Nikto简介
Nikto是一个简单的开源Web服务器扫描程序,可以检查网站并报告它发现的可能用于利用或破解网站的漏洞。此外,它是业界使用最广泛的网站漏洞工具之一,并且在许多圈子中被认为是行业标准。
虽然这个工具非常有效,但它根本不是隐秘的。任何具有入侵检测系统或其他安全措施的站点都将检测到它正在被扫描。最初设计只是用于安全测试,并不在意隐形问题。
【Nikto-百度百科】

Nikto使用教程
一、安装Nikto
在Kali Linux上,会预装Nikto,因此无需下载或安装任何东西,它在分类“Vulnerability Analysi”中。如果由于某种原因没有安装Nikto,可以从GitHub获取Nikto 或使用apt install命令安装。
apt install nikto如果在Mac上执行此操作,则可以使用Homebrew安装Nikto。
brew install nikto
二、Nikto使用
在使用Nikto深入扫描Web服务器之前,先使用-Help选项查看Nikto所有操作命令和功能。
nikto -Help
三、基本使用语法
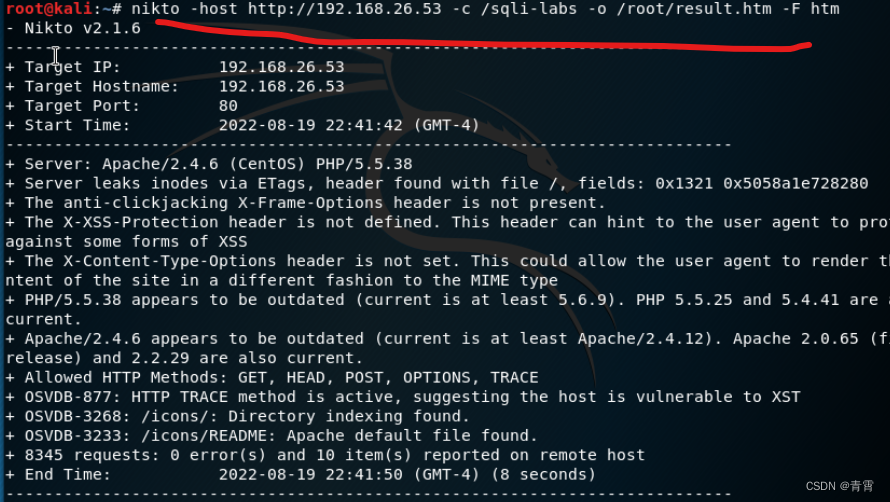
从上一步可以看出,Nikto有很多功能选项,基本语法如下。我们将<IP or hostname>替换为实际IP地址或主机名sans尖括号。
nikto -h <IP or hostname>Nikto能够进行扫描SSL和端口443(HTTPS网站使用的端口)(HTTP默认使用端口80)。因此,我们可以扫描使用了SSL的网站。
如果知道它是SSL网站,可以在Nikto中指定它,通过在命令末尾添加-ssl来节省扫描时间。
nikto -h <IP or hostname> -ssl
四、扫描使用SSL的网站
以pbs.org为例:
nikto -h pbs.org -ssl- Nikto v2.1.6
------------------------------------------------------------------------------
- STATUS: Starting up!
+ Target IP: 54.225.198.196
+ Target Hostname: pbs.org
+ Traget Port: 443
------------------------------------------------------------------------------
+ SSl Info: Subject: /CN=www.pbs.orgAltnames: account.pbs.org, admin.pgs.org, dipsy-tc.pbs.org, docs.pbs.org, ga.video.cdn.pbs.org, git.pbs.org, heart.ops.pbs.org, hub-dev.pbs.org, image.pbs.org,jaws..pbs.org, kids.pbs.org, koth-qa.svp.pbs.org, login.pbs.org, ops.pbs.org, pbs.org, player.pbs.org, projects.pbs.org, sentry.pbs.org, teacherline.pbs.org,urs.pbs.org, video.pbs.org, weta-qa.svp.pbs.org, whut-qa.svp.pbs.org, wnet.video-qa.pbs.org, wnet.video-staging.pbs.org, www-cache.pbs.org, www.pbs.orgCiphers: ECDHE-RSA-AES128-GCM-SHA256Issuer: /C-US/0=Let's Encrypt/CN=Let's Encrypt Authority X3
+ Start Time: 2018-12-05 23:34:06 (GMT-8)
------------------------------------------------------------------------------
+ Server: nginx
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-pbs-fwsrvname' found, with contents: fwcacheproxy1
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: https://www.pbs.org/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ RC-1918 IP address found in the 'x-pbs-appsvrip' header: The IP is "10.137.181.52".
+ Uncommon header 'x-cache-fs-status' found, with contents: EXPIRED
+ Uncommon header 'x-pbs-appsvrname' found, with contents: fwcacheproxy1
+ Uncommon header 'x-pbs-appsvrip' found, with contents: 10.137.181.52
+ Server leaks inodes via ETags, header found with file /pbs.org.zip, fields: 0x5b96537e 0x1678
+ 7446 requests: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2018-12-06 00:30:29 (GMT-8) (3383 seconds)
------------------------------------------------------------------------------
+ 1 host(s) tested可以看到有关于密码的一些有用信息以及服务器是Nginx等
五、扫描IP地址
ipcalc 192.168.0.48Address: 192.168.0.48 11000000.10101000.00000000. 00110000
Netmask: 255.255.255.0 = 24 11111111.11111111.11111111. 00000000
Wildcard: 0.0.0.255 00000000.00000000.00000000. 11111111
=>
Network: 192.168.0.0/24 11000000.10101000.00000000. 00000000
HostMin: 192.168.0.1 11000000.10101000.00000000. 00000001
HostMax: 192.168.0.254 11000000.10101000.00000000. 11111110
Broadcast: 192.168.0.255 11000000.10101000.00000000. 11111111
Hosts/Net: 254 Class C, Private Internet
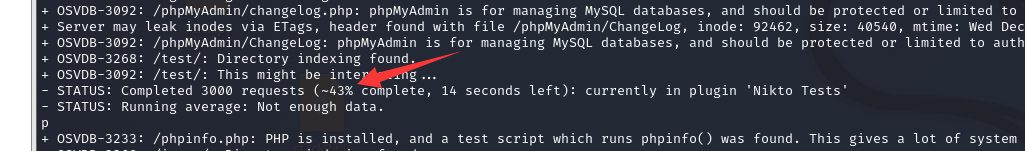
六、扫描HTTP网站
nikto -h www.afl.com.au- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 159.180.84.10
+ Target Hostname: www.afl.com.au
+ Target Port: 80
+ Start Time: 2018-12-05 21:48:32 (GMT-8)
---------------------------------------------------------------------------
+ Server: instart/nginx
+ Retried via header: 1.1 varnish (Varnish/6.1), 1.1 e9ba0a9a729ff2960a04323bf1833df8.cloudfront.net (CloudFront)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-cache' found, with contents: Miss from cloudfront
+ Uncommon header 'x-instart-cache-id' found, with contents: 17:12768802731504004780::1544075250
+ Uncommon header 'v-cache-hit' found, with contents: Hit
+ Uncommon header 'x-amz-cf-id' found, with contents: Dr-r6OwO5kk9ABt4ejzpc7R7AIF6SuH6kfJHQgP0v6xZoHwMLE55rQ==
+ Uncommon header 'x-instart-request-id' found, with contents: 12814413144077601501:BEQ01-CPVNPPRY18:1552504721:0
+ Uncommon header 'x-oneagent-js-injection' found, with contents: true
+ Uncommon header 'grace' found, with contents: cache
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Uncommon header 'x-ruxit-js-agent' found, with contents: true
+ Cookie dtCookie created without the httponly flag
+ Server banner has changed from 'instart/nginx' to 'nginx' which may suggest a WAF, load balancer or proxy is in place
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Entry '/sites/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/search/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '*.mobileapp' in robots.txt returned a non-forbidden or redirect HTTP code (400)
+ Entry '*.liveradio' in robots.txt returned a non-forbidden or redirect HTTP code (400)
+ Entry '*.smartmobile' in robots.txt returned a non-forbidden or redirect HTTP code (400)
+ Entry '*.responsive' in robots.txt returned a non-forbidden or redirect HTTP code (400)
+ Entry '/stats?*/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 8 entries which should be manually viewed.
+ OSVDB-3092: /sitemap.xml: This gives a nice listing of the site content.
+ OSVDB-3092: /psql_history: This might be interesting...
+ OSVDB-3092: /global/: This might be interesting...
+ OSVDB-3092: /home/: This might be interesting...
+ OSVDB-3092: /news: This might be interesting...
+ OSVDB-3092: /search.vts: This might be interesting...
+ OSVDB-3092: /stats.htm: This might be interesting...
+ OSVDB-3092: /stats.txt: This might be interesting...
+ OSVDB-3092: /stats/: This might be interesting...
+ OSVDB-3092: /Stats/: This might be interesting...
+ OSVDB-3093: /.wwwacl: Contains authorization information
+ OSVDB-3093: /.www_acl: Contains authorization information
+ OSVDB-3093: /.htpasswd: Contains authorization information
+ OSVDB-3093: /.access: Contains authorization information
+ OSVDB-3093: /.addressbook: PINE addressbook, may store sensitive e-mail address contact information and notes
+ OSVDB-3093: /.bashrc: User home dir was found with a shell rc file. This may reveal file and path information.
+ OSVDB-3093: /.bash_history: A user's home directory may be set to the web root, the shell history was retrieved. This should not be accessible via the web.
+ OSVDB-3093: /.forward: User home dir was found with a mail forward file. May reveal where the user's mail is being forwarded to.
+ OSVDB-3093: /.history: A user's home directory may be set to the web root, the shell history was retrieved. This should not be accessible via the web.
+ OSVDB-3093: /.htaccess: Contains configuration and/or authorization information
+ OSVDB-3093: /.lynx_cookies: User home dir found with LYNX cookie file. May reveal cookies received from arbitrary web sites.
+ OSVDB-3093: /.mysql_history: Database SQL?
+ OSVDB-3093: /.passwd: Contains authorization information
+ OSVDB-3093: /.pinerc: User home dir found with a PINE rc file. May reveal system information, directories and more.
+ OSVDB-3093: /.plan: User home dir with a .plan, a now mostly outdated file for delivering information via the finger protocol
+ OSVDB-3093: /.proclog: User home dir with a Procmail rc file. May reveal mail traffic, directories and more.
+ OSVDB-3093: /.procmailrc: User home dir with a Procmail rc file. May reveal subdirectories, mail contacts and more.
+ OSVDB-3093: /.profile: User home dir with a shell profile was found. May reveal directory information and system configuration.
+ OSVDB-3093: /.rhosts: A user's home directory may be set to the web root, a .rhosts file was retrieved. This should not be accessible via the web.
+ OSVDB-3093: /.sh_history: A user's home directory may be set to the web root, the shell history was retrieved. This should not be accessible via the web.
+ OSVDB-3093: /.ssh: A user's home directory may be set to the web root, an ssh file was retrieved. This should not be accessible via the web.
+ OSVDB-5709: /.nsconfig: Contains authorization information
+ /portal/changelog: Vignette richtext HTML editor changelog found.
+ 7587 requests: 4 error(s) and 55 item(s) reported on remote host
+ End Time: 2018-12-05 22:42:41 (GMT-8) (3249 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
七、与Metasploit配对扫描
Nikto可以将信息导出为Metasploit在执行扫描时可以读取的格式。只需使用上面的命令来执行扫描,但将-Format msf +附加到它的末尾。该格式可以帮助我们使用漏洞库快速配检索数据。
nikto -h <IP or hostname> -Format msf+
===========全文结束===========