前言
这里常用的方法就不说了,#{}预编译不说,但是如果我们不得不用${}来传递参数,那就有点麻烦了,另外,一般我们会用到druid自带的sql注入过滤:
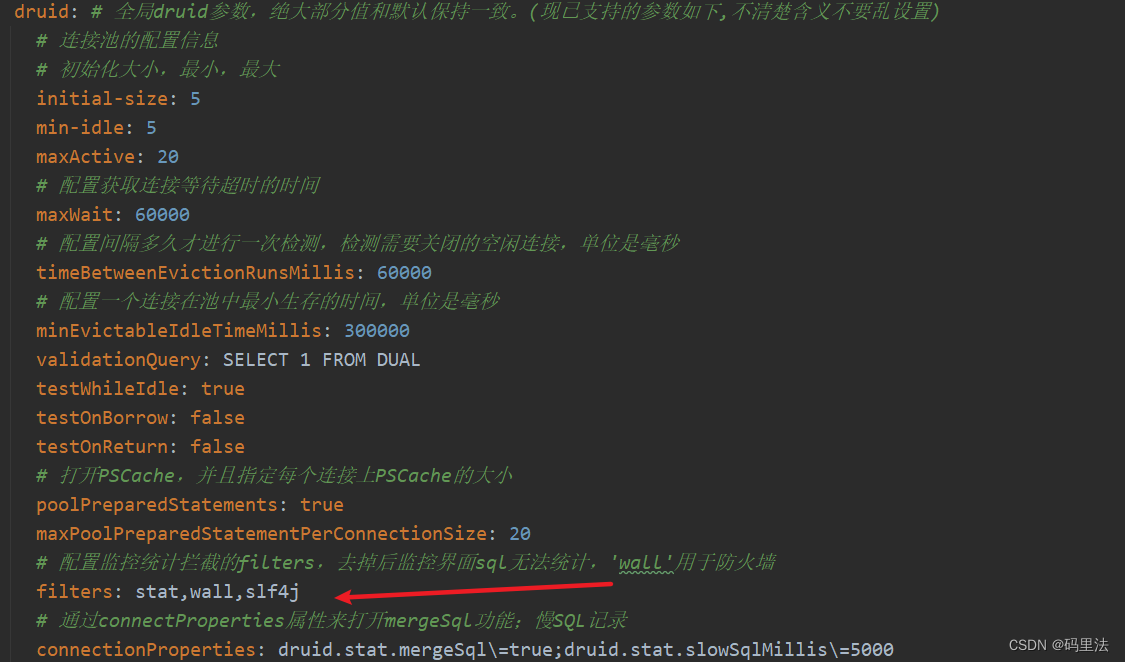
但是经过测试发现,这个方法并不能完全屏宾sql注入,比如:
select * from user where state=${state}
state传递 1 or state=2 这样就能跳过druid的检查
所以,还是需要我们自己自定义过滤拦截。
自定义拦截器
/*** 防止SQL注入的拦截器** @author scott* @time 2018-05-21*/
@Slf4j
public class SqlInjectInterceptor implements HandlerInterceptor {@Override public void afterCompletion(HttpServletRequest request, HttpServletResponse response, Object arg2, Exception arg3) throws Exception { // TODO Auto-generated method stub } @Override public void postHandle(HttpServletRequest request, HttpServletResponse response, Object arg2, ModelAndView arg3) throws Exception { // TODO Auto-generated method stub } @Override public boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object arg2) throws Exception {//常规业务操作(无SQL值情况), 针对数据库SQL操作,进行开发者权限控制,防止SQL注入Enumeration<String> names = request.getParameterNames(); while(names.hasMoreElements()){ String name = names.nextElement(); String[] values = request.getParameterValues(name); for(String value: values){//sql注入直接拦截if(judgeSQLInject(value.toLowerCase())){log.info("-----------Sql注入拦截-----------name: "+name+" -------------value:"+ value);response.setContentType("text/html;charset=UTF-8"); response.getWriter().print("参数含有非法攻击字符,已禁止继续访问!"); return false; }//跨站xss清理clearXss(value);} } return true; } /** * 判断参数是否含有攻击串 * @param value * @return */ public boolean judgeSQLInject(String value){if(value == null || "".equals(value)){ return false; } String xssStr = "and |or |select |update |delete |drop |truncate |%20|=|--|!="; String[] xssArr = xssStr.split("\\|"); for(int i=0;i<xssArr.length;i++){ if(value.indexOf(xssArr[i])>-1){ return true; } } return false; }/*** 处理跨站xss字符转义** @param value* @return*/private String clearXss(String value) {log.debug("----before--------处理跨站xss字符转义----------"+ value);if (value == null || "".equals(value)) {return value;}value = value.replaceAll("<", "<").replaceAll(">", ">");value = value.replaceAll("\\(", "(").replace("\\)", ")");value = value.replaceAll("'", "'");value = value.replaceAll("eval\\((.*)\\)", "");value = value.replaceAll("[\\\"\\\'][\\s]*javascript:(.*)[\\\"\\\']","\"\"");value = value.replace("script", "");//为了用户密码安全,禁止列表查询展示用户密码----------value = value.replace(",password","").replace("password","");log.debug("----end--------处理跨站xss字符转义----------"+ value);return value;}
}
@Configuration
public class WebMvcConfiguration implements WebMvcConfigurer @Beanpublic SqlInjectInterceptor sqlInjectInterceptor(){return new SqlInjectInterceptor();}@Overridepublic void addInterceptors(InterceptorRegistry registry) {registry.addInterceptor(sqlInjectInterceptor()).addPathPatterns("/**");}
}ok,这样就差不多了,欢迎指正