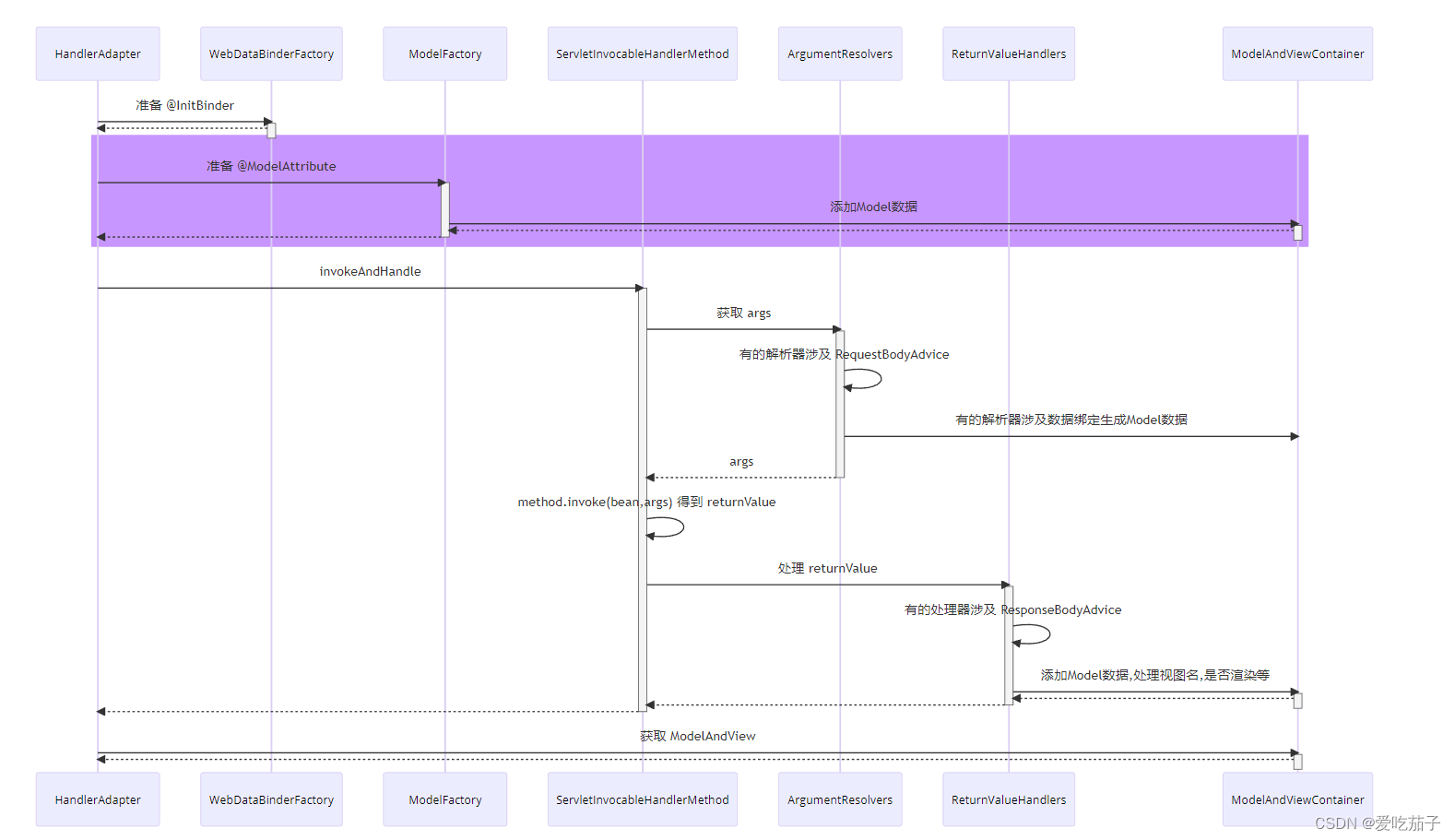
上一篇讲解了加密解密,这次来个加签验签,实际项目里,我们采用的是react 和nodejs 来进行加签验签,用的jsrsasign库,下面贴点核心代码
react加签
nodejs验签

实际应用在nodejs层可以将时间戳和sign签名验证通过剔除掉,所以对后端就是无感的。
下面来介绍下客户端见加签验签,前面的代码也有,以java为例
import org.apache.commons.codec.binary.Base64;import javax.crypto.Cipher;
import java.security.*;
import java.security.spec.PKCS8EncodedKeySpec;
import java.security.spec.X509EncodedKeySpec;
/*** @author ALvis* @ctreate 2019/11/26*/
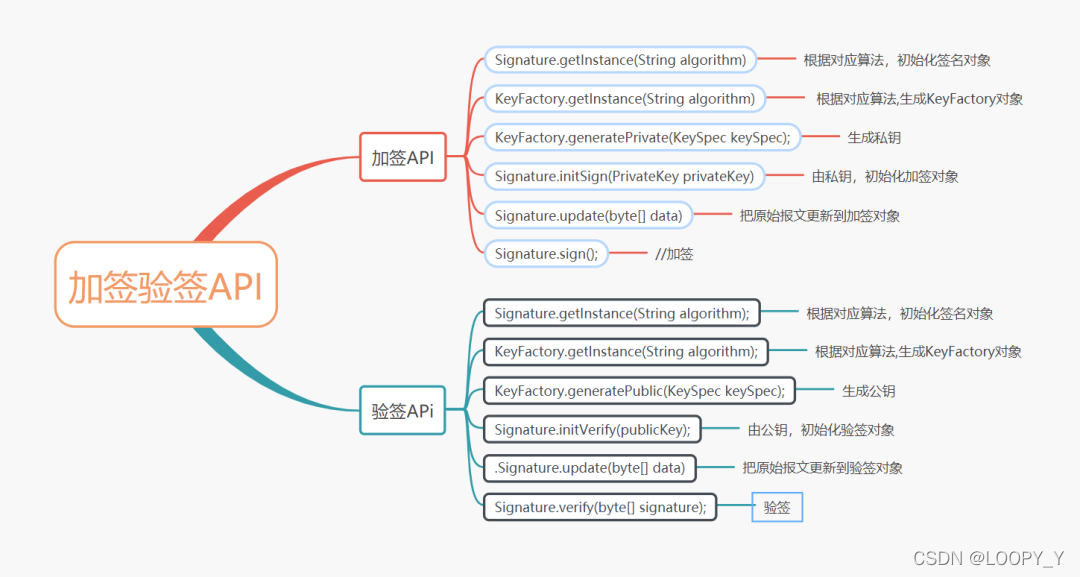
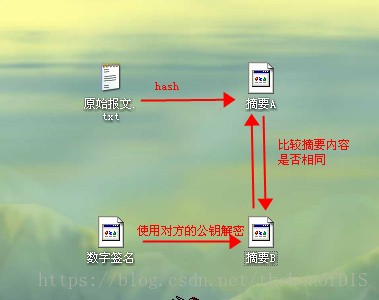
public class RSACoder {public static final String KEY_ALGORITHM = "RSA";public static final String SIGNATURE_ALGORITHM = "MD5withRSA";public static byte[] decryptBASE64(String key) {return Base64.decodeBase64(key);}public static String encryptBASE64(byte[] bytes) {return Base64.encodeBase64String(bytes);}/*** 用私钥对信息生成数字签名** @param data 加密数据* @param privateKey 私钥* @return* @throws Exception*/public static String sign(byte[] data, String privateKey) throws Exception {// 解密由base64编码的私钥byte[] keyBytes = decryptBASE64(privateKey);// 构造PKCS8EncodedKeySpec对象PKCS8EncodedKeySpec pkcs8KeySpec = new PKCS8EncodedKeySpec(keyBytes);// KEY_ALGORITHM 指定的加密算法KeyFactory keyFactory = KeyFactory.getInstance(KEY_ALGORITHM);// 取私钥匙对象PrivateKey priKey = keyFactory.generatePrivate(pkcs8KeySpec);// 用私钥对信息生成数字签名Signature signature = Signature.getInstance(SIGNATURE_ALGORITHM);signature.initSign(priKey);signature.update(data);return encryptBASE64(signature.sign());}/*** 校验数字签名** @param data 加密数据* @param publicKey 公钥* @param sign 数字签名* @return 校验成功返回true 失败返回false* @throws Exception*/public static boolean verify(byte[] data, String publicKey, String sign)throws Exception {// 解密由base64编码的公钥byte[] keyBytes = decryptBASE64(publicKey);// 构造X509EncodedKeySpec对象X509EncodedKeySpec keySpec = new X509EncodedKeySpec(keyBytes);// KEY_ALGORITHM 指定的加密算法KeyFactory keyFactory = KeyFactory.getInstance(KEY_ALGORITHM);// 取公钥匙对象PublicKey pubKey = keyFactory.generatePublic(keySpec);Signature signature = Signature.getInstance(SIGNATURE_ALGORITHM);signature.initVerify(pubKey);signature.update(data);// 验证签名是否正常return signature.verify(decryptBASE64(sign));}
}下面是测试代码
public class Test2 {private static final String publicKey="MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCHuKQKF9zgk3Y2OOeULroJnP4qHOGw/Jh/3+vKIqpXqZjjk2RW+eJLScHMWSxeZ+vwiboETGMlgSovywQN7qph6r10btW/V6B1PvHZr57N1nJ1MxtrIWKKYJKVUMZtwkhGes65YtZ7rMDMvCRas/3sP8NixHV8RYNm/KrnMknoAQIDAQAB";private static final String privateKey = "MIICdgIBADANBgkqhkiG9w0BAQEFAASCAmAwggJcAgEAAoGBAIe4pAoX3OCTdjY455Quugmc/ioc4bD8mH/f68oiqlepmOOTZFb54ktJwcxZLF5n6/CJugRMYyWBKi/LBA3uqmHqvXRu1b9XoHU+8dmvns3WcnUzG2shYopgkpVQxm3CSEZ6zrli1nuswMy8JFqz/ew/w2LEdXxFg2b8qucySegBAgMBAAECgYBW9BEE9mzo5REjhCm6YoWGizK7wG1Ie00pAEmM49DHAT2W8GOk5cv5+HNVfPxUL7iWD2dCQb5z1OE2ZZdfZb16q9YdAXxTt90exoDX8q4i0xWTKPooVni8+tdypzizw0m3XN/adq6RC4Hz8Xc5n6RTl+1rAGc60AkTmmhZaAx0EQJBAP6+yegOa9uQS06ww+pWZKO+hm3kIPunIkYlN3Y7KkPCOJq4WiS7D/oIyBYIBG/UltloF3ROOIf3uMROvdcvlE8CQQCIY8X3ICn5p+Ot32V/ZhT0aebUKGFvG9b/Zx072xEumG0xIhtOic1Vr10hvPYckWbJcEY6s+oeiXzi9CwutJqvAkEA4N+SZCK2228YyzIG/8mbtV/uUvtakksLWlhoCRpZSM8eIJY0HNB0Xgd6eNhC8mT7dJcKfUS/amcm10ObGWWKyQJATo/aGk1GoG3ase66UjYE3/yYX6Ca7xtELn3A0xeOwB5A10pkHEs4IaEPrj1gLnh6kpG/glTcCJb9fuVTBdw2NQJALFt2PMr8PwPKnV74MZFcKGlF7Qz31SIAPBgClsS/bUweJ/3lw9Xopv0WO8INdSqgwjAX2+PjDwOiwBYtD7bPNw==";@Testpublic void test1() throws Exception{EvalUser user = new EvalUser();user.setUserid("001");user.setUsername("alvis");user.setOrgId("111");user.setLevel("222");String content = JSON.toJSONString(user);String sign = RSACoder.sign(content.getBytes(), privateKey);String lastSign = URLEncoder.encode(sign.replace("\n", ""), "UTF-8");System.out.println("签名内容:" + content);System.out.println("最终签名:" + lastSign);// 签名验证String test ="{\"level\":\"222\",\"orgId\":\"111\",\"userid\":\"001\",\"username\":\"alvis\"}";boolean bverify = RSACoder.verify(test.getBytes(), publicKey, URLDecoder.decode(lastSign, "UTF-8"));System.out.println("验证结果:" + bverify +";decode sign="+URLDecoder.decode(lastSign, "UTF-8"));}
}加签验签一般失败的原因就是json转换时的顺序,比如用fastjson转换成字符串加签,那么解签时就要注意,把json转成字符串的排序是否一致,同是fastjson排序规则也会随着版本的改变而不同,解决方案之一就是要么用同版本的工具,要么可以结合加密解密来进行。