本文链接:http://t.csdn.cn/BIGKc
SAML单点登录-spring-security-saml客户端SP
使用spring-security-saml搭建SAML协议的客户端,该依赖是spring框架的官方库,配置方便、文档详细。提供了包括单点登录、单点登出、获取sq元数据文件等接口,无需自己实现,参考:spring-security-saml与应用程序的集成
SpringBoot接入
Maven添加spring-security-saml依赖
pom配置:
注意:spring-security-saml2-core的1.0.4-1.0.10版本用的是opensaml-2.6.6版本,而当前阿里云maven库中没有opensaml-2.6.6版本,所以spring-security-saml2-core需引用1.0.4之前的版本(1.0.3),否则打包时,会报opensaml-2.6.6版本没找到。-当前时间:2022-07-07
阿里云maven公开库查找地址:https://developer.aliyun.com/
springboot-2.6.2引入spring-security-saml2-core不用引入xmltooling,否则会有版本冲突问题
<!--saml处理库--><dependency><groupId>org.opensaml</groupId><artifactId>xmltooling</artifactId><version>1.3.4</version></dependency><!--springboot saml--><dependency><groupId>org.springframework.security.extensions</groupId><artifactId>spring-security-saml2-core</artifactId><version>1.0.3.RELEASE</version></dependency>application.yml配置:
sp:# 认证中心服务信息 -> IDP元数据URLidpMetadataUrl: http://localhost:8080/gc-starter-ac/idp/metadata# entityId,服务提供商唯一标识entityId: cas:saml:sp:springboot# 是否签名断言,则需要在idp上传sp的证书/公钥文件以供解密wantAssertionSigned: false# 是否签名元数据signMetadata: false# 签名算法signAlg: http://www.w3.org/2001/04/xmldsig-more#rsa-sha256# 是否启用服务发现。一个sp可以配置多个idp,启动服务发现允许进入idp选择页面选择idp,如果不启用的话默认使用idp列表的第一个idpDiscoveryEnable: true# 服务发现选择页面路由IdpSelectionPath: /saml/discovery# idp登录成功后的重定向的页面路由,也就是首页路由successLoginUrl: /landing# idp登录失败后的重定向的页面路由failLoginUrl: /error# 登出成功后跳转的页面路由successLogoutUrl: /# 密钥库设置jks:# jks文件位置path: classpath:/saml/samlKeystore.jks# jks密码password: nalle123# 私钥别名defaultKey: apollo
映射配置到bean:
/*** @Description: sp配置* @Author: thp-mac* @Date: 2022/7/7* @Version: 1.0**/
@Data
@Component
@ConfigurationProperties(prefix = "sp")
public class SpConfig {private String idpMetadataUrl;private String entityId;private Boolean wantAssertionSigned;private Boolean signMetadata;private String signAlg;private Boolean idpDiscoveryEnable;private String IdpSelectionPath;private String successLoginUrl;private String failLoginUrl;private String successLogoutUrl;private JKS jks;@Datapublic class JKS {private String path;private String password;private String defaultKey;}}
准备登录成功后回调服务:
需要实现SAMLUserDetailsService
/*** @Description: saml登录成功会回调该服务,从samlCredential中获取idp返回的数据* @Author: thp-mac* @Date: 2022/7/7* @Version: 1.0**/
public class SAMLUserDetailsServiceImpl implements SAMLUserDetailsService {@Overridepublic Object loadUserBySAML(SAMLCredential samlCredential) throws UsernameNotFoundException {return samlCredential.getAttributes();}
}
SP拦截等配置:
/** Copyright 2021 Vincenzo De Notaris** Licensed under the Apache License, Version 2.0 (the "License");* you may not use this file except in compliance with the License.* You may obtain a copy of the License at** http://www.apache.org/licenses/LICENSE-2.0** Unless required by applicable law or agreed to in writing, software* distributed under the License is distributed on an "AS IS" BASIS,* WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.* See the License for the specific language governing permissions and* limitations under the License.*/import java.util.ArrayList;
import java.util.Collection;
import java.util.HashMap;
import java.util.List;
import java.util.Map;
import java.util.Timer;import org.apache.commons.httpclient.HttpClient;
import org.apache.commons.httpclient.MultiThreadedHttpConnectionManager;
import org.apache.velocity.app.VelocityEngine;
import org.opensaml.saml2.metadata.provider.HTTPMetadataProvider;
import org.opensaml.saml2.metadata.provider.MetadataProvider;
import org.opensaml.saml2.metadata.provider.MetadataProviderException;
import org.opensaml.xml.parse.ParserPool;
import org.opensaml.xml.parse.StaticBasicParserPool;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.beans.factory.annotation.Qualifier;
import org.springframework.beans.factory.DisposableBean;
import org.springframework.beans.factory.InitializingBean;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.core.io.DefaultResourceLoader;
import org.springframework.core.io.Resource;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.method.configuration.EnableGlobalMethodSecurity;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.saml.SAMLAuthenticationProvider;
import org.springframework.security.saml.SAMLBootstrap;
import org.springframework.security.saml.SAMLDiscovery;
import org.springframework.security.saml.SAMLEntryPoint;
import org.springframework.security.saml.SAMLLogoutFilter;
import org.springframework.security.saml.SAMLLogoutProcessingFilter;
import org.springframework.security.saml.SAMLProcessingFilter;
import org.springframework.security.saml.SAMLWebSSOHoKProcessingFilter;
import org.springframework.security.saml.context.SAMLContextProviderImpl;
import org.springframework.security.saml.key.JKSKeyManager;
import org.springframework.security.saml.key.KeyManager;
import org.springframework.security.saml.log.SAMLDefaultLogger;
import org.springframework.security.saml.metadata.CachingMetadataManager;
import org.springframework.security.saml.metadata.ExtendedMetadata;
import org.springframework.security.saml.metadata.ExtendedMetadataDelegate;
import org.springframework.security.saml.metadata.MetadataDisplayFilter;
import org.springframework.security.saml.metadata.MetadataGenerator;
import org.springframework.security.saml.metadata.MetadataGeneratorFilter;
import org.springframework.security.saml.parser.ParserPoolHolder;
import org.springframework.security.saml.processor.HTTPArtifactBinding;
import org.springframework.security.saml.processor.HTTPPAOS11Binding;
import org.springframework.security.saml.processor.HTTPPostBinding;
import org.springframework.security.saml.processor.HTTPRedirectDeflateBinding;
import org.springframework.security.saml.processor.HTTPSOAP11Binding;
import org.springframework.security.saml.processor.SAMLBinding;
import org.springframework.security.saml.processor.SAMLProcessorImpl;
import org.springframework.security.saml.util.VelocityFactory;
import org.springframework.security.saml.websso.ArtifactResolutionProfile;
import org.springframework.security.saml.websso.ArtifactResolutionProfileImpl;
import org.springframework.security.saml.websso.SingleLogoutProfile;
import org.springframework.security.saml.websso.SingleLogoutProfileImpl;
import org.springframework.security.saml.websso.WebSSOProfile;
import org.springframework.security.saml.websso.WebSSOProfileConsumer;
import org.springframework.security.saml.websso.WebSSOProfileConsumerHoKImpl;
import org.springframework.security.saml.websso.WebSSOProfileConsumerImpl;
import org.springframework.security.saml.websso.WebSSOProfileECPImpl;
import org.springframework.security.saml.websso.WebSSOProfileImpl;
import org.springframework.security.saml.websso.WebSSOProfileOptions;
import org.springframework.security.web.DefaultSecurityFilterChain;
import org.springframework.security.web.FilterChainProxy;
import org.springframework.security.web.SecurityFilterChain;
import org.springframework.security.web.access.channel.ChannelProcessingFilter;
import org.springframework.security.web.authentication.SavedRequestAwareAuthenticationSuccessHandler;
import org.springframework.security.web.authentication.SimpleUrlAuthenticationFailureHandler;
import org.springframework.security.web.authentication.logout.LogoutHandler;
import org.springframework.security.web.authentication.logout.SecurityContextLogoutHandler;
import org.springframework.security.web.authentication.logout.SimpleUrlLogoutSuccessHandler;
import org.springframework.security.web.authentication.www.BasicAuthenticationFilter;
import org.springframework.security.web.csrf.CsrfFilter;
import org.springframework.security.web.util.matcher.AntPathRequestMatcher;@Configuration
@EnableWebSecurity
@EnableGlobalMethodSecurity(securedEnabled = true)
public class WebSecurityConfig extends WebSecurityConfigurerAdapter implements InitializingBean, DisposableBean {@javax.annotation.Resourceprivate SpConfig spConfig;private Timer backgroundTaskTimer;private MultiThreadedHttpConnectionManager multiThreadedHttpConnectionManager;public void init() {this.backgroundTaskTimer = new Timer(true);this.multiThreadedHttpConnectionManager = new MultiThreadedHttpConnectionManager();}public void shutdown() {this.backgroundTaskTimer.purge();this.backgroundTaskTimer.cancel();this.multiThreadedHttpConnectionManager.shutdown();}@javax.annotation.Resourceprivate SAMLUserDetailsServiceImpl samlUserDetailsServiceImpl;// Initialization of the velocity engine@Beanpublic VelocityEngine velocityEngine() {return VelocityFactory.getEngine();}// XML parser pool needed for OpenSAML parsing@Bean(initMethod = "initialize")public StaticBasicParserPool parserPool() {return new StaticBasicParserPool();}@Bean(name = "parserPoolHolder")public ParserPoolHolder parserPoolHolder() {return new ParserPoolHolder();}// Bindings, encoders and decoders used for creating and parsing messages@Beanpublic HttpClient httpClient() {return new HttpClient(this.multiThreadedHttpConnectionManager);}// SAML Authentication Provider responsible for validating of received SAML// messages@Beanpublic SAMLAuthenticationProvider samlAuthenticationProvider() {SAMLAuthenticationProvider samlAuthenticationProvider = new SAMLAuthenticationProvider();samlAuthenticationProvider.setUserDetails(samlUserDetailsServiceImpl);samlAuthenticationProvider.setForcePrincipalAsString(false);return samlAuthenticationProvider;}// Provider of default SAML Context@Beanpublic SAMLContextProviderImpl contextProvider() {return new SAMLContextProviderImpl();}// Initialization of OpenSAML library@Beanpublic static SAMLBootstrap sAMLBootstrap() {return new SAMLBootstrap();}// Logger for SAML messages and events@Beanpublic SAMLDefaultLogger samlLogger() {return new SAMLDefaultLogger();}// SAML 2.0 WebSSO Assertion Consumer@Beanpublic WebSSOProfileConsumer webSSOprofileConsumer() {return new WebSSOProfileConsumerImpl();}// SAML 2.0 Holder-of-Key WebSSO Assertion Consumer@Beanpublic WebSSOProfileConsumerHoKImpl hokWebSSOprofileConsumer() {return new WebSSOProfileConsumerHoKImpl();}// SAML 2.0 Web SSO profile@Beanpublic WebSSOProfile webSSOprofile() {return new WebSSOProfileImpl();}// SAML 2.0 Holder-of-Key Web SSO profile@Beanpublic WebSSOProfileConsumerHoKImpl hokWebSSOProfile() {return new WebSSOProfileConsumerHoKImpl();}// SAML 2.0 ECP profile@Beanpublic WebSSOProfileECPImpl ecpprofile() {return new WebSSOProfileECPImpl();}@Beanpublic SingleLogoutProfile logoutprofile() {return new SingleLogoutProfileImpl();}// sp密钥库// Central storage of cryptographic keys@Beanpublic KeyManager keyManager() {DefaultResourceLoader loader = new DefaultResourceLoader();Resource storeFile = loader.getResource(spConfig.getJks().getPath());String storePass = spConfig.getJks().getPassword();Map<String, String> passwords = new HashMap<String, String>();passwords.put(spConfig.getJks().getDefaultKey(), spConfig.getJks().getPassword());String defaultKey = spConfig.getJks().getDefaultKey();return new JKSKeyManager(storeFile, storePass, passwords, defaultKey);}@Beanpublic WebSSOProfileOptions defaultWebSSOProfileOptions() {WebSSOProfileOptions webSSOProfileOptions = new WebSSOProfileOptions();webSSOProfileOptions.setIncludeScoping(false);return webSSOProfileOptions;}// Entry point to initialize authentication, default values taken from// properties file@Beanpublic SAMLEntryPoint samlEntryPoint() {SAMLEntryPoint samlEntryPoint = new SAMLEntryPoint();samlEntryPoint.setDefaultProfileOptions(defaultWebSSOProfileOptions());return samlEntryPoint;}// 扩展元数据// Setup advanced info about metadata@Beanpublic ExtendedMetadata extendedMetadata() {ExtendedMetadata extendedMetadata = new ExtendedMetadata();extendedMetadata.setIdpDiscoveryEnabled(spConfig.getIdpDiscoveryEnable());extendedMetadata.setSigningAlgorithm(spConfig.getSignAlg());extendedMetadata.setSignMetadata(spConfig.getSignMetadata());extendedMetadata.setEcpEnabled(true);return extendedMetadata;}// 服务发现页面地址// IDP Discovery Service@Beanpublic SAMLDiscovery samlIDPDiscovery() {SAMLDiscovery idpDiscovery = new SAMLDiscovery();idpDiscovery.setIdpSelectionPath(spConfig.getIdpSelectionPath());return idpDiscovery;}@Bean@Qualifier("idp-ssocircle")public ExtendedMetadataDelegate ssoCircleExtendedMetadataProvider()throws MetadataProviderException {String idpSSOCircleMetadataURL = spConfig.getIdpMetadataUrl();HTTPMetadataProvider httpMetadataProvider = new HTTPMetadataProvider(this.backgroundTaskTimer, httpClient(), idpSSOCircleMetadataURL);httpMetadataProvider.setParserPool(parserPool());ExtendedMetadataDelegate extendedMetadataDelegate =new ExtendedMetadataDelegate(httpMetadataProvider, extendedMetadata());extendedMetadataDelegate.setMetadataTrustCheck(false);extendedMetadataDelegate.setMetadataRequireSignature(false);backgroundTaskTimer.purge();return extendedMetadataDelegate;}// IDP Metadata configuration - paths to metadata of IDPs in circle of trust// is here// Do no forget to call iniitalize method on providers@Bean@Qualifier("metadata")public CachingMetadataManager metadata() throws MetadataProviderException {List<MetadataProvider> providers = new ArrayList<MetadataProvider>();providers.add(ssoCircleExtendedMetadataProvider());return new CachingMetadataManager(providers);}// 元数据生成bean// Filter automatically generates default SP metadata@Beanpublic MetadataGenerator metadataGenerator() {MetadataGenerator metadataGenerator = new MetadataGenerator();metadataGenerator.setEntityId(spConfig.getEntityId());metadataGenerator.setExtendedMetadata(extendedMetadata());metadataGenerator.setIncludeDiscoveryExtension(false);metadataGenerator.setKeyManager(keyManager());metadataGenerator.setWantAssertionSigned(spConfig.getWantAssertionSigned());return metadataGenerator;}// The filter is waiting for connections on URL suffixed with filterSuffix// and presents SP metadata there@Beanpublic MetadataDisplayFilter metadataDisplayFilter() {return new MetadataDisplayFilter();}// 设置登陆成功后的重定向地址,或者说是首页地址// Handler deciding where to redirect user after successful login@Beanpublic SavedRequestAwareAuthenticationSuccessHandler successRedirectHandler() {SavedRequestAwareAuthenticationSuccessHandler successRedirectHandler =new SavedRequestAwareAuthenticationSuccessHandler();successRedirectHandler.setDefaultTargetUrl(spConfig.getSuccessLoginUrl());return successRedirectHandler;}// Handler deciding where to redirect user after failed login@Beanpublic SimpleUrlAuthenticationFailureHandler authenticationFailureHandler() {SimpleUrlAuthenticationFailureHandler failureHandler =new SimpleUrlAuthenticationFailureHandler();failureHandler.setUseForward(true);failureHandler.setDefaultFailureUrl(spConfig.getFailLoginUrl());return failureHandler;}@Beanpublic SAMLWebSSOHoKProcessingFilter samlWebSSOHoKProcessingFilter() throws Exception {SAMLWebSSOHoKProcessingFilter samlWebSSOHoKProcessingFilter = new SAMLWebSSOHoKProcessingFilter();samlWebSSOHoKProcessingFilter.setAuthenticationSuccessHandler(successRedirectHandler());samlWebSSOHoKProcessingFilter.setAuthenticationManager(authenticationManager());samlWebSSOHoKProcessingFilter.setAuthenticationFailureHandler(authenticationFailureHandler());return samlWebSSOHoKProcessingFilter;}// Processing filter for WebSSO profile messages@Beanpublic SAMLProcessingFilter samlWebSSOProcessingFilter() throws Exception {SAMLProcessingFilter samlWebSSOProcessingFilter = new SAMLProcessingFilter();samlWebSSOProcessingFilter.setAuthenticationManager(authenticationManager());samlWebSSOProcessingFilter.setAuthenticationSuccessHandler(successRedirectHandler());samlWebSSOProcessingFilter.setAuthenticationFailureHandler(authenticationFailureHandler());return samlWebSSOProcessingFilter;}@Beanpublic MetadataGeneratorFilter metadataGeneratorFilter() {return new MetadataGeneratorFilter(metadataGenerator());}// Handler for successful logout@Beanpublic SimpleUrlLogoutSuccessHandler successLogoutHandler() {SimpleUrlLogoutSuccessHandler successLogoutHandler = new SimpleUrlLogoutSuccessHandler();successLogoutHandler.setDefaultTargetUrl(spConfig.getSuccessLogoutUrl());return successLogoutHandler;}// Logout handler terminating local session@Beanpublic SecurityContextLogoutHandler logoutHandler() {SecurityContextLogoutHandler logoutHandler =new SecurityContextLogoutHandler();logoutHandler.setInvalidateHttpSession(true);logoutHandler.setClearAuthentication(true);return logoutHandler;}// Filter processing incoming logout messages// First argument determines URL user will be redirected to after successful// global logout@Beanpublic SAMLLogoutProcessingFilter samlLogoutProcessingFilter() {return new SAMLLogoutProcessingFilter(successLogoutHandler(),logoutHandler());}// Overrides default logout processing filter with the one processing SAML// messages@Beanpublic SAMLLogoutFilter samlLogoutFilter() {return new SAMLLogoutFilter(successLogoutHandler(),new LogoutHandler[]{logoutHandler()},new LogoutHandler[]{logoutHandler()});}// Bindingsprivate ArtifactResolutionProfile artifactResolutionProfile() {final ArtifactResolutionProfileImpl artifactResolutionProfile =new ArtifactResolutionProfileImpl(httpClient());artifactResolutionProfile.setProcessor(new SAMLProcessorImpl(soapBinding()));return artifactResolutionProfile;}@Beanpublic HTTPArtifactBinding artifactBinding(ParserPool parserPool, VelocityEngine velocityEngine) {return new HTTPArtifactBinding(parserPool, velocityEngine, artifactResolutionProfile());}@Beanpublic HTTPSOAP11Binding soapBinding() {return new HTTPSOAP11Binding(parserPool());}@Beanpublic HTTPPostBinding httpPostBinding() {return new HTTPPostBinding(parserPool(), velocityEngine());}@Beanpublic HTTPRedirectDeflateBinding httpRedirectDeflateBinding() {return new HTTPRedirectDeflateBinding(parserPool());}@Beanpublic HTTPSOAP11Binding httpSOAP11Binding() {return new HTTPSOAP11Binding(parserPool());}@Beanpublic HTTPPAOS11Binding httpPAOS11Binding() {return new HTTPPAOS11Binding(parserPool());}// Processor@Beanpublic SAMLProcessorImpl processor() {Collection<SAMLBinding> bindings = new ArrayList<SAMLBinding>();bindings.add(httpRedirectDeflateBinding());bindings.add(httpPostBinding());bindings.add(artifactBinding(parserPool(), velocityEngine()));bindings.add(httpSOAP11Binding());bindings.add(httpPAOS11Binding());return new SAMLProcessorImpl(bindings);}/*** Define the security filter chain in order to support SSO Auth by using SAML 2.0** @return Filter chain proxy* @throws Exception*/@Beanpublic FilterChainProxy samlFilter() throws Exception {List<SecurityFilterChain> chains = new ArrayList<SecurityFilterChain>();chains.add(new DefaultSecurityFilterChain(new AntPathRequestMatcher("/saml/login/**"),samlEntryPoint()));chains.add(new DefaultSecurityFilterChain(new AntPathRequestMatcher("/saml/logout/**"),samlLogoutFilter()));chains.add(new DefaultSecurityFilterChain(new AntPathRequestMatcher("/saml/metadata/**"),metadataDisplayFilter()));chains.add(new DefaultSecurityFilterChain(new AntPathRequestMatcher("/saml/SSO/**"),samlWebSSOProcessingFilter()));chains.add(new DefaultSecurityFilterChain(new AntPathRequestMatcher("/saml/SSOHoK/**"),samlWebSSOHoKProcessingFilter()));chains.add(new DefaultSecurityFilterChain(new AntPathRequestMatcher("/saml/SingleLogout/**"),samlLogoutProcessingFilter()));chains.add(new DefaultSecurityFilterChain(new AntPathRequestMatcher("/saml/discovery/**"),samlIDPDiscovery()));return new FilterChainProxy(chains);}/*** Returns the authentication manager currently used by Spring.* It represents a bean definition with the aim allow wiring from* other classes performing the Inversion of Control (IoC).** @throws Exception*/@Bean@Overridepublic AuthenticationManager authenticationManagerBean() throws Exception {return super.authenticationManagerBean();}/*** Defines the web based security configuration.** @param http It allows configuring web based security for specific http requests.* @throws Exception*/@Overrideprotected void configure(HttpSecurity http) throws Exception {http.httpBasic().authenticationEntryPoint(samlEntryPoint());http.addFilterBefore(metadataGeneratorFilter(), ChannelProcessingFilter.class).addFilterAfter(samlFilter(), BasicAuthenticationFilter.class).addFilterBefore(samlFilter(), CsrfFilter.class);http.authorizeRequests().antMatchers("/").permitAll().antMatchers("/saml/**").permitAll().antMatchers("/css/**").permitAll().antMatchers("/img/**").permitAll().antMatchers("/js/**").permitAll().anyRequest().authenticated();http.logout().disable(); // The logout procedure is already handled by SAML filters.}/*** Sets a custom authentication provider.** @param auth SecurityBuilder used to create an AuthenticationManager.* @throws Exception*/@Overrideprotected void configure(AuthenticationManagerBuilder auth) throws Exception {auth.authenticationProvider(samlAuthenticationProvider());}@Overridepublic void afterPropertiesSet() throws Exception {init();}@Overridepublic void destroy() throws Exception {shutdown();}
}
生成密钥库jks文件
SAML客户端在发送SAML请求时需要进行加密和签名,这就需要密钥,上面配置文件中也有需要去配置jks。jks即密钥库(Java Key Store),里面包含多个公钥和私钥,也可以将认证中心的公钥放入其中,进行解密和验签。这里介绍如何使用jdk的keytool工具生成私钥和自签名证书。
生成密钥库,密钥库包含了公钥和私钥(别名,alias自行更改)
keytool -genkeypair -alias qianxing -keyalg RSA -keystore samlKeystore.jks
生成公钥,IDP解密时需要使用
keytool -alias qianxing -exportcert -keystore samlKeystore.jks -file public.cer
根据jks生成私钥
keytool -v -importkeystore -srckeystore samlKeystore.jks -srcstoretype jks -destkeystore qianxing.pfx -deststoretype pkcs12
openssl pkcs12 -in qianxing.pfx -nocerts -nodes -out private.key
工程中classpath下创建一个saml目录,将samlKeystore.jks放入其中
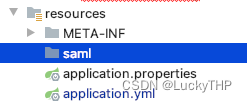
sp常用API:
获取sp元数据:http://ip:port/cotext-path/saml/metadata
可能存在问题:
springboot-2.6以后默认禁止循环依赖,若不开启会出现samlEntryPoint与samlIDPDiscovery循环依赖问题
解决:
application.yml中添加配置:
spring:main:#开启循环依赖allow-circular-references: true
application.properties中的写法:
spring.main.allow-circular-references = true
本文链接:http://t.csdn.cn/BIGKc
在博客:https://blog.csdn.net/zhitianming/article/details/122824124的基础上整理补充