# named-checkconf
[root@localhost named]# named-checkzone test.com /var/named/test.com.zone
zone test.com/IN: loaded serial 2018053101
OK
#检测语法
服务器重载配置文件和区域数据文件
[root@localhost named]# rndc status
number of zones: 101
[root@localhost named]# rndc reload
server reload successful
[root@localhost named]# rndc status
number of zones: 102
#查看状态可以看到重载后数字加1
DNS主服务器正向解析测试
[root@localhost ~]# dig -t -A www.test.com
;; Warning, ignoring invalid type -A; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t -A www.test.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 18274
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.test.com. IN A;; ANSWER SECTION:
www.test.com. 3600 IN A 192.168.10.10;; AUTHORITY SECTION:
test.com. 3600 IN NS ns1.test.com.;; ADDITIONAL SECTION:
ns1.test.com. 3600 IN A 192.168.10.10;; Query time: 1 msec
;; SERVER: 192.168.10.10#53(192.168.10.10)
;; WHEN: Thu May 31 21:55:26 EDT 2018
;; MSG SIZE rcvd: 91
[root@localhost ~]# host -t A bbs.test.com
bbs.test.com has address 192.168.10.23
bbs.test.com has address 192.168.10.24
[root@localhost ~]# host -t A bbs.test.com
bbs.test.com has address 192.168.10.23
bbs.test.com has address 192.168.10.24
[root@localhost ~]# host -t A bbs.test.com
bbs.test.com has address 192.168.10.24
bbs.test.com has address 192.168.10.23
配置解析一个反向区域
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "10.168.192.in-addr.arpa" IN {type master;file "192.168.10.zone";
};
建立反向区域数据文件
[root@localhost ~]# vim /var/named/192.168.10.zone
$TTL 3600
$ORIGIN 10.168.192.in-addr.arpa.
@ IN SOA ns1.test.com. nsadmin.test.com. (20180601011H10M3D12H )IN NS ns1.test.com. #反向解析此处不能简写
10 IN PTR ns1.test.com.
21 IN PTR mx1.test.com.
22 IN PTR mx2.test.com.
23 IN PTR bbs.test.com.
24 IN PTR bbs.test.com.
10 IN PTR www.test.com.
修改反向区域文件权限,检测语法
[root@localhost named]# chgrp named /var/named/192.168.10.zone
[root@localhost named]# chmod o= /var/named/192.168.10.zone
[root@localhost named]# named-checkconf
[root@localhost named]# named-checkzone 10.168.192.in-addr.arpa /var/named/192.168.10.zone
zone 10.168.192.in-addr.arpa/IN: loaded serial 2018060101
OK
重载配置文件和区域数据文件
[root@localhost named]# rndc status
number of zones: 102
[root@localhost named]# rndc reload
server reload successful
[root@localhost named]# rndc status
number of zones: 103
主服务器反向解析测试
[root@localhost named]# dig -x 192.168.10.10; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -x 192.168.10.10
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 25958
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 1, ADDITIONAL: 2;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;10.10.168.192.in-addr.arpa. IN PTR;; ANSWER SECTION:
10.10.168.192.in-addr.arpa. 3600 IN PTR ns1.test.com.
10.10.168.192.in-addr.arpa. 3600 IN PTR www.test.com.;; AUTHORITY SECTION:
10.168.192.in-addr.arpa. 3600 IN NS ns1.test.com.;; ADDITIONAL SECTION:
ns1.test.com. 3600 IN A 192.168.10.10;; Query time: 1 msec
;; SERVER: 192.168.10.10#53(192.168.10.10)
;; WHEN: Thu May 31 22:26:03 EDT 2018
;; MSG SIZE rcvd: 129
2.设置辅DNS服务器
[root@localhost ~]# yum -y install bind bind-utils
[root@localhost ~]# systemctl start named.service[root@localhost ~]# vim /etc/resolv.conf
nameserver 192.168.10.11[root@localhost ~]# vim /etc/named.conf
listen-on port 53 { 192.168.10.11; };
allow-query { any; };
dnssec-enable no;
dnssec-validation no;
配置11辅服务器的正向区域
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "test.com" IN { #正向区域type slave;file "slaves/test.com.zone"; #区域数据文件位置masters { 192.168.10.10; }; #定义正向区域主服务器IP
};
[root@localhost ~]# named-checkconf
来到10主服务器上去配置文件
[root@localhost ~]# vim /var/named/test.com.zone
$TTL 3600
$ORIGIN test.com.
@ IN SOA ns1.test.com. dnsadmin.test.com. (2018053102 #每次修改文件时手动加1,从服务器才会更新1H10M3D1D )IN NS ns1IN NS ns2 #增加A记录指向11辅服务器IN MX 10 mx1IN MX 20 mx2
ns1 IN A 192.168.10.10
ns2 IN A 192.168.10.11 #辅服务器IP
MX1 IN A 192.168.10.21
MX2 IN A 192.168.10.22
www IN A 192.168.10.10
web IN CNAME www
bbs IN A 192.168.10.23
bbs IN A 192.168.10.24[root@localhost ~]# named-checkzone test.com /var/named/test.com.zone
zone test.com/IN: loaded serial 2018053102
OK
[root@localhost ~]# rndc reload
server reload successful
[root@localhost ~]# rndc status
server is up and running
#检测语法,检测状态都正常
来到11辅服务器
[root@localhost ~]# rndc reload
server reload successful
[root@localhost slaves]# ll /var/named/slaves/
total 4
-rw-r--r-- 1 named named 533 May 31 23:17 test.com.zone
#正向区域数据文件已经同步过来
测试用11辅服务器解析网址
[root@localhost slaves]# dig -t A www.test.com @192.168.10.11; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t A www.test.com @192.168.10.11
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 45851
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.test.com. IN A;; ANSWER SECTION:
www.test.com. 3600 IN A 192.168.10.10;; AUTHORITY SECTION:
test.com. 3600 IN NS ns2.test.com.
test.com. 3600 IN NS ns1.test.com.;; ADDITIONAL SECTION:
ns1.test.com. 3600 IN A 192.168.10.10
ns2.test.com. 3600 IN A 192.168.10.11;; Query time: 0 msec
;; SERVER: 192.168.10.11#53(192.168.10.11)
;; WHEN: Thu May 31 23:20:16 EDT 2018
;; MSG SIZE rcvd: 125
进一步对主辅服务器进行测试,来到10主服务器
[root@localhost ~]# vim /var/named/test.com.zone
$TTL 3600
$ORIGIN test.com.
@ IN SOA ns1.test.com. dnsadmin.test.com. (2018053103 #序列号加11H10M3D1D )IN NS ns1IN NS ns2IN MX 10 mx1IN MX 20 mx2
ns1 IN A 192.168.10.10
ns2 IN A 192.168.10.11
MX1 IN A 192.168.10.21
MX2 IN A 192.168.10.22
www IN A 192.168.10.10
web IN CNAME www
bbs IN A 192.168.10.23
bbs IN A 192.168.10.24
pop3 IN A 192.168.10.25 #增加一条A记录[root@localhost ~]# rndc reload
server reload successful
#重载配置
来到11辅服务器
[root@localhost ~]# systemctl status named.service
● named.service - Berkeley Internet Name Domain (DNS)Loaded: loaded (/usr/lib/systemd/system/named.service; disabled; vendor preset: disabled)Active: active (running) since Thu 2018-05-31 22:38:36 EDT; 54min agoProcess: 1090 ExecStart=/usr/sbin/named -u named -c ${NAMEDCONF} $OPTIONS (code=exited, status=0/SUCCESS)Process: 1087 ExecStartPre=/bin/bash -c if [ ! "$DISABLE_ZONE_CHECKING" == "yes" ]; then /usr/sbin/named-checkconf -z "$NAMEDCONF"; else echo "Checking of zone files is disabled"; fi (code=exited, status=0/SUCCESS)Main PID: 1093 (named)CGroup: /system.slice/named.service└─1093 /usr/sbin/named -u named -c /etc/named.confMay 31 23:17:11 localhost.localdomain named[1093]: zone test.com/IN: transferred serial 2018053102
May 31 23:17:11 localhost.localdomain named[1093]: transfer of 'test.com/IN' from 192.168.10.10#53: Transfer completed.../sec)
May 31 23:17:11 localhost.localdomain named[1093]: zone test.com/IN: sending notifies (serial 2018053102)
May 31 23:30:31 localhost.localdomain named[1093]: client 192.168.10.10#2372: received notify for zone 'test.com'
May 31 23:30:31 localhost.localdomain named[1093]: zone test.com/IN: refresh: unexpected rcode (REFUSED) from master 1....0#0)
May 31 23:30:31 localhost.localdomain named[1093]: zone test.com/IN: Transfer started.
May 31 23:30:31 localhost.localdomain named[1093]: transfer of 'test.com/IN' from 192.168.10.10#53: connected using 19...46792
May 31 23:30:31 localhost.localdomain named[1093]: zone test.com/IN: transferred serial 2018053103
May 31 23:30:31 localhost.localdomain named[1093]: transfer of 'test.com/IN' from 192.168.10.10#53: Transfer completed.../sec)
May 31 23:30:31 localhost.localdomain named[1093]: zone test.com/IN: sending notifies (serial 2018053103)
Hint: Some lines were ellipsized, use -l to show in full.
#辅服务器不需要reload,此时看到自动更新到新序列号,文件也传输过来了
[root@localhost ~]# dig -t A pop3.test.com @192.168.10.11; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t A pop3.test.com @192.168.10.11
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 24355
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;pop3.test.com. IN A;; ANSWER SECTION:
pop3.test.com. 3600 IN A 192.168.10.25;; AUTHORITY SECTION:
test.com. 3600 IN NS ns1.test.com.
test.com. 3600 IN NS ns2.test.com.;; ADDITIONAL SECTION:
ns1.test.com. 3600 IN A 192.168.10.10
ns2.test.com. 3600 IN A 192.168.10.11;; Query time: 1 msec
;; SERVER: 192.168.10.11#53(192.168.10.11)
;; WHEN: Thu May 31 23:54:58 EDT 2018
;; MSG SIZE rcvd: 126
配置11辅服务器反向区域
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "10.168.192.in-addr.arpa" IN {type slave;file "slaves/192.168.10.zone";masters { 192.168.10.10; };
};[root@localhost ~]# named-checkconf
配置10主服务器反向区域的数据文件
[root@localhost ~]# vim /var/named/192.168.10.zone
$TTL 3600
$ORIGIN 10.168.192.in-addr.arpa.
@ IN SOA ns1.test.com. nsadmin.test.com. (20180601021H10M3D12H )IN NS ns1.test.com.IN NS ns2.test.com. #增加PTR记录指向11辅服务器
10 IN PTR ns1.test.com.
11 IN PTR ns2.test.com. #11辅服务器名称
21 IN PTR mx1.test.com.
22 IN PTR mx2.test.com.
23 IN PTR bbs.test.com.
24 IN PTR bbs.test.com.
10 IN PTR www.test.com.[root@localhost ~]# named-checkzone 10.168.192.in-addr.arpa /var/named/192.168.10.zone
zone 10.168.192.in-addr.arpa/IN: loaded serial 2018060102
OK
[root@localhost ~]# rndc reload
server reload successful
#检测语法,重载配置
来到11辅服务器
[root@localhost ~]# rndc reload
server reload successful
[root@localhost ~]# ll /var/named/slaves/
total 8
-rw-r--r-- 1 named named 600 Jun 1 02:23 192.168.10.zone
-rw-r--r-- 1 named named 574 Jun 1 02:10 test.com.zone
#反向区域的数据文件也已经同步过来
测试在11辅服务器反向解析IP
[root@localhost ~]# dig -x 192.168.10.10 @192.168.10.11; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -x 192.168.10.10 @192.168.10.11
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 50592
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 3;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;10.10.168.192.in-addr.arpa. IN PTR;; ANSWER SECTION:
10.10.168.192.in-addr.arpa. 3600 IN PTR ns1.test.com.
10.10.168.192.in-addr.arpa. 3600 IN PTR www.test.com.;; AUTHORITY SECTION:
10.168.192.in-addr.arpa. 3600 IN NS ns2.test.com.
10.168.192.in-addr.arpa. 3600 IN NS ns1.test.com.;; ADDITIONAL SECTION:
ns1.test.com. 3600 IN A 192.168.10.10
ns2.test.com. 3600 IN A 192.168.10.11;; Query time: 1 msec
;; SERVER: 192.168.10.11#53(192.168.10.11)
;; WHEN: Fri Jun 01 02:25:17 EDT 2018
;; MSG SIZE rcvd: 163
进一步主辅同步测试,在10主中添加一条PTR
[root@localhost ~]# vim /var/named/192.168.10.zone
$TTL 3600
$ORIGIN 10.168.192.in-addr.arpa.
@ IN SOA ns1.test.com. nsadmin.test.com. (2018060103 #序列号加11H10M3D12H )IN NS ns1.test.com.IN NS ns2.test.com.
10 IN PTR ns1.test.com.
11 IN PTR ns2.test.com.
21 IN PTR mx1.test.com.
22 IN PTR mx2.test.com.
23 IN PTR bbs.test.com.
24 IN PTR bbs.test.com.
10 IN PTR www.test.com.
25 IN PTR pop3.test.com. #增加一条RTR数据[root@localhost ~]# rndc reload
server reload successful
在11辅服务器测试
[root@localhost ~]# dig -x 192.168.10.25 @192.168.10.11; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -x 192.168.10.25 @192.168.10.11
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35322
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;25.10.168.192.in-addr.arpa. IN PTR;; ANSWER SECTION:
25.10.168.192.in-addr.arpa. 3600 IN PTR pop3.test.com.;; AUTHORITY SECTION:
10.168.192.in-addr.arpa. 3600 IN NS ns1.test.com.
10.168.192.in-addr.arpa. 3600 IN NS ns2.test.com.;; ADDITIONAL SECTION:
ns1.test.com. 3600 IN A 192.168.10.10
ns2.test.com. 3600 IN A 192.168.10.11;; Query time: 1 msec
;; SERVER: 192.168.10.11#53(192.168.10.11)
;; WHEN: Fri Jun 01 02:36:48 EDT 2018
;; MSG SIZE rcvd: 150
手动测试区域传送功能
[root@localhost ~]# dig -t axfr test.com @192.168.10.11; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t axfr test.com @192.168.10.11
;; global options: +cmd
test.com. 3600 IN SOA ns1.test.com. dnsadmin.test.com. 2018053103 3600 600 259200 86400
test.com. 3600 IN MX 10 mx1.test.com.
test.com. 3600 IN MX 20 mx2.test.com.
test.com. 3600 IN NS ns1.test.com.
test.com. 3600 IN NS ns2.test.com.
bbs.test.com. 3600 IN A 192.168.10.23
bbs.test.com. 3600 IN A 192.168.10.24
MX1.test.com. 3600 IN A 192.168.10.21
MX2.test.com. 3600 IN A 192.168.10.22
ns1.test.com. 3600 IN A 192.168.10.10
ns2.test.com. 3600 IN A 192.168.10.11
pop3.test.com. 3600 IN A 192.168.10.25
web.test.com. 3600 IN CNAME www.test.com.
www.test.com. 3600 IN A 192.168.10.10
test.com. 3600 IN SOA ns1.test.com. dnsadmin.test.com. 2018053103 3600 600 259200 86400
;; Query time: 1 msec
;; SERVER: 192.168.10.11#53(192.168.10.11)
;; WHEN: Fri Jun 01 02:40:11 EDT 2018
;; XFR size: 15 records (messages 1, bytes 350)
[root@localhost ~]# dig -t axfr 10.168.192.in-addr.arpa @192.168.10.10; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t axfr 10.168.192.in-addr.arpa @192.168.10.10
;; global options: +cmd
10.168.192.in-addr.arpa. 3600 IN SOA ns1.test.com. nsadmin.test.com. 2018060103 3600 600 259200 43200
10.168.192.in-addr.arpa. 3600 IN NS ns1.test.com.
10.168.192.in-addr.arpa. 3600 IN NS ns2.test.com.
10.10.168.192.in-addr.arpa. 3600 IN PTR ns1.test.com.
10.10.168.192.in-addr.arpa. 3600 IN PTR www.test.com.
11.10.168.192.in-addr.arpa. 3600 IN PTR ns2.test.com.
21.10.168.192.in-addr.arpa. 3600 IN PTR mx1.test.com.
22.10.168.192.in-addr.arpa. 3600 IN PTR mx2.test.com.
23.10.168.192.in-addr.arpa. 3600 IN PTR bbs.test.com.
24.10.168.192.in-addr.arpa. 3600 IN PTR bbs.test.com.
25.10.168.192.in-addr.arpa. 3600 IN PTR pop3.test.com.
10.168.192.in-addr.arpa. 3600 IN SOA ns1.test.com. nsadmin.test.com. 2018060103 3600 600 259200 43200
;; Query time: 2 msec
;; SERVER: 192.168.10.10#53(192.168.10.10)
;; WHEN: Fri Jun 01 02:42:53 EDT 2018
;; XFR size: 12 records (messages 1, bytes 319)
这种开放式的区域传送对服务器有巨大的风险,我们需要配置访问控制,让主服务器只开放给辅服务器做传送
四、访问控制,子域授权
配置192.168.10.12子域主服务器流程:
首先到192.168.10.10主服务器中添加子域服务器的数据
[root@localhost ~]# vim /var/named/test.com.zone
$ORIGIN test.com.
@ IN SOA ns1.test.com. dnsadmin.test.com. (2018053104 #序列号加11H10M3D1D )IN NS ns1IN NS ns2IN MX 10 mx1IN MX 20 mx2
ops IN NS ns1.ops #增加子域服务器
ns1 IN A 192.168.10.10
ns2 IN A 192.168.10.11
MX1 IN A 192.168.10.21
MX2 IN A 192.168.10.22
www IN A 192.168.10.10
web IN CNAME www
bbs IN A 192.168.10.23
bbs IN A 192.168.10.24
ns1.ops IN A 192.168.10.12 #增加子域服务器A标记
配置12子域服务器
[root@localhost ~]# yum -y install bind bind-utils
[root@localhost ~]# systemctl start named.service[root@localhost ~]# vim /etc/resolv.conf
nameserver 192.168.10.12[root@localhost ~]# vim /etc/named.conf
listen-on port 53 { 127.0.0.1; 192.168.10.12; };
//allow-query { localhost; }; #注释掉这一行
dnssec-enable no;
dnssec-validation no;[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "ops.test.com" IN {type master;file "ops.test.com.zone";
};
#增加三级域,增加正向区域的子域[root@localhost ~]# vim /etc/named/ops.test.com.zone$TTL 3600
$ORIGIN ops.test.com.
@ IN SOA ns1.ops.test.com. nsadmin.ops.test.com. (20180601011H10M1D2H )IN NS ns1
ns1 IN A 192.168.10.12
www IN A 192.168.10.12[root@localhost ~]# chgrp named /var/named/ops.test.com.zone
[root@localhost ~]# chmod o= /var/named/ops.test.com.zone
[root@localhost ~]# named-checkconf
[root@localhost ~]# named-checkzone ops.test.com /var/named/ops.test.com.zone
zone ops.test.com/IN: loaded serial 2018060101
OK[root@localhost ~]# rndc reload
server reload successful
测试
[root@localhost ~]# dig -t A www.ops.test.com @192.168.10.12; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t A www.ops.test.com @192.168.10.12
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 13329
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.ops.test.com. IN A;; ANSWER SECTION:
www.ops.test.com. 3600 IN A 192.168.10.12;; AUTHORITY SECTION:
ops.test.com. 3600 IN NS ns1.ops.test.com.;; ADDITIONAL SECTION:
ns1.ops.test.com. 3600 IN A 192.168.10.12;; Query time: 1 msec
;; SERVER: 192.168.10.12#53(192.168.10.12)
;; WHEN: Fri Jun 01 03:45:00 EDT 2018
;; MSG SIZE rcvd: 95
子域服务器解析www.test.com时,因自己不能解析默认会去互联网根域上去迭代查询
[root@localhost ~]# dig -t A www.test.com @192.168.10.12; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t A www.test.com @192.168.10.12
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 32424
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.test.com. IN A;; ANSWER SECTION:
www.test.com. 3579 IN A 69.172.200.235;; AUTHORITY SECTION:
test.com. 172779 IN NS ns66.worldnic.com.
test.com. 172779 IN NS ns65.worldnic.com.;; ADDITIONAL SECTION:
ns65.worldnic.com. 172779 IN A 207.204.40.133
ns66.worldnic.com. 172779 IN A 207.204.21.133;; Query time: 1 msec
;; SERVER: 192.168.10.12#53(192.168.10.12)
;; WHEN: Fri Jun 01 21:06:53 EDT 2018
;; MSG SIZE rcvd: 136
子域定义转发域到主辅服务器,test.com会转发到主辅服务器中解析
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "test.com" IN {type forward;forward only;forwarders { 192.168.10.10; 192.168.10.11; };
};
#在配置文件末尾添加这段转发规则[root@localhost ~]# rndc reload
server reload successful
[root@localhost ~]# rndc flush
#清空缓存
此时可以解析出正确的IP
[root@localhost ~]# dig -t A www.test.com @192.168.10.12; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t A www.test.com @192.168.10.12
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 63618
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.test.com. IN A;; ANSWER SECTION:
www.test.com. 3600 IN A 192.168.10.10;; AUTHORITY SECTION:
test.com. 3600 IN NS ns2.test.com.
test.com. 3600 IN NS ns1.test.com.;; ADDITIONAL SECTION:
ns2.test.com. 3600 IN A 192.168.10.11
ns1.test.com. 3600 IN A 192.168.10.10;; Query time: 6 msec
;; SERVER: 192.168.10.12#53(192.168.10.12)
;; WHEN: Fri Jun 01 21:23:08 EDT 2018
;; MSG SIZE rcvd: 125
上面是对特定区域的区域转发解析请求,也可以配置本地不能解析的全部转给其他服务器来解析的全局转发
[root@localhost ~]# vim /etc/named.conf
forward only;
forwarders { 192.168.10.10; }; #在options代码段中添加这两行指令
#并删除掉上面的区域转发规则[root@localhost ~]# rndc reload
[root@localhost ~]# rndc flush
[root@localhost ~]# dig -t A www.test.com @192.168.10.12; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t A www.test.com @192.168.10.12
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 9713
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.test.com. IN A;; ANSWER SECTION:
www.test.com. 3560 IN A 192.168.10.10;; AUTHORITY SECTION:
test.com. 3560 IN NS ns2.test.com.
test.com. 3560 IN NS ns1.test.com.;; ADDITIONAL SECTION:
ns2.test.com. 3560 IN A 192.168.10.11
ns1.test.com. 3560 IN A 192.168.10.10;; Query time: 1 msec
;; SERVER: 192.168.10.12#53(192.168.10.12)
;; WHEN: Fri Jun 01 21:47:02 EDT 2018
;; MSG SIZE rcvd: 125
配置访问控制命令
[root@localhost ~]# vim /etc/named.rfc1912.zones
zone "test.com" IN {type master;file "test.com.zone";allow-transfer { slaves; };
};[root@localhost ~]# vim /etc/named.conf
acl slaves {192.168.10.11;
};
#在options前面加上这一段
上面的访问控制列表中没有12服务器,所以用12传输失败
[root@localhost ~]# dig -t axfr test.com @192.168.10.12; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t axfr test.com @192.168.10.12
;; global options: +cmd
; Transfer failed.
服务器只允许列表中网段主机可以执行递归查询
[root@localhost ~]# vim /etc/named.conf
acl mynet {192.168.10.0/24;127.0.0.0/8;
};
#在options前面加上这一段
allow-recuresion { mynet; };
#recursion yes;修改这上面这句
五、使用bind搭建智能DNS
要实现DNS服务器的智能解析,需要先理解一个概念:view
假如有台web主机,www.test.com是域名,它有两个IP,一个接内网IP为192.168.10.10,一个接外网IP为1.1.1.1。来自互联网的用户会解析成1.1.1.1,而来自内网的用户不需要解析成外网IP在连进来,只需要直接解析成内网IP192.168.10.10就可以了。这种根据客户端的不同来源将同一个主机解析成不同的结果,就叫做view。
修改主DNS的named.conf配置文件
[root@localhost ~]# vim /etc/named.conf
options {
......
};
logging {
......
};
view internal {match-clients { 192.168.10.11; };#设置此IP解析成外网zone "." IN {type hint;file "named.ca";};zone "test.com" IN {type master;file "test.com/internal";};include "/etc/named.rfc1912.zones";include "/etc/named.root.key";
};
view external {match-clients { any; };#除了上面的IP范围,其他所有IP解析成内网zone "." IN {type hint;file "named.ca";};zone "test.com" IN {type master;file "test.com/external";};include "/etc/named.rfc1912.zones";include "/etc/named.root.key";
};
建立两个正向区域数据文件
[root@localhost ~]# vim /var/named/test.com/internal
$TTL 3600
$ORIGIN test.com.
@ IN SOA ns1.test.com. dnsadmin.test.com. (20180531011H10M3D1D )IN NS ns1
ns1 IN A 192.168.10.10
www IN A 1.1.1.1
web IN CNAME www
bbs IN A 1.1.1.2
bbs IN A 1.1.1.3[root@localhost ~]# vim /var/named/test.com/external
$TTL 3600
$ORIGIN test.com.
@ IN SOA ns1.test.com. dnsadmin.test.com. (20180531011H10M3D1D )IN NS ns1
ns1 IN A 192.168.10.10
www IN A 192.168.10.10
web IN CNAME www
bbs IN A 192.168.10.23
bbs IN A 192.168.10.24
检测语法并设置权限
[root@localhost ~]# named-checkconf
[root@localhost ~]# named-checkzone test.com /var/named/test.com/internal
zone test.com/IN: loaded serial 2018053101
OK
[root@localhost ~]# named-checkzone test.com /var/named/test.com/external
zone test.com/IN: loaded serial 2018053101
OK
[root@localhost ~]# chgrp named /var/named/test.com/{internal,external}
[root@localhost ~]# chmod o= /var/named/test.com/{internal,external}[root@localhost ~]# rndc reload
server reload successful
用192.168.10.12进行解析,解析成内网IP
[root@localhost ~]# dig -t A www.test.com @192.168.10.10; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t A www.test.com @192.168.10.10
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 47742
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.test.com. IN A;; ANSWER SECTION:
www.test.com. 3600 IN A 192.168.10.10;; AUTHORITY SECTION:
test.com. 3600 IN NS ns1.test.com.;; ADDITIONAL SECTION:
ns1.test.com. 3600 IN A 192.168.10.10;; Query time: 2 msec
;; SERVER: 192.168.10.10#53(192.168.10.10)
;; WHEN: Sat Jun 02 02:45:02 EDT 2018
;; MSG SIZE rcvd: 91[root@localhost ~]# dig -t A bbs.test.com @192.168.10.10; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t A bbs.test.com @192.168.10.10
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 36168
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 1, ADDITIONAL: 2;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;bbs.test.com. IN A;; ANSWER SECTION:
bbs.test.com. 3600 IN A 192.168.10.24
bbs.test.com. 3600 IN A 192.168.10.23;; AUTHORITY SECTION:
test.com. 3600 IN NS ns1.test.com.;; ADDITIONAL SECTION:
ns1.test.com. 3600 IN A 192.168.10.10;; Query time: 1 msec
;; SERVER: 192.168.10.10#53(192.168.10.10)
;; WHEN: Sat Jun 02 02:45:20 EDT 2018
;; MSG SIZE rcvd: 107
用192.168.10.11进行解析,解析成外网IP
[root@localhost ~]# dig -t A www.test.com @192.168.10.10; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t A www.test.com @192.168.10.10
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 39708
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.test.com. IN A;; ANSWER SECTION:
www.test.com. 3600 IN A 1.1.1.1;; AUTHORITY SECTION:
test.com. 3600 IN NS ns1.test.com.;; ADDITIONAL SECTION:
ns1.test.com. 3600 IN A 192.168.10.10;; Query time: 1 msec
;; SERVER: 192.168.10.10#53(192.168.10.10)
;; WHEN: Sat Jun 02 02:47:01 EDT 2018
;; MSG SIZE rcvd: 91[root@localhost ~]# dig -t A bbs.test.com @192.168.10.10; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7 <<>> -t A bbs.test.com @192.168.10.10
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 44362
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 1, ADDITIONAL: 2;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;bbs.test.com. IN A;; ANSWER SECTION:
bbs.test.com. 3600 IN A 1.1.1.2
bbs.test.com. 3600 IN A 1.1.1.3;; AUTHORITY SECTION:
test.com. 3600 IN NS ns1.test.com.;; ADDITIONAL SECTION:
ns1.test.com. 3600 IN A 192.168.10.10;; Query time: 1 msec
;; SERVER: 192.168.10.10#53(192.168.10.10)
;; WHEN: Sat Jun 02 02:47:24 EDT 2018
;; MSG SIZE rcvd: 107